Key Takeaways
- Broken CI builds slow teams down, waste developer time, and create release risk, especially during the pre-merge phase of the pipeline.
- Standardizing linting, formatting, and test strategies prevents many trivial failures before they reach production and keeps review cycles focused on real logic.
- Automated quality gates and AI-driven root cause analysis make it easier to detect, understand, and prevent misconfigurations and recurring CI failures.
- Autonomous CI agents can read logs, generate fixes, validate them in the real CI environment, and commit changes back to pull requests with minimal developer intervention.
- Teams that want to automatically fix broken builds and protect developer flow can install Gitar as an autonomous CI fixer by visiting https://gitar.ai/fix.
The High Cost of Broken Builds: Why Self-Healing CI Matters
Broken CI builds create a major productivity bottleneck for engineering teams. The pre-merge CI/CD phase has a significantly higher job failure rate and more jobs per check than post-merge, which directly affects developer productivity and experience. Many teams see developers lose a large share of their time to CI and code review issues, which delays releases and increases operational costs.
This impact extends beyond inconvenience. Developers feel productivity bottlenecks most during pre-merge, where job failures, long wait times, and time-consuming debugging are common, and for a mid-sized engineering team this can add up to large annual productivity losses. Improving pre-merge performance by reducing failures or increasing efficiency often produces more immediate gains in developer experience than post-merge optimization. Self-healing CI aims to reduce this reactive work so developers can focus on feature delivery.
Streamline Your CI with Gitar: An Autonomous Fixer
Gitar operates as an autonomous CI fixer that focuses on resolving failures, not just pointing them out. The system runs against real CI environments so proposed fixes respect your dependencies, SDKs, and existing tools.
Key capabilities include:
- End-to-end fixing: Applies and validates fixes against the full CI workflow so pull requests move back to a passing state.
- Full environment replication: Supports complex CI setups with specific dependencies, SDKs, and tools such as SonarQube, Snyk, and snapshot testing frameworks.
- Configurable trust model: Lets teams start with suggestion-only changes, then move toward auto-commit with rollback as confidence grows.
- Intelligent code review assistant: Implements review feedback directly in code rather than only surfacing comments.
- Cross-platform support: Works with GitHub Actions, GitLab CI, CircleCI, BuildKite, and other common CI platforms.
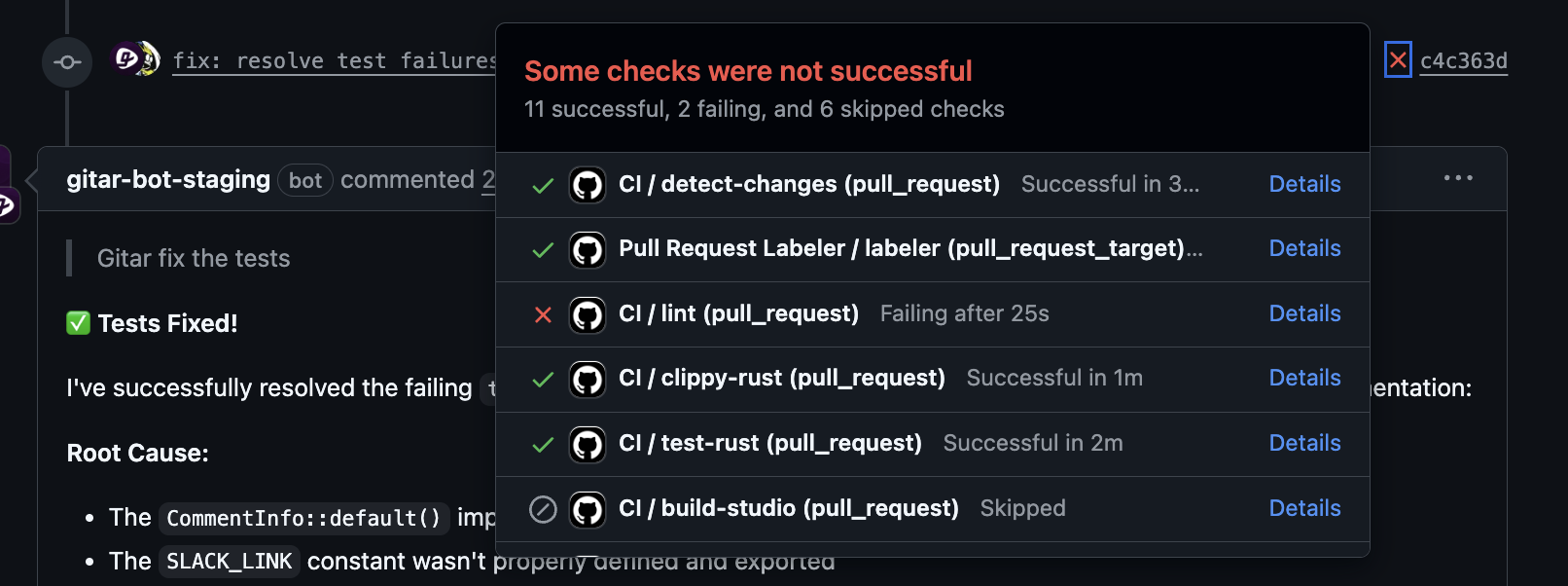
Install Gitar to automatically fix broken builds and keep pull requests moving.
#1: Use Advanced Linting and Formatting Automation Early
Enforcing consistent code style before review removes many low-value interruptions. Tools like ESLint, Black, and Prettier keep syntax and formatting consistent across the codebase so reviewers can focus on logic, not spacing or style. Breaking large, monolithic pipelines into smaller stages also reduces cascading failures and supports more frequent, focused commits.
Teams see the best results when they add linting and formatting checks as pre-commit hooks or in the earliest CI stages and enable auto-fix where possible. Traditional tools fix formatting but stop at that boundary. Gitar extends this approach by reading lint failures in CI logs, generating code changes that address them, and committing updates back to the pull request branch. This reduces context switching and keeps developers in their primary workflow.
#2: Automate Test Failure Remediation for Flaky and Simple Errors
Test flakiness and simple unit or integration failures account for a large portion of CI problems. Flaky tests and intermittent failures contribute heavily to CI/CD job failures, yet many follow patterns that automation can detect and resolve. Common examples include outdated snapshots, minor assertion mismatches, and time-dependent tests.
Healthy test strategies use isolation and reliable dependency management. Running heavy end-to-end tests on every commit increases pipeline time and brittleness, while selective execution strategies improve efficiency. Frameworks like Cypress and Jest support retries and custom handling for flaky tests. For failures that follow predictable paths, Gitar analyzes logs, identifies root causes, proposes code fixes, runs the pipeline again, and commits changes so developers do not need to babysit failing builds.
#3: Enforce CI Quality Gates and Configuration Validation
Many failures arise from misconfigured pipelines, not application logic. Missing CI/CD quality gates often allow malformed Kubernetes manifests, mismatched environment settings, version drift, risky rollouts, missing tests, and weak secret handling to pass unchecked. These issues reach later stages where they are slower and more expensive to fix.
Quality gates can include schema validation for Kubernetes YAML, dependency auditing with tools like Renovate, and static analysis using platforms such as SonarQube and Snyk. Inconsistent environments across development, staging, and production drive test flakiness and deployment failures, so infrastructure as code deserves the same rigor as application code. Strong validation at this layer reduces avoidable configuration-related build breaks.
#4: Apply AI for Root Cause Analysis and Failure Prediction
AI can process large volumes of logs and metrics faster than manual review, which shortens the feedback loop when builds fail. AI-based tools now help teams diagnose and resolve broken CI/CD pipelines by correlating signals across stages and services, surfacing likely causes with clear context.
Frequent pipeline failures include syntax errors, failed tests caused by dependency mismatches, and incorrect pipeline or environment configuration. AI log analysis and anomaly detection highlight these issues earlier, while prediction models can flag patterns that tend to produce failures before they reach production. Clear logging and defined ownership for each pipeline stage already help teams resolve failures faster, and AI builds on that foundation by compressing the time from first red build to verified fix.
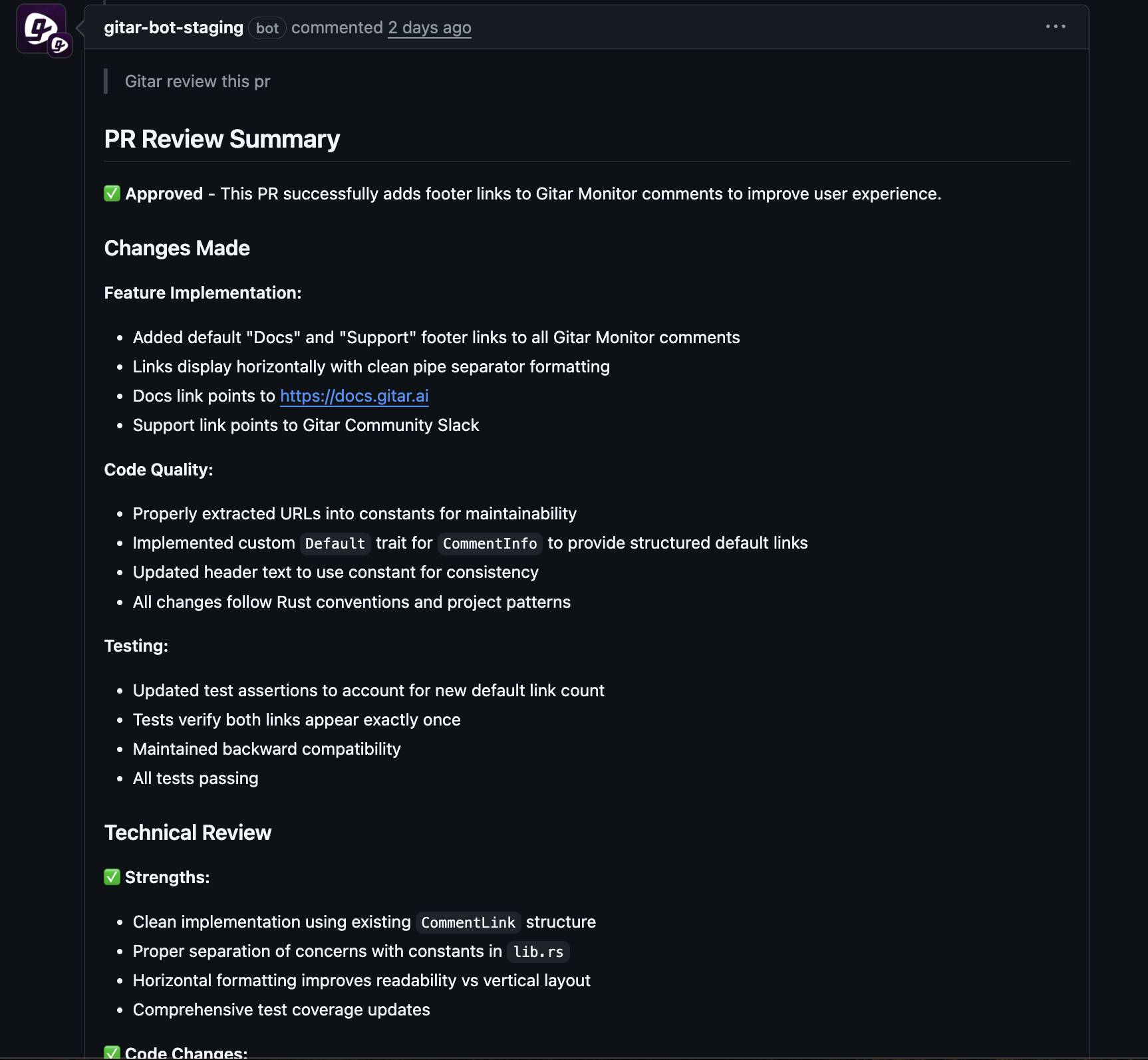
#5: Use Autonomous Agents for End-to-End Build Healing
CI workflows now increasingly rely on autonomous agents that not only detect issues but also apply and validate fixes. These agents aim to function as healing engines, closing the loop from failure detection through code change and CI validation without manual steps in the middle.
Effective agents must understand the build environment, interpret code diffs and pipeline logs, generate suitable code changes, and re-run CI to confirm success. Teams with limited visibility into CI failures struggle to identify causes quickly, especially across time zones. Gitar addresses this by monitoring CI, identifying whether failures stem from linting, tests, or dependencies, and then committing fixes directly to pull requests. This reduces the context switching tax that usually accompanies manual debugging.
Autonomous vs. Traditional CI Fixes: A Comparison
|
Feature |
Manual Debugging |
AI Suggestion Engines |
Gitar: Autonomous CI Healing |
|
Problem Identification |
Developer |
Automated |
Automated |
|
Fix Generation |
Developer |
AI-Assisted |
AI-Driven (Autonomous) |
|
Validation |
Developer |
Manual |
Automated (Full CI Run) |
|
Context Switching |
High |
Moderate |
Low / None |
Frequently Asked Questions (FAQ) about Autonomous Tools for Fixing Broken Builds
How does an autonomous CI fixer handle complex enterprise environments?
Autonomous fixers like Gitar replicate full workflows, including specific JDK versions, multiple SDKs, and integrations with tools such as SonarQube and Snyk. This alignment with the real CI environment helps ensure generated fixes are reliable for your setup.
What if I do not want automated tools to merge fixes directly?
Teams can configure Gitar in a conservative mode where it posts suggestions that developers accept manually. As trust grows, teams can enable more automated modes that commit fixes directly while still keeping rollback options available.
How are autonomous CI fixers different from AI code review or suggestion tools?
AI code review tools focus on suggestions that require developers to write or apply changes. Autonomous fixers like Gitar take responsibility for generating code, running CI again, and confirming that checks pass before a pull request returns to a green state.
Can these tools help distributed teams resolve CI issues faster?
Autonomous CI fixers support distributed teams by resolving failures between working hours. A reviewer can leave a comment for Gitar, and the agent can deliver a passing build before the next workday begins for teammates in another time zone.
What types of CI failures can autonomous tools fix today?
Autonomous tools like Gitar can handle lint and formatting violations, many simple unit and integration test failures, selected build script issues, and common dependency errors. The tool generates, tests, and applies fixes without requiring manual intervention for each failure.
Conclusion: Move Toward Self-Healing CI and Better Developer Flow
CI pipelines that rely only on manual debugging interrupt developer focus and slow delivery. The strategies in this article, from linting automation and stronger quality gates to AI analysis and autonomous agents, reduce this friction and help keep builds healthy.
The benefits appear at both team and organization levels. Teams with faster pipelines deploy more frequently, and higher deployment frequency correlates with stronger software quality. Self-healing CI moves work away from repetitive troubleshooting and toward building features. Teams that want this operating model can start by installing Gitar to automatically fix broken builds in their existing CI pipelines.
