Key Takeaways
- Modern attacks in 2026 target backups, identities, and supply chains, which makes reactive security alone insufficient for protecting software delivery.
- Shift Left Security catches vulnerabilities earlier in the SDLC, lowers remediation costs, and reduces production incidents without slowing developers.
- Automation and AI improve coverage and consistency across CI/CD pipelines, especially for large codebases and complex dependency graphs.
- Security maturity assessments, clear ownership, and awareness of SaaS and shadow IT risks help leaders prioritize the most effective improvements.
- Gitar adds autonomous CI fixing to existing pipelines, reducing broken builds and manual rework while keeping developers focused on higher-value work. See how Gitar can automatically fix your CI failures.
The Evolving Threat Landscape: Why Traditional Security Fails in 2026
The Cost of Inaction: Exploding Vulnerabilities
Ransomware attacks in 2025 increasingly targeted backup systems first to delete or encrypt them before detonation, which showed how quickly attacker tactics evolved beyond perimeter defenses. Mass exploitation of enterprise platforms, such as Oracle E-Business Suite zero-days, enabled extortion without encryption and exposed gaps in patching and monitoring. Identity-led ransomware abused valid credentials for lateral movement, which highlighted the need for stronger identity controls and segmentation from the earliest design stages.
Unpatched software, misconfigured systems, and edge device vulnerabilities remained consistent targets, with more than 84,000 attack alerts observed on edge devices since January 2024. These trends showed that attackers could exploit weaknesses faster than manual patching and review cycles, so teams needed continuous, automated defenses embedded into development workflows.
SaaS and Supply Chain: New Attack Vectors
SaaS vulnerabilities rose 65% since 2024 as rapid AI adoption expanded data flows and integration points. Security teams often had visibility into less than 30% of the 1,400 or more cloud services in use, which allowed shadow IT and unmanaged data access to grow unchecked.
Excessive permissions affected most SaaS users and widened the blast radius of any compromise. Supply-chain incidents, including breaches of Salesforce environments through third-party compromises, demonstrated how a single weak integration could impact an entire ecosystem. Secure development in 2026 therefore needed strong dependency management, vendor risk controls, and aligned security practices across partners.
The Benefits of Proactive, Modern Security
A Shift Left approach embeds security into planning, coding, and testing so teams discover issues before production. Fixing defects in early stages costs far less than emergency patching in live environments and reduces downtime, fines, and reputational impact. This approach also improves developer productivity, since fewer last-minute tickets and escalations interrupt work, and security becomes part of normal engineering practice rather than a late-stage blocker.
Fundamentals of Shift Left Security: Integrating Protection from the Start
Core Principles of Shifting Left
Security by design treats security requirements as core architecture constraints, not add-ons. Teams capture data flows, trust boundaries, and access needs early so that controls such as encryption, least privilege, and logging fit naturally into the system.
Developer-centric security supports engineers with practical guardrails. Integrated security checks in IDEs and CI, clear coding guidelines, and quick feedback on common issues, such as injection or insecure configuration, help developers fix problems as they write code.
Automated security testing uses SAST, DAST, software composition analysis, and infrastructure as code scanning in pipelines. Continuous feedback then returns specific, actionable findings to the developer who introduced the change, which reduces context switching and delays.
Threat modeling workshops and lightweight reviews identify likely attack paths and abuse cases. These exercises give teams a shared view of risk, which guides where to focus automated tests, monitoring, and manual review.
Implementing Shift Left: Key Practices
Teams can wire security checks into CI/CD so every merge request triggers consistent tests and policy checks. Security training that focuses on the tech stack and real code examples helps engineers recognize patterns they see daily. Standardized policies, encoded as automated gates, apply the same rules to all services and reduce reliance on memory or manual checklists.
The Role of Automation and AI in 2026 Software Development Security
Limitations of Manual Security Workflows
Manual review alone cannot keep up with frequent releases, microservices, and expanding dependency trees. Security teams that rely on one-off audits or ticket-driven reviews often become bottlenecks and still miss issues in less visible components. Inconsistent enforcement and human error create gaps that skilled attackers can exploit.
Scaling manual triage and remediation also raises costs and slows delivery. Many organizations in 2026 look for ways to move repetitive, pattern-based security work to automated systems so specialists can focus on higher-risk analysis and architectural decisions.
Leveraging AI for Proactive Defense
AI-powered code analysis can highlight insecure patterns, dangerous combinations of configuration, and unusual data flows faster than traditional rule-based tools. This coverage is especially useful in large monorepos and polyglot environments.
Autonomous vulnerability remediation extends this capability by generating and testing candidate fixes. Predictive models that monitor threat intelligence and code changes help teams anticipate emerging techniques and tune rules before incidents occur.
Automated policy enforcement applies secure defaults across repositories, pipelines, and environments. This consistency reduces drift between services and simplifies audits. Teams can also add AI agents that fix CI failures automatically to close the loop between detection and remediation.
Gitar: Enhancing CI/CD Pipelines with Autonomous AI
Gitar’s Autonomous Approach to CI Fixes
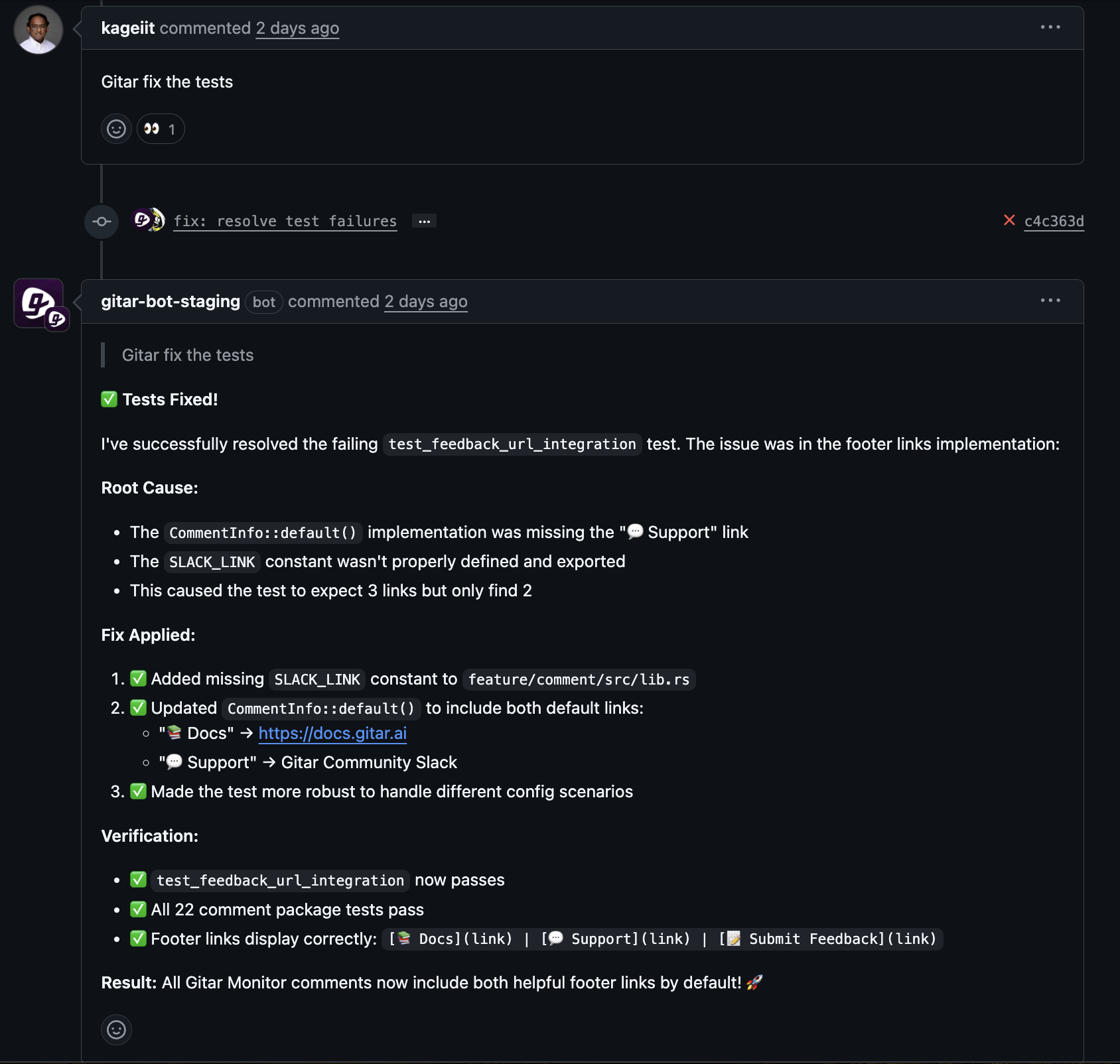
Gitar is an autonomous AI agent that resolves CI pipeline failures and code review feedback with awareness of the full environment. The system inspects failing runs, understands logs and context, generates code changes, and updates pull or merge requests. This approach removes a large class of repetitive fixes from developer backlogs.
How Gitar Supports Development Workflows
Automated CI fixes from Gitar address linting errors, test failures, and build issues that block merges. The agent commits changes that pass CI, which keeps branches moving and prevents minor problems from piling up.
As a code review assistant, Gitar can respond to reviewer comments by proposing or applying edits that match the feedback. This approach reduces back-and-forth cycles while maintaining human approval on important design choices.
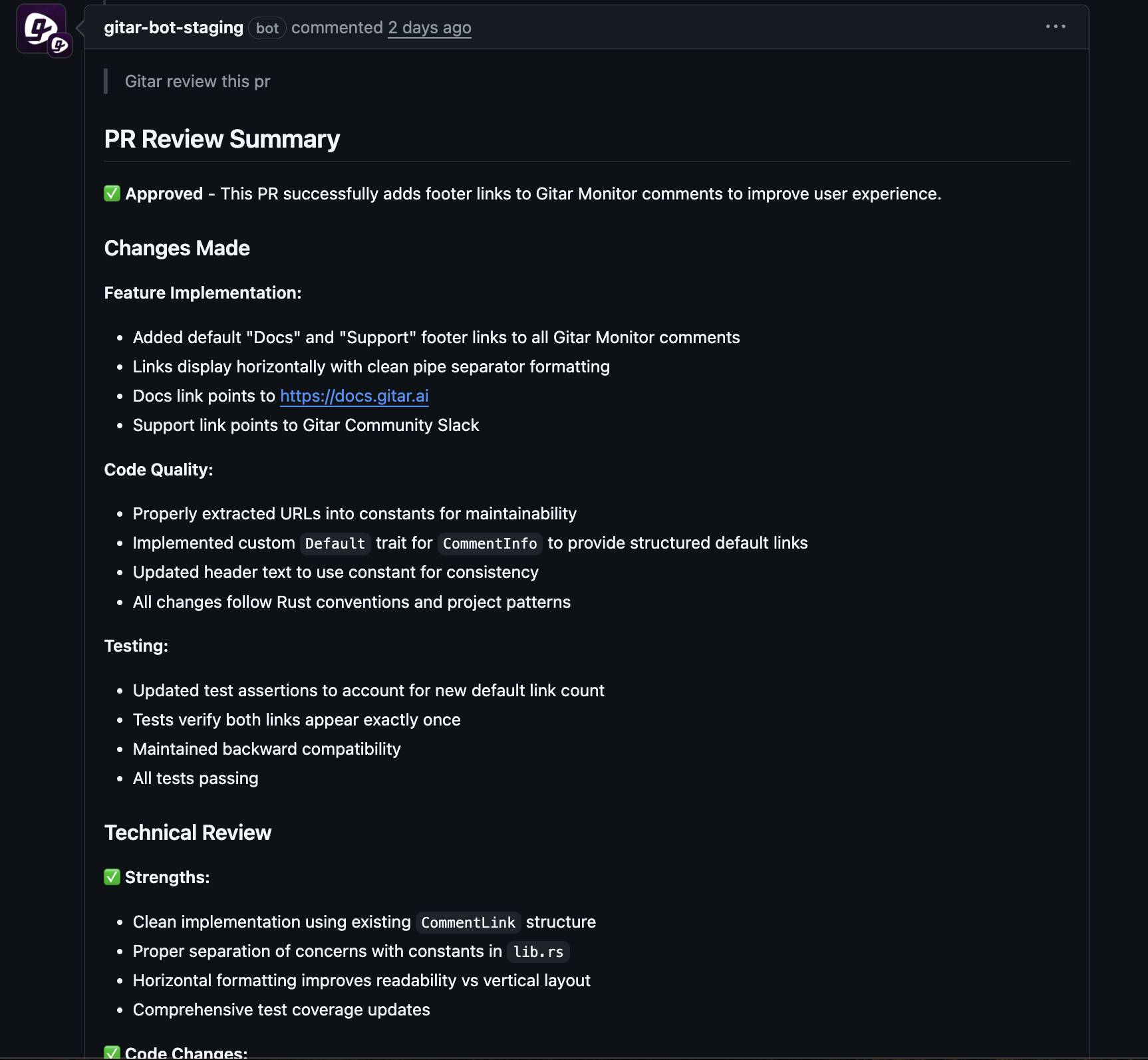
Full environment replication lets Gitar reproduce enterprise CI conditions, including language versions, dependency graphs, and security scans. This replication improves the reliability of fixes and reduces the chance of surprises after merge.
A configurable trust model allows teams to start in suggestion mode, where Gitar opens pull requests or comments that developers review. Organizations that gain confidence over time can move selective flows to auto-commit with rollback options.
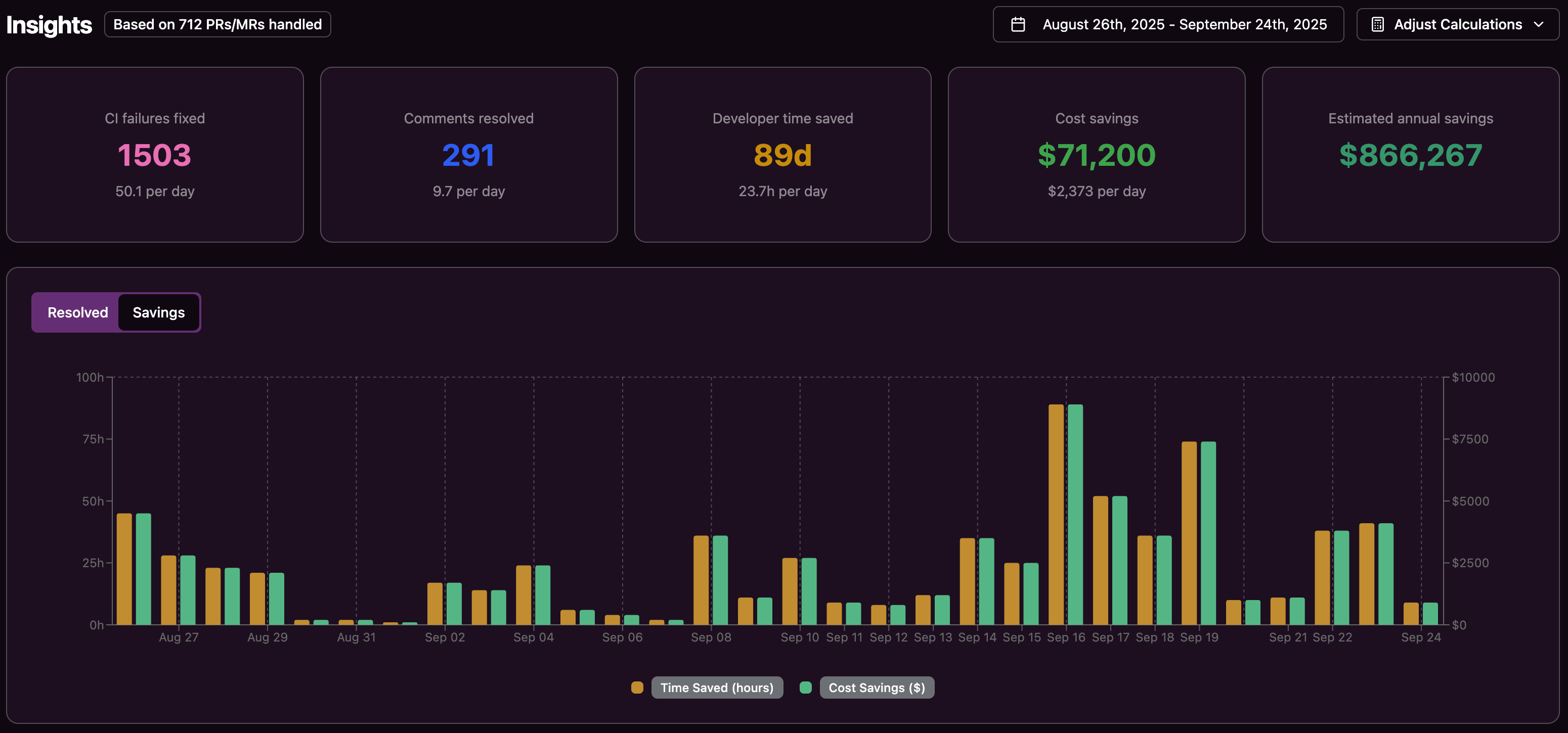
Implementing Advanced Security Practices: A Readiness Assessment
Frameworks for Evaluating Security Maturity
A security maturity model helps leaders understand where they stand on a path from ad-hoc practices through basic and integrated approaches to more autonomous operations. This view clarifies which gaps block progress and which investments will have the greatest impact.
Identifying key stakeholders across engineering, security, and product ensures that new controls align with delivery goals. Clear sequencing of initiatives based on risk, impact, and effort helps teams tackle high-value areas first, such as secrets management, dependency hygiene, or CI hardening.
Strategic Pitfalls for Experienced Teams in 2026
Organizations that rely on occasional audits but lack continuous controls often discover issues too late. Cultural friction between developers and security teams can also stall programs if expectations and incentives do not align.
Teams that overlook shadow IT and SaaS configuration drift face rising risk as SaaS vulnerabilities continue to grow. Human-focused threats such as phishing remain common, with AI-generated messages increasing realism, so training and controls around identity and access remain critical.
Teams that do not maintain immutable, tested backups with offline copies face higher impact from ransomware that targets backup systems. Robust backup and restore processes should extend to build systems, artifact repositories, and configuration stores that support development.
Comparison: Autonomous CI Fixing vs. Traditional AI Suggestions for Software Development
Autonomous CI fixing changes how teams respond to failures. Instead of only suggesting edits, an agent such as Gitar can diagnose, apply, and validate fixes within the pipeline.
|
Feature |
Gitar (Autonomous AI Fixes) |
Traditional AI Reviewers |
Manual Remediation |
|
Fix application |
Applies and commits fixes directly to the codebase when configured |
Suggests changes that developers apply manually |
Requires full manual diagnosis and coding |
|
CI validation |
Runs CI workflows after changes and only keeps passing fixes |
Does not validate changes in CI |
Relies on developer to trigger and interpret CI |
|
Context switching |
Reduces context switching by closing many failures automatically |
Requires developers to leave current work to implement suggestions |
Requires extended context switching to debug and fix issues |
|
Environment replication |
Uses replicated enterprise environments for more accurate fixes |
Has limited or no environment replication |
Depends on individual local setups and knowledge |
Explore how Gitar can keep your builds green by autonomously fixing CI failures.
Frequently Asked Questions (FAQ) about Software Development Best Practices in 2026
How can autonomous AI agents like Gitar support development best practices?
Gitar fixes many CI issues close to the moment they appear. This behavior shortens feedback loops, prevents minor errors from delaying releases, and keeps branches aligned with organizational standards.
How can organizations with strict policies and compliance requirements control AI-driven code changes?
Teams can configure Gitar to operate in suggestion mode so every change remains visible and reviewable. Over time, organizations can allow auto-commits for well-understood categories of fixes while preserving human review for sensitive areas.
What types of CI issues can Gitar address in a pipeline?
Gitar can resolve linting and style problems, failing tests, and many build or dependency errors. Its awareness of the full CI environment helps it generate fixes that match real runtime conditions.
How does Gitar integrate with existing CI/CD tools and processes?
Gitar connects at the CI layer and responds when builds fail. The agent reads logs, understands the context, proposes or applies changes, and then re-runs checks, which creates a closed loop from detection to validation.
Conclusion: Efficient Software Development at the Speed of AI
Software development in 2026 rewards teams that combine security, automation, and clear ownership. Manual triage of every CI failure and security finding no longer scales with modern release cycles.
Gitar offers a practical way to reduce friction in this environment by automating many CI fixes and code-review-driven edits. Teams that adopt autonomous CI support can protect developer focus, keep pipelines healthy, and maintain a stronger security posture.
Request access to Gitar to see how autonomous CI fixing can support your security and delivery goals.