Key Takeaways
- Self-healing DevOps platforms reduce CI/CD bottlenecks by diagnosing and fixing common failures without manual intervention.
- Engineering leaders can recover significant developer time and budget by targeting high-frequency CI issues with autonomous remediation.
- Successful adoption depends on integration with existing tools, clear governance, and gradual increases in automation levels.
- Common risks include over-engineering custom agents, skipping trust-building phases, and overlooking security and compliance controls.
- Gitar provides an autonomous CI assistant that fixes broken builds and implements review feedback, which you can try at Gitar.
The Strategic Context: Why Self-Healing DevOps Matters Now
Modern AI coding tools accelerate code creation, so CI/CD pipelines now act as a primary bottleneck for delivery speed. Teams ship more changes, but manual log reading, debugging, and re-runs keep cycle times high.
Self-healing DevOps platforms shift operations from reactive support to proactive, automated recovery. These systems identify failures, choose likely fixes, and apply changes with minimal human input, which turns CI/CD from a cost center into a lever for faster, more reliable releases.
Teams with 20 or more developers can lose a meaningful share of capacity to recurring CI failures and review churn. Automating that work cuts context switching and shortens feedback loops, which improves both throughput and code quality.
Executive Summary: A Practical Self-Healing DevOps Framework
Self-healing DevOps automation relies on three pillars: autonomous detection, intelligent remediation, and continuous optimization. Traditional monitoring tools raise alerts and wait for humans, while self-healing systems act on those alerts and report back outcomes.
Key Components of Self-Healing Architecture
- Intelligent monitoring and detection that analyzes logs, metrics, and historical incidents to spot anomalies instead of only fixed thresholds.
- Autonomous remediation that applies code changes, configuration updates, or infrastructure adjustments to resolve known failure patterns.
- Continuous learning that uses past fixes and outcomes to refine future remediation plans without constant manual tuning.
Industry Landscape: Moving From Reactive to Autonomous CI/CD
DevOps automation has progressed from ad hoc scripts to infrastructure-as-code and now to AI-driven systems. Recent platforms focus less on running steps and more on managing outcomes, such as green builds and merged pull requests with minimal manual work.
Market Segments for Self-Healing DevOps
- Monitoring and alerting platforms that collect signals and sometimes trigger simple automated runbooks.
- Suggestion-based AI tools that propose fixes but still rely on developers to edit code and push commits.
- Autonomous healing engines that detect failures, generate patches, and commit changes with auditable histories.
Enterprise teams often slow adoption until they trust how an agent behaves. Configurable automation levels, approvals, and clear logs help address compliance, security, and governance expectations.
Strategic Considerations for Implementation
Build vs. Buy Decisions
Internal builds require deep expertise in agents, orchestration, and distributed systems. Teams must solve concurrency, retries, state management, and context sharing across jobs while keeping the system reliable and observable.
Commercial platforms provide these capabilities out of the box. Evaluation criteria typically include:
- Effort to integrate with current CI/CD tools and source control systems.
- Support for different automation modes, from suggestions to full auto-commit.
- Compatibility with multiple languages, frameworks, and CI environments.
- Security, access controls, audit trails, and compliance features.
ROI Expectations and Success Metrics
Teams usually measure self-healing value through a mix of speed and quality metrics. Common indicators include:
- Reduced mean time to resolution for CI failures.
- Lower manual time spent reading logs and re-running jobs.
- Higher deployment frequency and more stable releases.
- Improved developer satisfaction and less after-hours firefighting.
Gitar: Autonomous CI That Fixes and Explains Itself
Gitar focuses on the CI bottleneck and turns repetitive troubleshooting into an automated workflow. The platform operates as an AI assistant that understands failures, proposes fixes, and can optionally commit changes on its own.
How Gitar Automates CI Fixes
Gitar coordinates long-running agents that operate in noisy, parallel CI environments. The system maintains context about jobs, commits, and comments, manages retries, and avoids duplicate work while a pipeline runs.
During a CI failure, Gitar can:
- Analyze logs to identify the root cause.
- Generate the relevant code or configuration change.
- Update the pull request with commits or suggested patches.
- Comment with an explanation of what changed and why.
This workflow covers frequent issues such as lint violations, unit test failures, and simple build problems, which reduces the time developers spend on mechanical fixes.
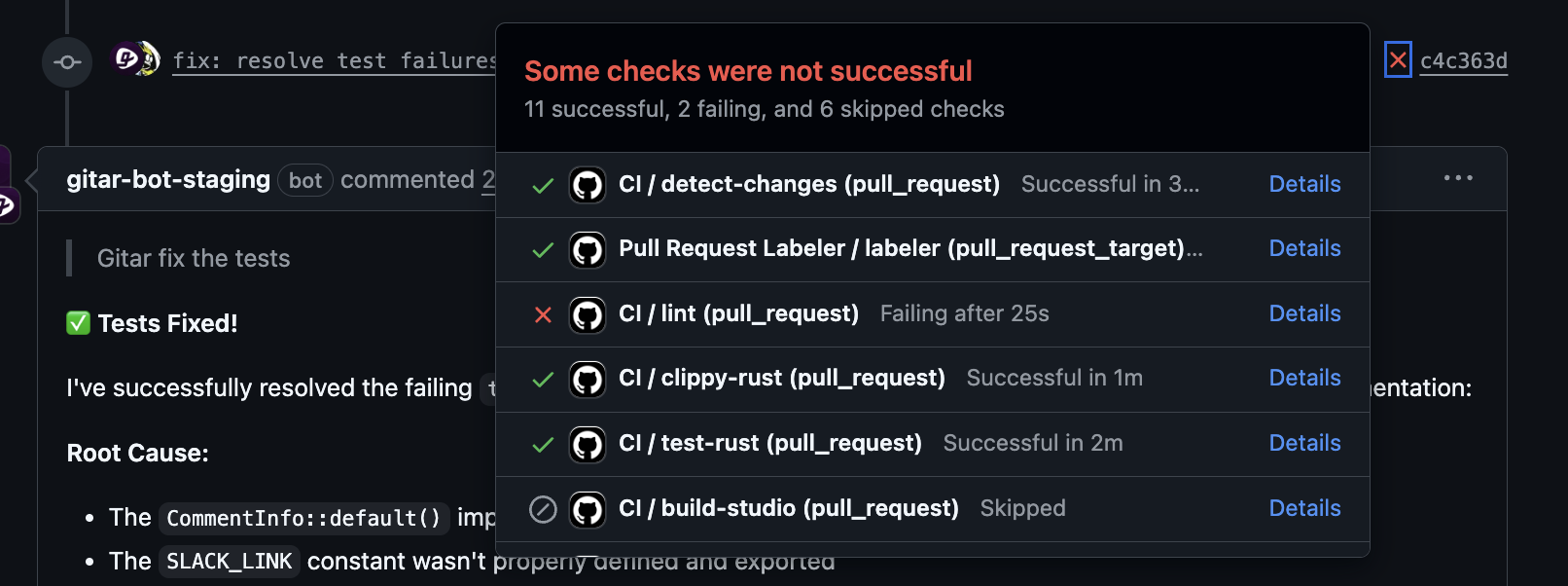
Configurable Trust and Control
Gitar supports multiple operating modes so teams can match automation levels to their comfort and compliance needs. A conservative mode suggests changes and waits for human approval, while a more aggressive mode commits fixes directly, with rollback options available.
This progression helps teams build trust. Early phases validate that the agent understands the codebase, test suite, and review standards before automation expands to more repositories or workflows.
Support for Distributed and Large Teams
Distributed teams often lose days to minor review comments and small CI failures that wait for the original author. Gitar allows reviewers to leave instructions in pull request comments, then handles the requested code updates and CI fixes automatically.
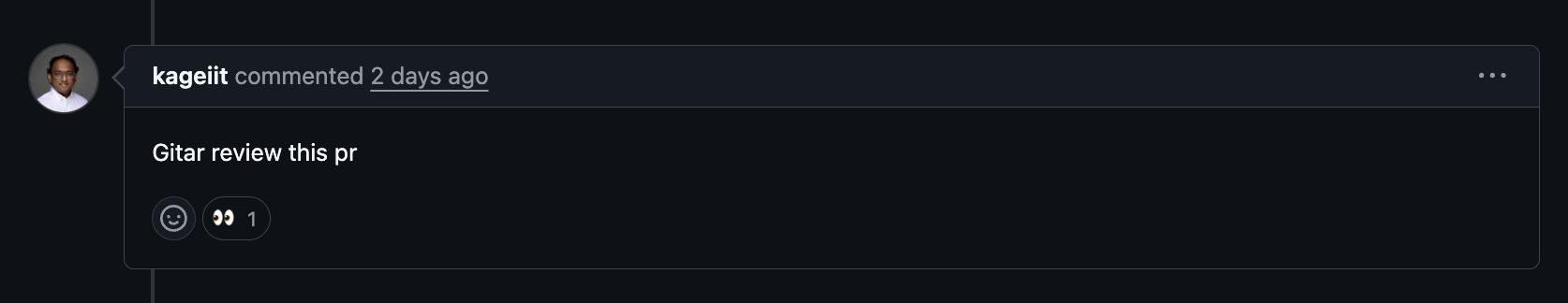
This approach enables progress around the clock, even when teams span several time zones.
Assessing Readiness for Self-Healing DevOps
Technical Readiness
Strong candidates for self-healing DevOps usually share these traits:
- Standardized CI/CD pipelines and repeatable workflows.
- APIs or integrations available for source control, CI, and observability tools.
- Existing logging, tracing, and metrics that provide clear failure signals.
- Defined security and compliance policies for automated code changes.
Change Management and Communication
Teams adopt automation more easily when leaders frame agents as collaborators, not replacements. Clear expectations about what the system will change, how it will report actions, and how humans can override decisions help reduce resistance.
Pilot Rollout Strategy
Pilots usually work best on non-critical services that generate frequent, low-risk CI failures. Teams can begin with suggestion-only mode, track resolution time and developer feedback, then widen scope and automation once benefits and safety are clear.
Common Pitfalls and How to Avoid Them
Over-Engineering Custom Solutions
Some organizations attempt to build full autonomous agents in-house on top of scripts and basic automation. The effort to maintain reliability, state, and observability for such agents often grows faster than expected and diverts attention from core product work.
Skipping Trust-Building Phases
Jumping directly to full auto-commit across critical repositories can damage trust if an early mistake appears. A gradual rollout with clear metrics and fast rollback options helps teams feel in control.
Underestimating Integration Work
Self-healing platforms must fit naturally into existing workflows for pull requests, reviews, and releases. Planning for identity management, permissions, and notification patterns up front prevents friction that can reduce adoption.
Missing Compliance and Security Controls
Automated code changes need the same or stronger controls as human changes. Role-based access, approvals, and complete logs for each automated action are essential, especially in regulated industries.
The Future of Autonomous DevOps
Self-healing DevOps platforms are shifting engineer time from reactive support to continuous improvement. Teams that invest in autonomous remediation today prepare for a future where most routine CI and deployment issues resolve without direct human effort.
The long-term role of DevOps professionals will center on designing guardrails, refining automation policies, and improving system reliability, while agents handle the repetitive tasks that slow delivery today.
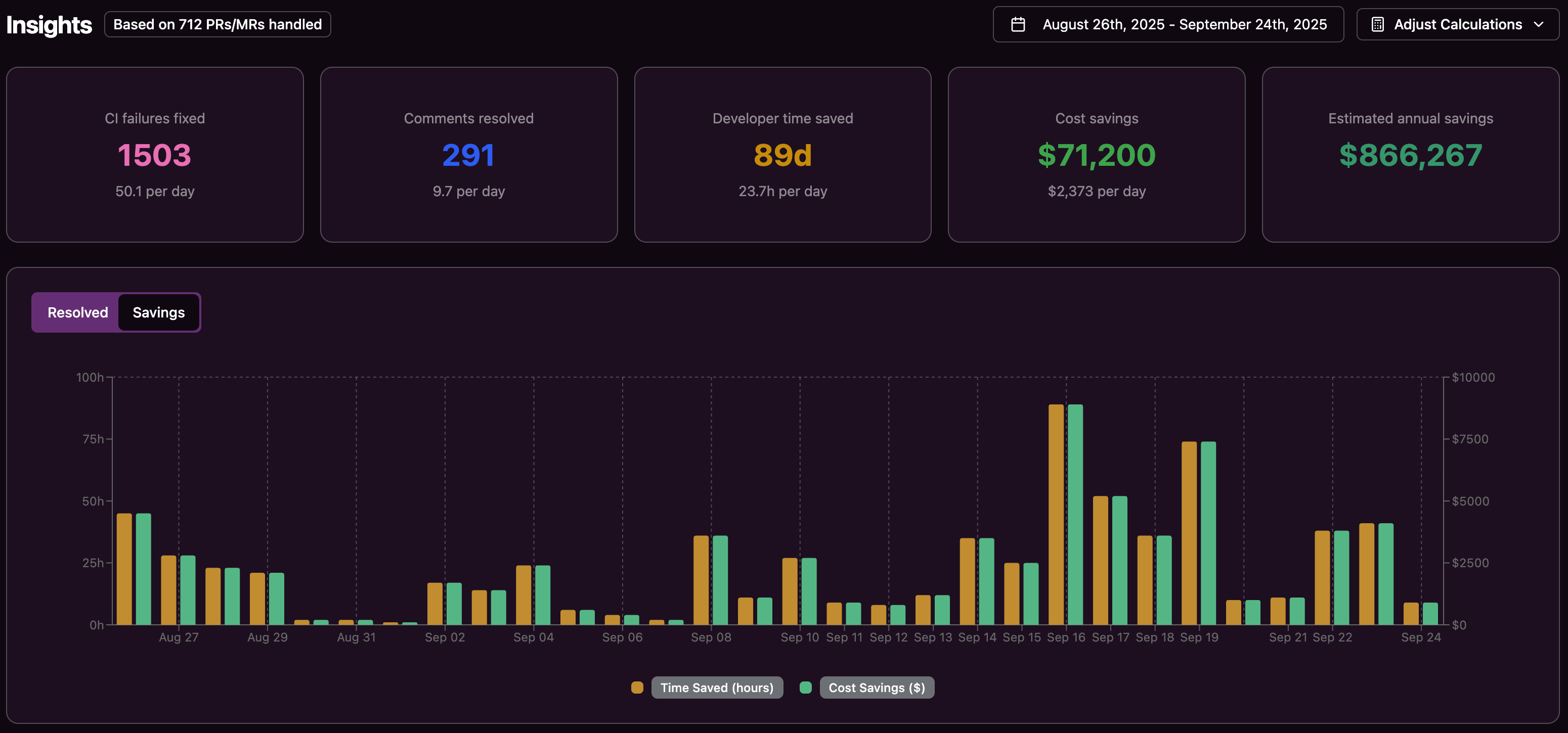
Frequently Asked Questions
How do self-healing DevOps platforms differ from traditional CI/CD automation?
Traditional CI/CD automation executes fixed scripts and jobs when triggered. Self-healing platforms interpret context from logs and code, diagnose failures, and propose or apply fixes that adapt to each situation, which reduces manual investigation and recovery work.
What security considerations are important when implementing autonomous DevOps systems?
Effective autonomous DevOps programs rely on role-based permissions, encryption in transit and at rest, detailed audit logs, and configurable approvals. Teams benefit from the option to limit automation scope, run in suggestion-only mode for sensitive areas, and review a full history of each automated change.
How can organizations measure the ROI of self-healing DevOps platforms?
ROI emerges through faster incident resolution, fewer failed builds that require human attention, and shorter lead times for changes. Metrics such as MTTR, deployment frequency, number of automated fixes, and surveyed developer satisfaction provide a clear view of impact.
What challenges do distributed teams face with CI/CD that self-healing platforms address?
Distributed teams often experience multi-day delays for small fixes due to time zone gaps and asynchronous communication. Self-healing platforms update code and resolve CI failures shortly after they occur, so work continues smoothly even when contributors are offline.
How do self-healing platforms handle complex enterprise environments with multiple dependencies?
Advanced platforms capture environment details such as language versions, build tools, external scanners, and dependency policies. This context allows them to generate fixes that match the specific enterprise stack instead of relying on generic patterns that might break local constraints.