Key Takeaways
- Manual compliance and integration testing cannot keep pace with 2026 multi-framework requirements and continuous evidence expectations.
- Autonomous integration testing tools embed in CI/CD pipelines, validate complex workflows, and generate audit-ready evidence in real time.
- Healing engines that automatically fix CI issues reduce developer toil more than suggestion-only tools, especially in complex environments.
- A phased rollout that aligns scope, automation policies, monitoring, and governance helps teams adopt automation without disrupting delivery.
- Gitar provides an AI-driven healing engine that automatically fixes CI failures in your existing pipelines, which you can try by installing Gitar for autonomous CI fixes.
Why Manual Compliance And Integration Testing Slow Teams In 2026
Modern engineering teams now operate under overlapping frameworks that demand continuous evidence across jurisdictions and industries. Many organizations combine SOC 2 with SOC 1, PCI DSS, HIPAA, and related frameworks, so any manual, framework-by-framework approach quickly becomes inefficient.
Teams that manage each standard separately often duplicate tests, documentation, and reviews. This fragmentation delays releases, increases the risk of missed obligations, and pushes compliance work to the end of the development cycle, where changes are more expensive.
SOC 2 guidance in 2026 emphasizes continuous compliance and real-time evidence, which aligns with the broader move away from point-in-time audits. SOC 2 Type 2 expectations for sustained evidence over time make manual checks impractical for any team that ships frequently.
How Autonomous Integration Testing Tools Support Continuous Compliance
Autonomous integration testing tools embed inside CI/CD pipelines and act on failures automatically. These tools treat every build and deployment as a chance to validate controls, capture evidence, and keep services within defined policies.
Most platforms share three core capabilities:
- Policy-driven testing that maps requirements to concrete checks and integration tests.
- Continuous monitoring that runs with every pipeline execution and records evidence automatically.
- Native integrations with CI platforms, version control, and ticketing systems so automation fits existing workflows.
Integration testing is especially important for processing integrity and data protection in distributed systems. Processing integrity criteria around complete, accurate, timely, and authorized data flows match directly to how services exchange messages, enforce contracts, and handle failures.
Effective tools validate these flows, record results, and surface issues as part of normal pipelines instead of separate audit projects.
Install Gitar to add autonomous CI fixing on top of your existing integration tests.
Gitar: Automating CI Fixes For Integration Testing
Gitar focuses on one high-impact problem in integration testing and compliance automation: fixing CI failures and code review feedback without manual intervention. The AI agent watches your pipelines, diagnoses causes, and commits targeted code changes back to pull requests.
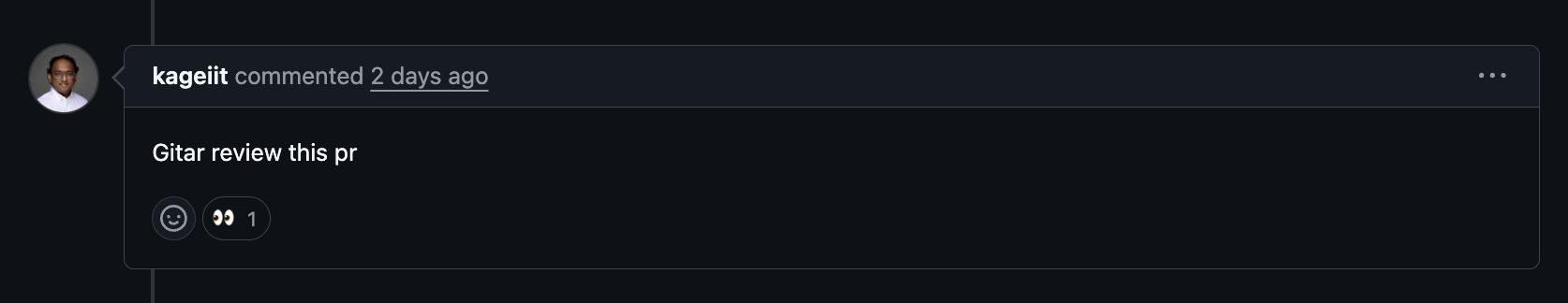
Gitar addresses issues such as failing integration tests, lint errors, and build problems by reproducing the environment, generating fixes, and pushing commits. This approach turns recurring CI problems into automated remediation steps instead of repeated manual work.
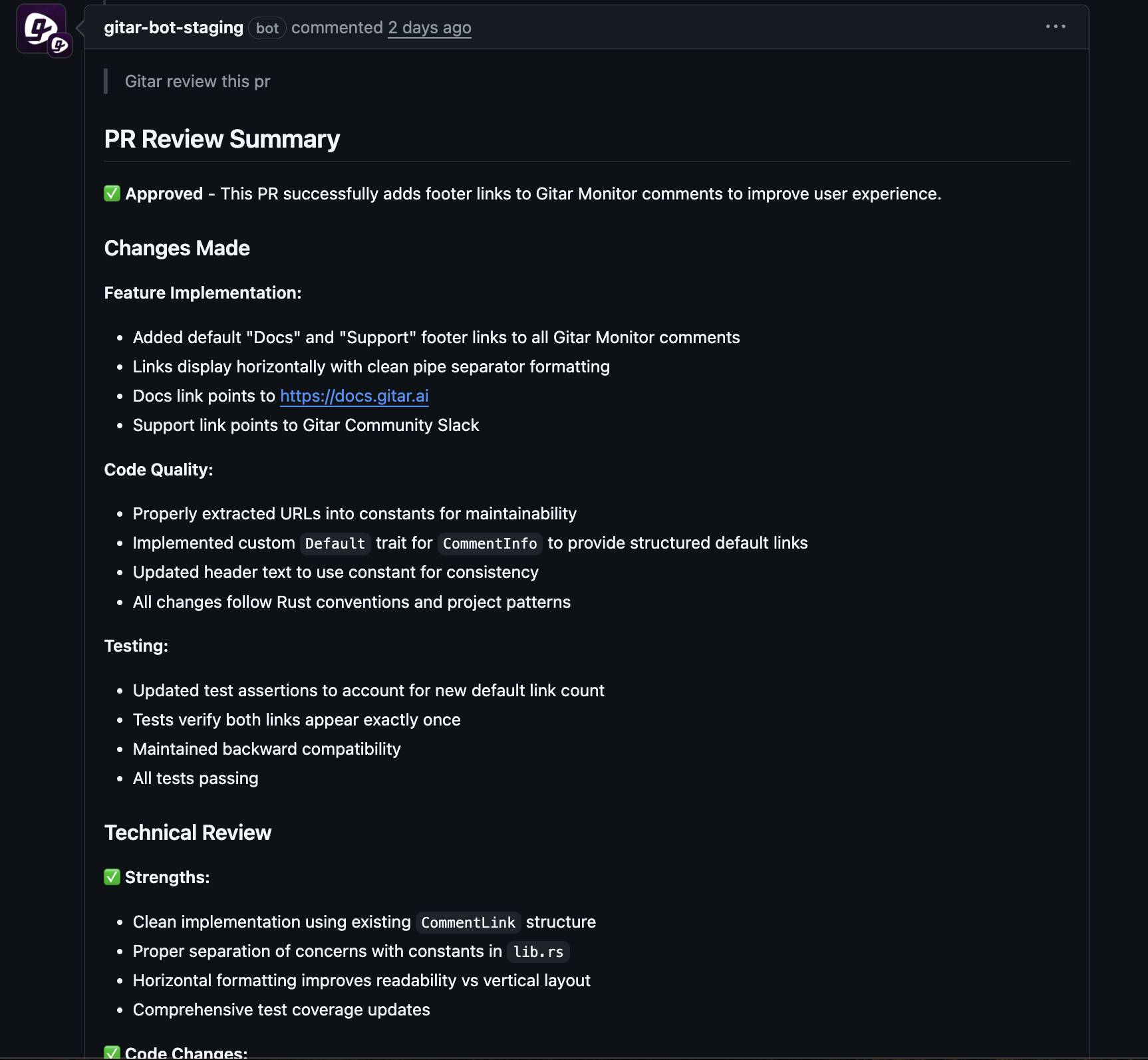
Developer workflows stay familiar because Gitar works through pull requests in GitHub and GitLab. The system updates each PR with clear messages about what changed and why, so developers keep visibility without stepping out of their normal tools.
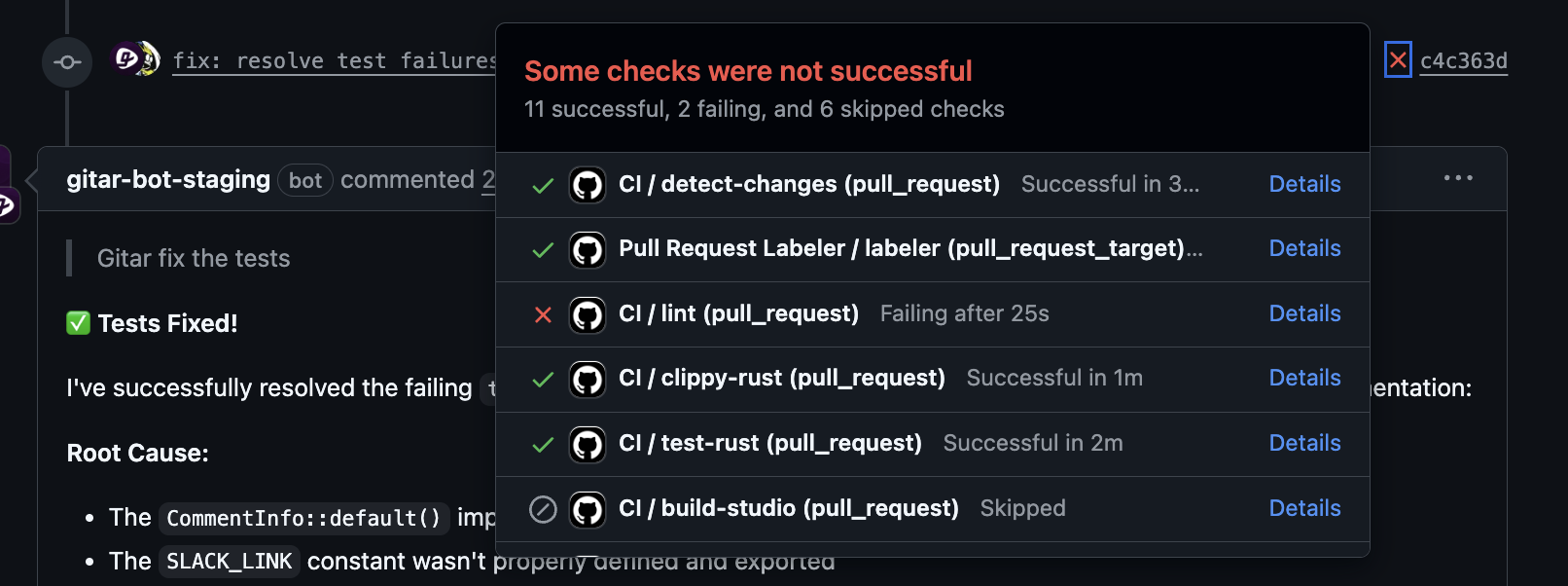
A configurable trust model lets teams start with suggestion-only mode, then progress to auto-commit once they gain confidence. This staged approach gives engineering leaders control over how quickly autonomous fixes enter production workflows.
Install Gitar to reduce the time your team spends unblocking failing integration tests.
Planning And Rolling Out Autonomous Integration Testing
Successful automation programs start with a clear scope, realistic policies, and a roadmap that balances safety and speed.
1. Define Scope And Policies
Teams first map regulatory and internal obligations to specific integration test requirements. Scoping guidance highlights the need for configurable policies and risk-based coverage, so automation concentrates on the highest-impact systems and controls.
This step includes identifying overlapping frameworks, clarifying evidence expectations, and defining which stages of the pipeline must enforce which controls.
2. Embed Automation In CI/CD
Automation then becomes a native part of build and release workflows. Tools validate integration tests, enforce policies, and, in Gitar’s case, repair CI failures so engineers do not need to leave their normal tools to investigate common issues.
Many teams begin with read-only checks and automated suggestions. Over time, they enable autonomous remediation for well-understood failure modes.
3. Monitor Continuously And Support Audits
Continuous review cycles align with a self-healing posture where detected issues feed backlog work instead of one-off fire drills. Dashboards that summarize integration test coverage, failures, and fixes help leaders track readiness.
Automation should also produce artifacts that external reviewers can understand, such as logs, mappings, and procedures that show how integration tests cover specific controls.
4. Scale Automation With Governance
SOC 2+ mappings that align SOC 2 with ISO 27001, HIPAA, GDPR, NIST, HITRUST, and DORA show how quickly requirements converge. As the scope expands, change management, approvals, and review workflows keep automation aligned with risk appetite.
Cross-functional remediation expectations also mean that security, engineering, and operations must agree on ownership for issues surfaced by autonomous tools.
Avoiding Common Pitfalls With Automation
Engineering teams that already maintain complex CI/CD systems often try to build their own automation layer on top of general-purpose AI. This effort can consume months of work and still fall short of specialized tools that already handle environment replication, CI orchestration, and guardrails.
Stakeholder misalignment also slows adoption. Automation that ignores developer experience, or compliance expectations, tends to be bypassed or disabled. Early collaboration between security, compliance, and development helps prevent that outcome.
Independent examinations expect clear mappings, logs, and procedures, so low-quality automation can increase audit friction instead of reducing it. Governance, clear documentation, and simple review paths help teams keep automation outcomes reliable.
Healing Engines vs. Suggestion Engines
Automation tools fall into two broad categories: suggestion engines and healing engines. Suggestion engines identify issues and propose fixes that humans must implement. Healing engines, such as Gitar, both detect and implement fixes within policy boundaries.
|
Capability |
Suggestion Engines |
Healing Engines (Gitar) |
|
Issue handling |
Surface problems for manual action |
Detect and commit fixes automatically |
|
Workflow impact |
Interrupt developer flow |
Resolve common failures in the background |
|
Environment context |
Partial understanding of CI setup |
Replicates dependencies and tools for accurate fixes |
Suggestion engines can improve visibility but still rely on manual remediation. Healing engines reduce cycle time and cognitive load by closing the loop automatically, particularly for recurring integration test and build failures. Enterprises increasingly seek unified systems instead of many point tools, which makes healing engines attractive for complex environments.
Measuring ROI Of Autonomous Integration Testing
Return on investment spans direct engineering savings and broader business impact.
On the engineering side, teams often track reduced time spent on CI triage, shorter lead times for changes, and fewer context switches during development. For a mid-sized team, automation of recurring CI issues can reclaim hundreds or thousands of hours per year.
At the business level, compliance increasingly functions as a trust and sales enabler. Faster evidence generation, fewer production incidents tied to integration failures, and more predictable release schedules translate into lower risk and smoother customer conversations.
Frequently Asked Questions About Integration Testing Automation
How do autonomous tools stay accurate as requirements change?
Autonomous tools map requirements to technical checks and keep those mappings up to date for major platforms. They validate behavior across services, log outcomes, and produce artifacts that link each test to one or more obligations, so updates to requirements translate into updated policies and checks.
What safeguards limit the risk of automated fixes?
Modern platforms offer trust modes, rollback options, and approval workflows. Teams can begin in suggest-only mode, then enable automatic remediation for low-risk failures while keeping human review for sensitive changes.
How do these tools connect to existing CI/CD systems?
Most autonomous tools plug into CI platforms such as GitHub Actions, GitLab CI, CircleCI, and Buildkite through standard configuration files and APIs. They run as additional pipeline steps, integrate with version control, and send status updates back to pull requests or issues.
Conclusion: Using Autonomous Integration Testing To Stay Ready In 2026
Continuous, automated integration testing has become a practical requirement for teams that work under multiple regulatory frameworks and ship changes frequently. Automation that lives inside CI/CD pipelines helps organizations maintain evidence, reduce risk, and keep releases moving.
Healing engines such as Gitar extend this model by closing the loop on CI failures, which reduces manual effort and keeps developers focused on higher-value work. Teams that adopt these tools with clear scope, governance, and monitoring can improve both delivery speed and operational readiness.
Install Gitar to add an autonomous healing layer to your integration testing workflows.
