Key Takeaways
- CI failures and slow code reviews consume thousands of developer hours each year and create hidden costs through context switching and burnout.
- Traditional CI tools surface red builds but still depend on manual diagnosis and fixes, which do not scale in complex, fast-changing environments.
- Autonomous “healing engines” detect failures, find root causes, and apply validated fixes so developers can stay focused on feature work.
- Security controls, auditability, and configurable automation levels make it possible to adopt autonomous remediation while meeting enterprise governance needs.
- Gitar delivers autonomous CI healing, code review assistance, and environment-aware fixes; teams can explore it through a quick setup and demo.
The Escalating Cost of CI Failures on Developer Experience and Business Velocity
Hidden Costs of Unreliable CI
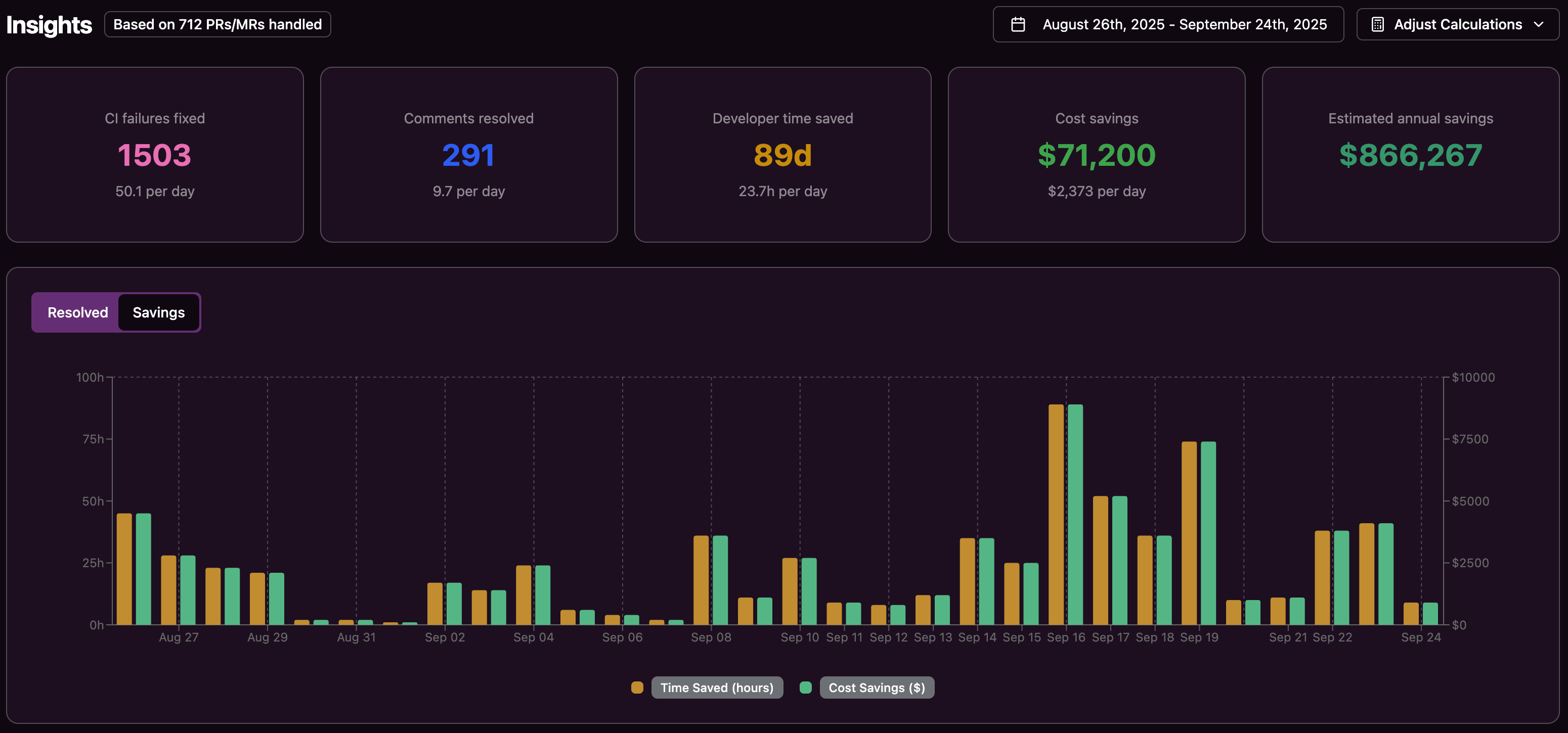
Build failures and slow reviews quickly add up. A 20-developer team can lose about 5,000 hours per year to CI and review friction, which translates to roughly $1 million in productivity at a $200 loaded hourly rate.
Context switching amplifies this loss. A simple five-minute fix often turns into an hour of lost focus once a developer leaves deep work to investigate a failing build.
Frequent failures also change behavior. Teams start treating red builds as noise, which weakens quality gates and delays releases.
Where Traditional CI Platforms Fall Short
CI systems such as Jenkins, GitHub Actions, and GitLab CI were built to orchestrate builds and report status. They excel at telling you that something failed. They rarely fix the problem for you.
Misconfigurations and brittle tests often break pipelines, yet most teams still scan logs and tweak configs by hand. AI-assisted coding tools increase code volume and pull requests, which further raises the number of potential failure points. Typical failures include invalid YAML, missing permissions, and environment mismatches that are repetitive and automatable.
Modern architectures add more pressure. Microservices, polyglot stacks, and third-party integrations create many failure paths. Runner issues, configuration drift, and external service problems often require deep context that traditional tools do not capture.
Autonomous CI as a Practical Shift
Autonomous CI changes the focus from detection to resolution. These systems watch for failures, identify likely causes, propose code or configuration changes, and validate fixes in the pipeline before handing a green build back to the team.
This approach directly reduces one of the largest drains on developer productivity. Developers spend less time firefighting and more time on product work.
Teams that reach this state build a culture of green builds and predictable releases instead of normalizing broken pipelines.
How Gitar Uses Autonomous Healing to Stabilize CI Pipelines
Gitar focuses on removing CI toil rather than just surfacing failures. The platform detects broken builds, diagnoses causes, applies fixes, and re-runs pipelines so developers receive working pull requests instead of red ones.
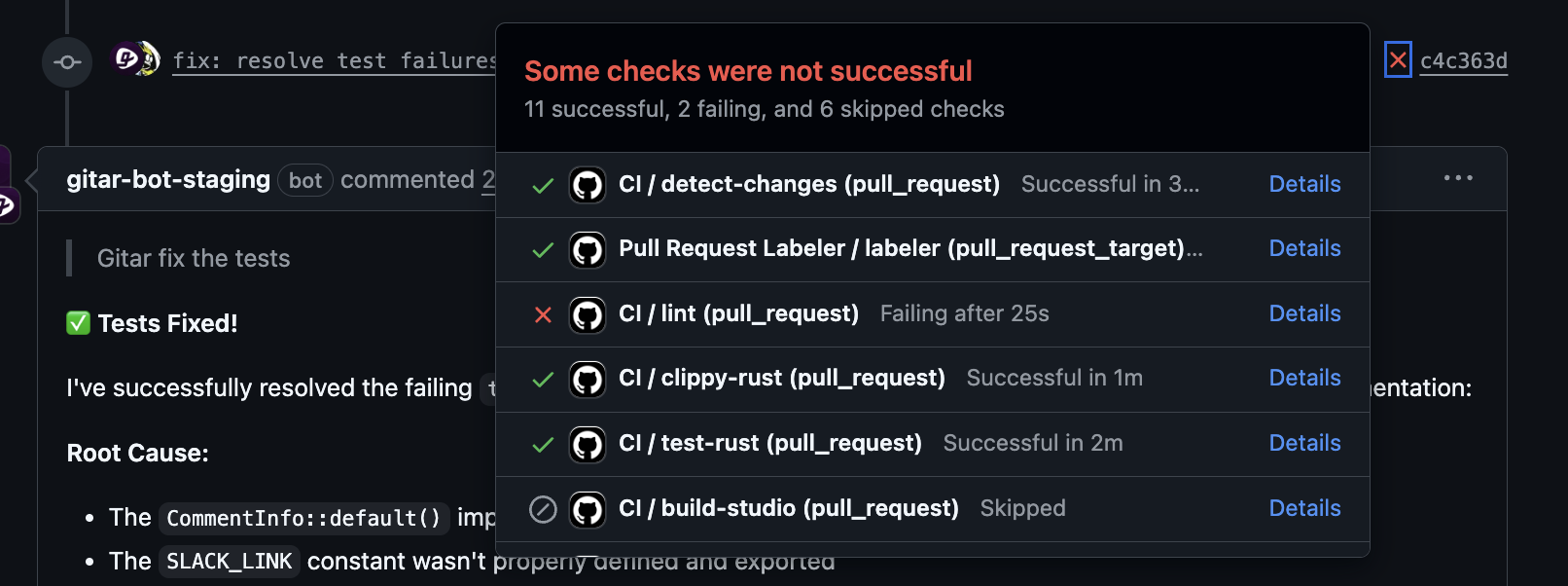
End-to-end fixing covers the full loop. When a lint error or test failure appears, Gitar reads the logs, updates the code, commits the change to the pull request branch, and verifies the result in CI.
Full environment replication helps Gitar avoid “works in AI, fails in CI” scenarios. Unlike tools that run in generic sandboxes, Gitar mirrors real build environments, including specific JDKs, SDKs, and dependencies. This level of fidelity and attention to environment details supports reliable fixes across complex pipelines.
A configurable trust model lets teams phase in automation. Initially, Gitar can post proposed fixes as suggestions that developers approve with one click. Over time, teams can enable auto-commits with safeguards and rollbacks as confidence increases. This staged rollout pattern aligns with common change-management practices.
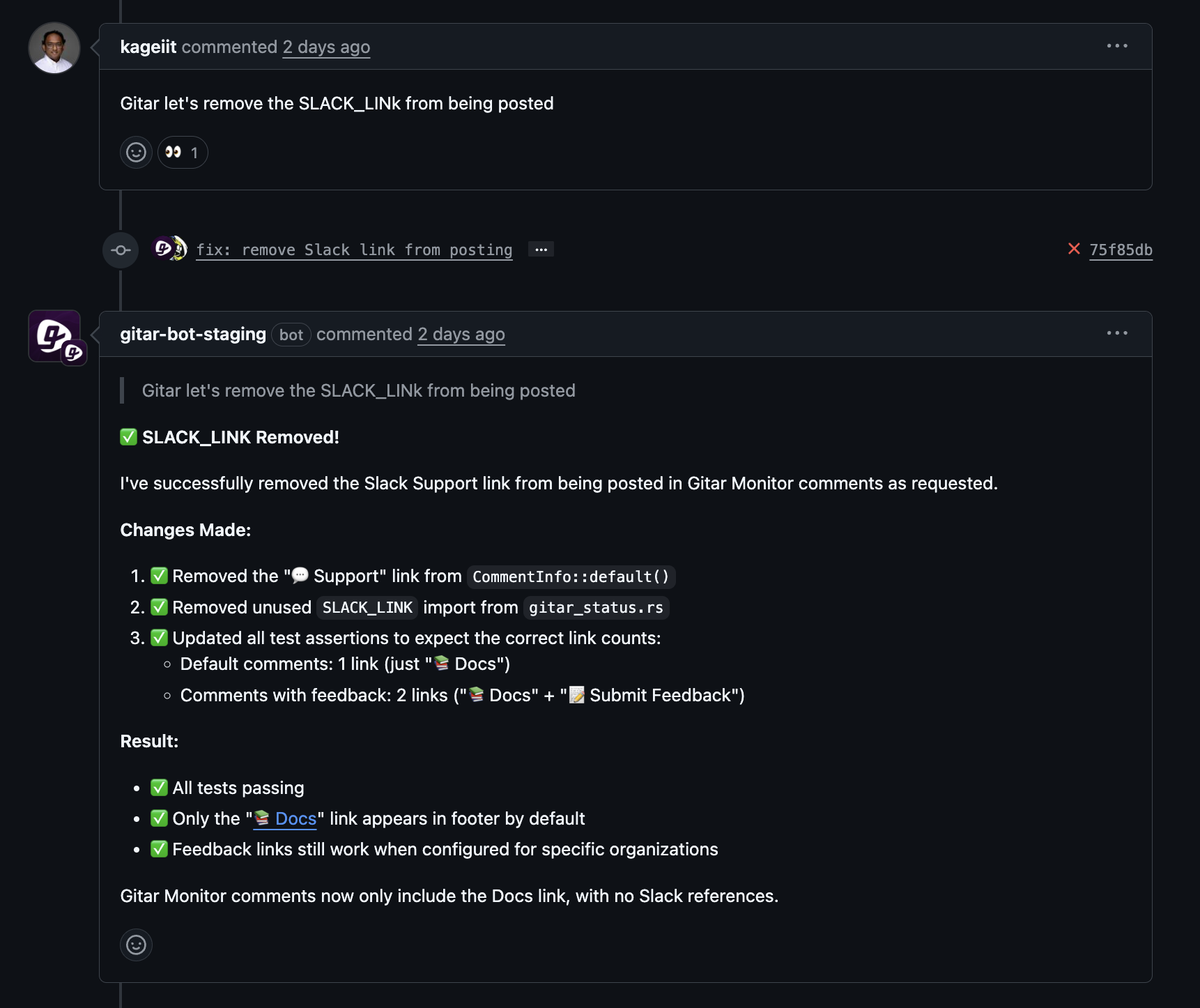
Gitar also supports reviewers. A reviewer can mention Gitar in a pull request comment with instructions, and Gitar will update the code, commit the change, and leave an explanation in the thread. This shortens long review cycles, especially for distributed teams.
Cross-platform support lets Gitar plug into existing CI providers and repositories rather than replacing them. This integration-first approach helps teams adopt autonomous healing without re-architecting pipelines.
Install Gitar to automatically fix broken builds and reduce manual CI debugging.
Key Capabilities to Evaluate in Platforms for Build Reliability
Healing Engines vs Suggestion Engines
Suggestion engines focus on recommendations that still require human action. Developers receive hints or code snippets and must apply, test, and adjust them.
Healing engines focus on outcomes. Self-healing test frameworks already show how systems can update selectors and assertions automatically, and self-healing systems extend this pattern into production operations. CI healing engines bring this model into build pipelines.
Root Cause Analysis and Automated Fixes
Modern platforms need more than log pattern matching. AI models that combine code changes, history, and environment data can pinpoint likely causes faster than manual inspection.
Effective remediation should cover tasks such as:
- Updating code for lint and style violations
- Adjusting failing tests and assertions
- Resolving dependency and version conflicts
The strongest platforms continuously learn from successful fixes to improve future recommendations and actions.
Reliable Environment Replication
Enterprise CI pipelines often involve multiple SDKs, language versions, and scanners. These combinations create fragile points where builds fail unexpectedly, and consistent environments improve stability.
Platforms that replicate environments accurately can validate fixes under realistic conditions, which reduces “fix and re-fail” cycles.
Proactive Failure Prevention and Test Stability
Pre-commit and pre-push checks help catch issues before they reach CI. Machine learning models that predict risky changes and optimize build and test paths add another layer of protection.
Flaky tests also need attention. Analytics that identify and quarantine unstable tests and data showing that a small set of tests often cause most flakiness highlight the importance of targeted remediation.
Security, Compliance, and Auditability
Enterprises must see and control what automation does. Supply chain security frameworks and guidance on AI tooling both emphasize traceability and safe data handling.
Leading platforms provide:
- Configurable aggression levels for automated actions
- Complete audit trails of every change
- Rollback options for any automated commit
- Alignment with enterprise compliance controls
Comparison: How Gitar Differs from Other Approaches
|
Feature Area |
Gitar (Autonomous Healing) |
Suggestion Engines |
Traditional CI Platforms |
|
Core Focus |
Detects CI failures, finds causes, applies and validates fixes |
Highlights issues and potential fixes for developers to apply |
Runs builds and reports pass or fail with logs |
|
Developer Effort |
Optional review of proposed or auto-committed fixes |
Manual editing, testing, and iteration |
Manual diagnosis and remediation after each failure |
|
Environment Context |
Replicates real CI environments for accurate validation |
Often limited or generic environment assumptions |
Uses configured environment but provides no autonomous fixes |
|
Governance |
Configurable aggression, audit trails, and rollback |
Relies on human control at every step |
Standard CI permissions without automated remediation |
Conclusion: Moving Toward Autonomous Developer Experience
Autonomous CI healing shifts build management from manual firefighting to managed automation. Teams that adopt platforms like Gitar can reclaim time lost to repeated CI failures, shorten review loops, and maintain healthier pipelines as systems grow.
Improvements in deployment frequency, lead time, and developer satisfaction provide a practical way to measure impact.
Frequently Asked Questions about Reducing Build Failures
How do healing engines like Gitar differ from suggestion engines and IDE assistants?
Gitar operates in the CI pipeline after code is committed. It detects failures, analyzes logs and code, generates a candidate fix, commits the change, and validates it in CI. Suggestion engines surface ideas and snippets but depend on developers to apply and test them. IDE assistants such as GitHub Copilot help during coding in the local environment and do not address failures in remote CI pipelines.
How do autonomous fixers handle complex enterprise CI setups?
Gitar is built to mirror real CI environments, including multiple SDKs, language versions, and third-party tools. By running fixes and validations in a replica of the actual pipeline, Gitar keeps changes aligned with the constraints and integrations that exist in production CI.
How can teams build trust in automated fixes for critical code?
Teams can start with conservative modes where Gitar proposes changes but does not commit them. Developers review diffs, verify behavior, and approve changes with a click. As confidence grows, teams can enable automatic commits with full audit logs and rollback options so automation remains transparent and controllable.