Key Takeaways
- Automated test failure resolution tools have become a strategic priority in 2026 as AI code generation shifts the bottleneck from writing code to validating and deploying it.
- Flaky tests, noisy alerts, and frequent CI failures now consume significant engineering time, which pushes teams to adopt autonomous CI healing rather than rely on manual debugging alone.
- Engineering leaders can evaluate these tools by looking at measurable outcomes such as Change Failure Rate, time-to-merge, CI compute spend, and developer satisfaction.
- Low-risk pilots, clear governance, and alignment with security and compliance standards help organizations adopt autonomous CI fixes while maintaining control and trust.
- Gitar provides autonomous CI failure resolution that helps teams fix broken builds and ship higher quality software with less manual effort.
The Critical Juncture: Why Automated Test Failure Resolution Is a Strategic Priority
Software organizations in 2026 face a growing productivity gap. AI-powered code generation increased output, yet CI pipelines now struggle to keep pace. Teams see more failing builds and noisy alerts, and flaky tests reduce confidence in automation and push developers to ignore red builds.
The economics are clear. For a typical 20-developer team, time lost to CI failures and extended review cycles can approach $1 million per year in productivity. Change Failure Rate has become a central engineering metric that influences delivery performance and competitive position. Manual debugging and suggestion-only tools no longer scale with current release expectations.
Engineering leaders who recognize this shift now treat autonomous test failure resolution as core delivery infrastructure. The focus moves from asking whether to automate fixes to deciding how to introduce automation in a controlled, measurable way.
A New Paradigm: Gitar as an Autonomous CI Healing Engine
Gitar operates as a CI healing engine that detects, diagnoses, and resolves many CI pipeline failures without manual intervention. The goal is to keep developers focused on design and problem-solving while an autonomous agent handles routine breakages in the pipeline.
End-to-End Autonomous Fixing
When a CI check fails because of lint errors, test failures, or build issues, Gitar analyzes the logs, identifies the likely root cause, proposes a code change, and commits that change back to the pull request. This behavior covers frequent issues such as style violations, straightforward test failures, and dependency problems so that simple breakages rarely block progress.
Full Environment Replication
Gitar replicates complex enterprise CI environments so that fixes match real conditions. The system respects details such as JDK versions, multi-SDK setups, and integrations with tools like SonarQube and Snyk. This context awareness helps ensure that changes that pass in Gitar’s environment also pass in the organization’s actual CI stack.
Intelligent Code Review Actioning
Gitar also accelerates code review workflows. Reviewers add comments with instructions, and Gitar implements the requested changes and commits them to the pull request. Distributed teams benefit in particular, because a reviewer in one time zone can leave feedback that Gitar applies before the original author returns to the code.
Configurable Automation and Trust
Teams can adjust Gitar’s behavior to match their risk tolerance. A conservative mode posts fixes as suggestions that require one-click approval. A more aggressive mode allows automatic commits while still preserving rollback options. This progression lets organizations build trust as they see results.
Cross-Platform CI Support
Gitar integrates with major CI platforms, including GitHub Actions, GitLab CI, CircleCI, and BuildKite. Engineering leaders can adopt autonomous fixes without replacing existing tools or restructuring pipelines.
The Evolution of Automated Test Failure Resolution
Automated test failure resolution has moved through clear stages. Initial tools focused on alerts and dashboards. They surfaced that something failed, but left root-cause analysis and fixing to developers. Common CI failures now span test instability, build errors, deployment issues, and configuration gaps, which creates more noise than many teams can handle manually.
Later solutions introduced recommendation engines that pointed to likely causes or suggested code edits. Those tools improved visibility but still required developers to apply and validate fixes. Flaky tests forced teams to rerun suites repeatedly and slowed releases, which exposed the limits of detection-only approaches.
The current stage centers on autonomous resolution. Self-healing pipelines that repair broken tests and deployment failures now define expectations for high-performing engineering groups. Gitar fits into this stage by validating fixes against full CI workflows and reducing the need for developers to restart or babysit failing pipelines.
Strategic Considerations for Adopting Autonomous CI Fixes
Build vs. Buy
Custom autonomous CI agents require orchestration of concurrent jobs, long-running context, and integrations with large language models. That work often competes with product roadmap priorities. Many teams now compare the ongoing cost and risk of internal platforms with adopting a tool like Gitar that already handles multi-repo, multi-pipeline environments.
Measuring ROI and Success Metrics
Clear metrics help justify adoption and tune automation levels. Common measures include:
- Reduction in Change Failure Rate and post-deployment incidents
- Shorter time-to-merge for pull requests
- Fewer rerun builds and lower CI compute costs
- Higher developer satisfaction and fewer context switches
For a 20-developer team that spends about an hour per day on CI issues, even partial automation can recapture hundreds of thousands of dollars in annual value through time savings and faster delivery.
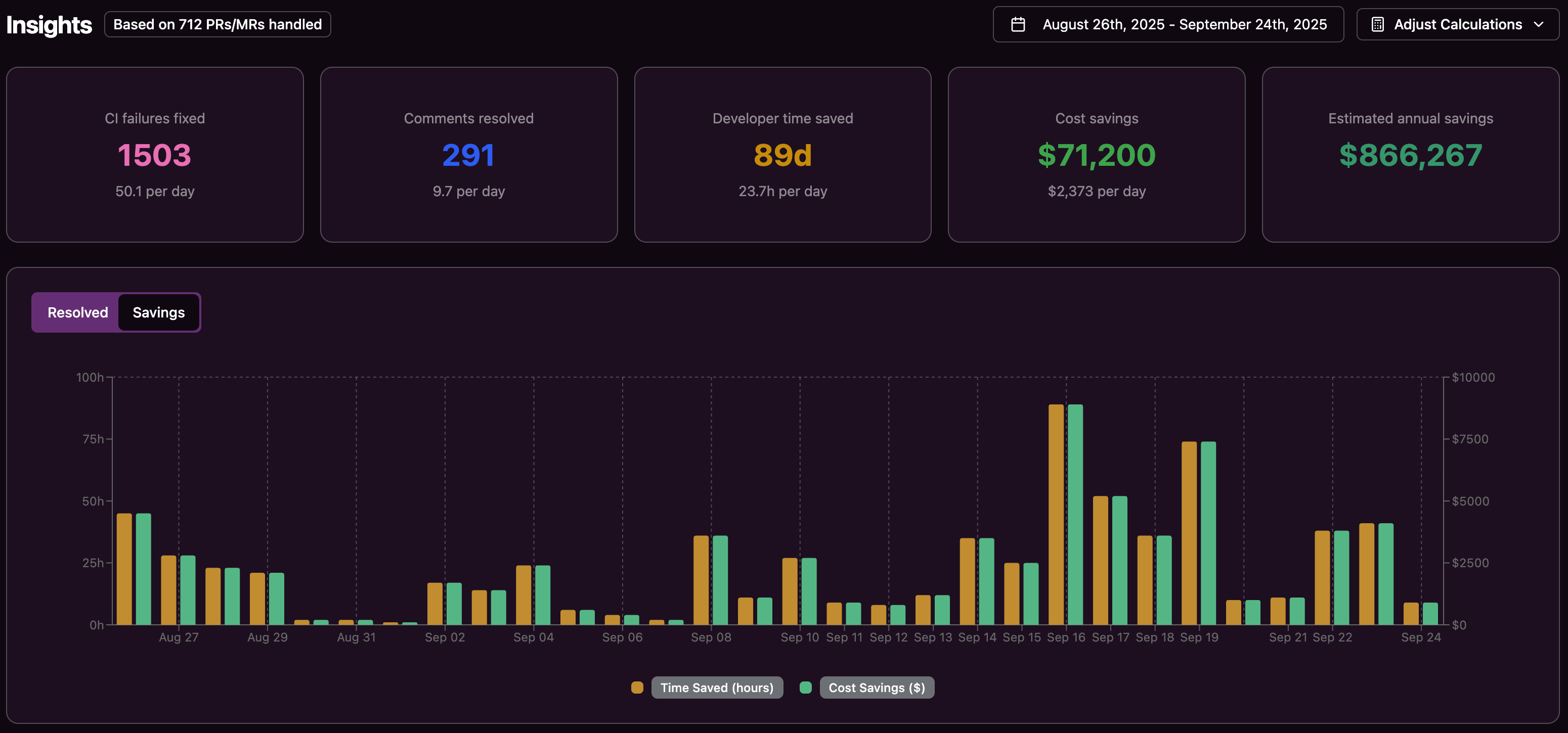
Change Management and Adoption
Developers must trust that automated changes are safe and reversible. Many organizations start with lower-risk repositories and modest automation, such as suggestion-only modes focused on lint and simple test fixes. They then expand scope and autonomy as the tool proves reliable and audit logs confirm that changes remain easy to track and roll back.
Security and Compliance
Modern CI/CD pipelines now include security checks that flag misconfigurations and application-level risks during builds. Autonomous agents must respect those controls. Evaluation criteria often include how the tool handles secrets, whether on-premises or private deployments are available, and how its actions appear in existing audit and approval flows.
Implementation Readiness and Common Pitfalls
Assessing CI Automation Maturity
Teams typically move from manual debugging to monitored pipelines with limited scripts, to autonomous agents that diagnose and fix failures. Leaders who map current maturity can plan an incremental path rather than attempting a sudden shift to full autonomy.
Aligning Stakeholders
Engineers, managers, DevOps, and security teams each view automation through a different lens. Successful rollouts give engineers code-level visibility, provide managers with metrics, reassure DevOps about reliability, and document how the tool stays within security and compliance boundaries.
Avoiding Strategic Pitfalls
Common issues include over-investing in bespoke internal agents, enabling full automation before teams build trust, and focusing on technical features while neglecting communication and governance. Underestimating the complexity of enterprise CI environments can also lead to tools that work in simple cases but fail under real workload diversity.
Understanding the Landscape: Automated Test Failure Resolution Options
The market for automated test failure resolution spans several solution types, each with strengths in different situations.
|
Solution Type |
Approach |
Implementation |
Best For |
|
Manual Debugging |
Reactive investigation |
Developer-driven |
Complex, unique failures |
|
AI Code Reviewers |
Suggestion generation |
Varies by tool |
Code quality insights |
|
On-Demand Fixers |
Triggered assistance |
Single-threaded |
Occasional guidance |
|
Autonomous Agents |
Proactive resolution |
Full automation |
Systematic CI healing |
Gitar operates as an autonomous healing engine in this landscape. While AI code reviewers such as CodeRabbit can offer recommendations or one-click patches, Gitar focuses on applying fixes, validating them against CI workflows, and returning builds to a passing state with minimal developer effort.
This approach gives organizations a path to reduce manual validation, keep pipelines green, and standardize how routine CI failures get resolved.
Install Gitar to add autonomous failure resolution to your existing CI pipelines.
Frequently Asked Questions about Automated Test Failure Resolution Tools
How do these tools handle complex enterprise environments?
Modern autonomous CI agents such as Gitar replicate complete build environments, including language runtimes, dependency graphs, security scans, and multi-service configurations. That replication helps the agent propose fixes that match real production conditions and avoid changes that only work in simplified test setups.
What security considerations should leaders review before adoption?
Leaders should confirm that the tool operates within existing permission models, records a clear audit trail, and integrates with current security scanners. It is important to understand where code and logs are processed, how secrets are protected, and whether the vendor offers deployment models that align with internal policies.
How can organizations measure ROI for automated test failure resolution?
Teams can track metrics such as average time-to-green for failing builds, the number of failures resolved without developer input, and the share of CI compute spend tied to reruns. Many organizations also survey developers on perceived interruption and frustration levels before and after rollout to capture qualitative impact.
What implementation approach helps build developer trust?
A low-risk starting point uses suggestion or approval modes on non-critical repositories, focused on lint and clear-cut test failures. Teams review results, adjust guardrails, and only then expand automation to more complex services and direct commits.
How do these tools integrate with existing workflows?
Tools like Gitar integrate with GitHub, GitLab, and common CI platforms so that developers continue to work through familiar pull request comments and status checks. The agent participates in existing review and approval steps rather than replacing them, which keeps governance intact while reducing manual debugging.
Conclusion: Moving Toward Autonomous Developer Tooling
Automated test failure resolution tools address a growing constraint in 2026 software delivery: keeping increasingly busy CI pipelines healthy without consuming developer time. Autonomous CI healing shifts routine failure handling to specialized agents and allows teams to focus on building features.
Gitar offers one path to that outcome by combining environment-aware diagnosis, automatic fixes, and configurable trust levels. Organizations that adopt this type of tooling early can reduce delivery friction, improve engineering focus, and standardize how they respond to recurring CI failures.
