Key Takeaways
- Automated security scanning embedded in CI/CD pipelines reduces supply chain risk and misconfigurations that manual reviews often miss.
- Self-healing CI shifts work away from developers by autonomously fixing common failures, which reduces context switching and improves delivery speed.
- Successful adoption of automated security and fixing requires clear change management, toolchain integration, and alignment with existing DevOps practices.
- Modern DevSecOps programs rely on shift-left scanning, strong access controls, continuous monitoring, and formal security standards to keep pipelines resilient.
- Teams can use Gitar to automatically fix broken builds and move toward a self-healing CI pipeline without disrupting existing workflows.
Why Automated Security Scanning is Crucial for Modern DevOps
Security scanning now sits at the core of CI/CD pipelines as complexity and risk keep rising. Gartner projects that 45% of organizations will suffer supply chain attacks by the end of 2026, with CI/CD pipelines as primary targets, which highlights how exposed build systems have become.
Manual security checks cannot keep pace with short release cycles. Developer productivity often drops, with as much as 30% of time lost to troubleshooting CI/CD issues. Fifty-seven percent of organizations reported security incidents from exposed secrets in insecure DevOps processes, showing how widely pipeline weaknesses still appear.
A shift-left security approach reduces these risks and costs. Early detection through automated security scanning within the pipeline reduces remediation costs and improves development velocity, so security becomes part of everyday delivery rather than a late-stage blocker.
Gitar’s Approach to Self-Healing CI: Autonomous Fixes for CI Failures
Gitar acts as an autonomous CI agent that fixes failing pipelines and resolves code review feedback without constant developer involvement. The system operates as a CI healing engine that understands your environment, applies fixes, and keeps builds moving.
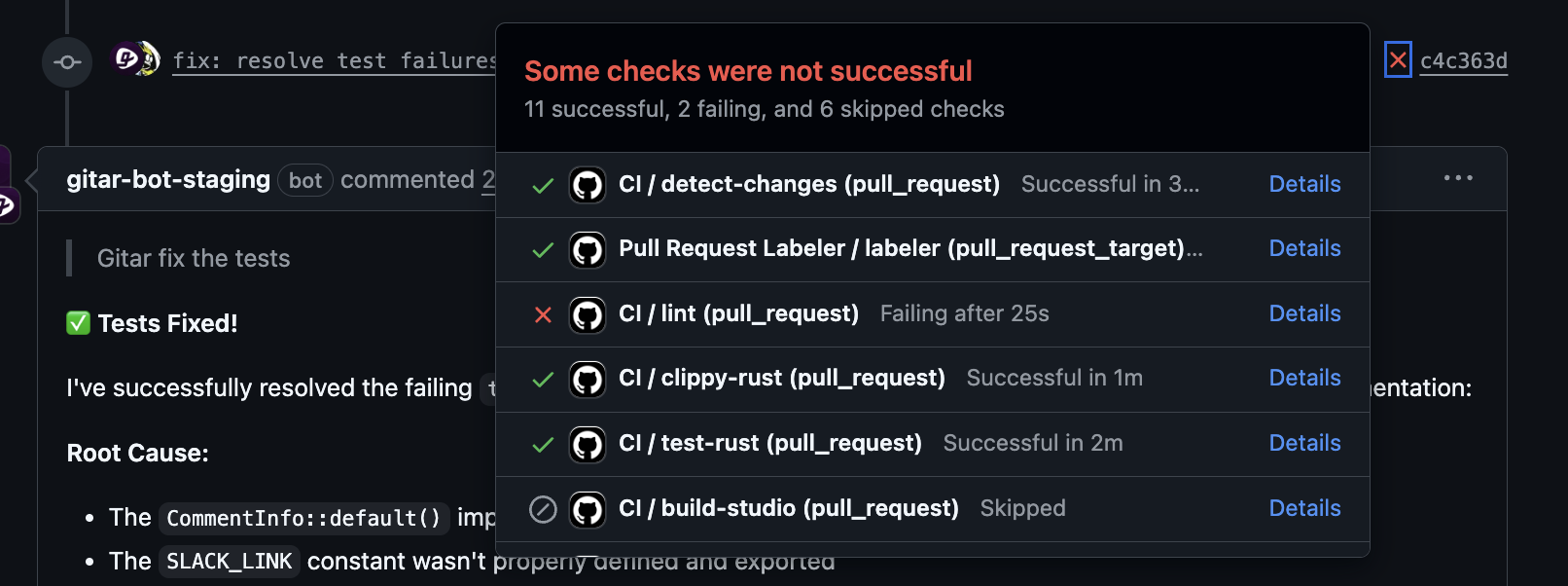
Key Capabilities for Enhanced Efficiency
- End-to-end fixing: Gitar applies, validates, and commits fixes for failures such as lint errors, test failures, and build issues. This process reduces context switching and shortens what would otherwise be long debugging sessions.
- Full environment replication: Gitar reproduces complex enterprise workflows, including specific SDK or JDK versions and integrations with third-party tools. This context lets it generate fixes that match real production and staging environments.
- Configurable trust model: Teams can start with conservative mode, where Gitar posts suggested fixes as pull request comments, then move to more aggressive auto-commit behavior as trust grows. This staged approach helps teams adopt automation at a pace that fits their risk tolerance.
Strategic Integration of Automated Security Scanning in DevOps
Preparing Your Organization for Automated Solutions
Teams need a realistic view of their security maturity before adding automation. Processes, ownership, and incident response should be clear. Poorly designed automation can create new risks when tools operate in isolation from real workflows and governance, so planning and communication are essential.
Toolchain Integration That Fits Existing Workflows
Security scanning and automated fixing work best when they plug into existing CI/CD systems such as GitHub Actions, GitLab CI, or CircleCI with minimal extra configuration. Gitar supports multiple platforms, which helps large organizations avoid lock-in to any single ecosystem and keeps teams on shared workflows.
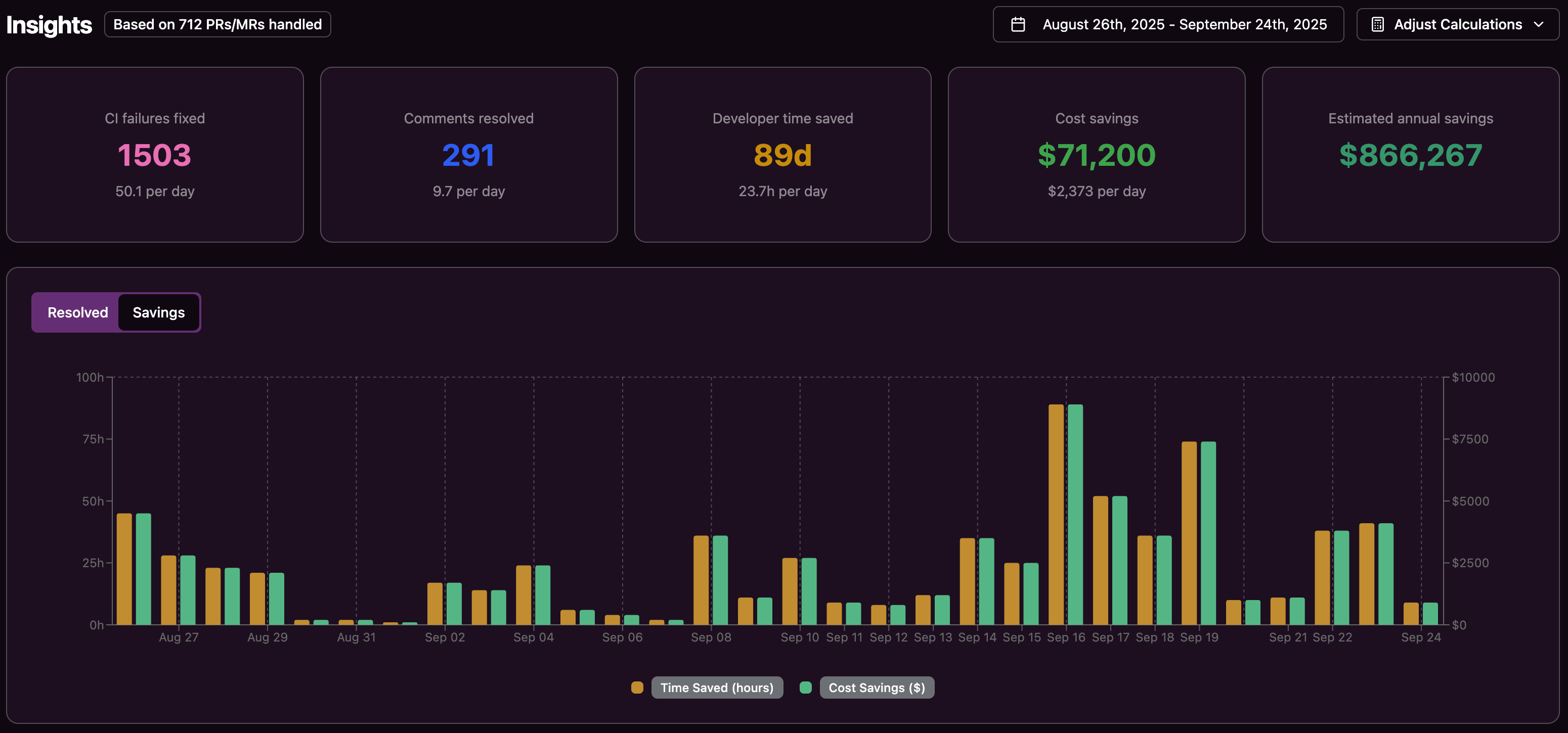
Measuring ROI and Success
Clear metrics help show the value of automated CI fixing. Teams often track:
- Time spent on CI/CD troubleshooting before and after automation
- Number of failed builds automatically resolved
- Lead time from pull request to merge
- Incidents tied to configuration or security failures in the pipeline
For an organization with 20 developers, manual CI/CD remediation can approach one million dollars per year in lost productivity, so even partial automation can drive meaningful savings.
Securing AI-Driven Code Generation
AI-assisted coding tools increase code volume and speed, which adds pressure to downstream validation. AI-driven threats and code flaws are reshaping web security and require continuous monitoring across the development lifecycle. Automated scanning and fixing help keep pace with this accelerated change.
Gitar vs. Traditional Solutions: A Comparison
|
Feature |
Gitar (Healing Engine) |
Traditional Tools |
Manual Practices |
|
Issue resolution |
Autonomously fixes, validates, and commits changes |
Identifies issues and provides suggestions |
Relies on manual detection, debugging, and fixing |
|
Integration |
Works across major CI platforms |
Often runs as a single pipeline step |
Depends on ad hoc or manual processes |
|
Developer interruption |
Low, since fixes run automatically |
High, because developers must apply suggestions |
High, with frequent context switching |
|
Build environment |
Replicates the full environment for accurate fixes |
Uses the tool’s internal assumptions |
Requires local reproduction of issues |
Best Practices for Resilient and Secure DevOps Workflows
Shift-Left Security with Automated Scans
Teams should integrate SAST, DAST, software composition analysis, and secrets scanning early in the development lifecycle. This approach keeps security debt from piling up and reduces the cost of remediation by catching issues before they reach production.
Immutable Infrastructure and RBAC
Immutability principles and role-based access control provide strong foundations for secure pipelines. Infrastructure testing tools such as Test Kitchen, Terratest, and InSpec, along with drift detection, help keep environments consistent and trustworthy.
Continuous Monitoring and Auditing
Centralized logging and monitoring with services such as AWS CloudTrail or Azure Monitor improves visibility into anomalous or unauthorized activity. Continuous real-time monitoring across development and deployment stages helps teams identify threats before they cause damage.
Compliance and Security Standards
Frameworks such as OWASP Top 10 CI/CD Security Risks, NIST SP 800-204D, and SLSA define expectations for artifact integrity and supply chain security. Aligning automated tools with these standards supports both compliance and consistent engineering practices.
Proactive Vulnerability Management
Automated scanning and remediation create a proactive posture for vulnerability management. Systems that continuously identify, prioritize, and address issues reduce the window of exposure and limit unplanned work.
Common Pitfalls in Automated Solutions for Experienced Teams
Over-Reliance on Tools Without Context
Security and CI tools that operate without awareness of the full environment can surface noisy or inaccurate results. Context-aware systems that understand configuration, dependencies, and runtime behavior provide more reliable fixes.
Ignoring Organizational Readiness
Teams that adopt automation without preparing roles, expectations, and training often see resistance or low adoption. A staged rollout with clear communication and feedback loops improves long-term success.
Underestimating the Cost of Manual Remediation
Manual fixing of recurring CI and security issues consumes expensive engineering time. The hidden costs of interruptions and context switching usually outweigh the perceived simplicity of handling each failure by hand.
Lack of Integration with Broader Strategy
Automation that exists as a standalone tool instead of part of a defined DevSecOps strategy can leave gaps. Connecting CI healing, security scanning, monitoring, and incident response creates a stronger overall posture.
Key Answers about Automated CI Fixing and Gitar
Gitar and AI-Driven Code Generation in CI/CD
Gitar manages the increased flow of changes from AI-generated code by monitoring pipelines, detecting failures, and applying fixes before merge. Full environment replication helps prevent bottlenecks that appear when AI tools accelerate code creation but do not handle downstream validation.
Gitar in Complex CI Setups
Gitar supports complex enterprise pipelines that use multiple SDKs, specific JDK versions, and third-party integrations. The system tailors fixes to these environments, which reduces human error and supports compliance without forcing teams to simplify their toolchains.
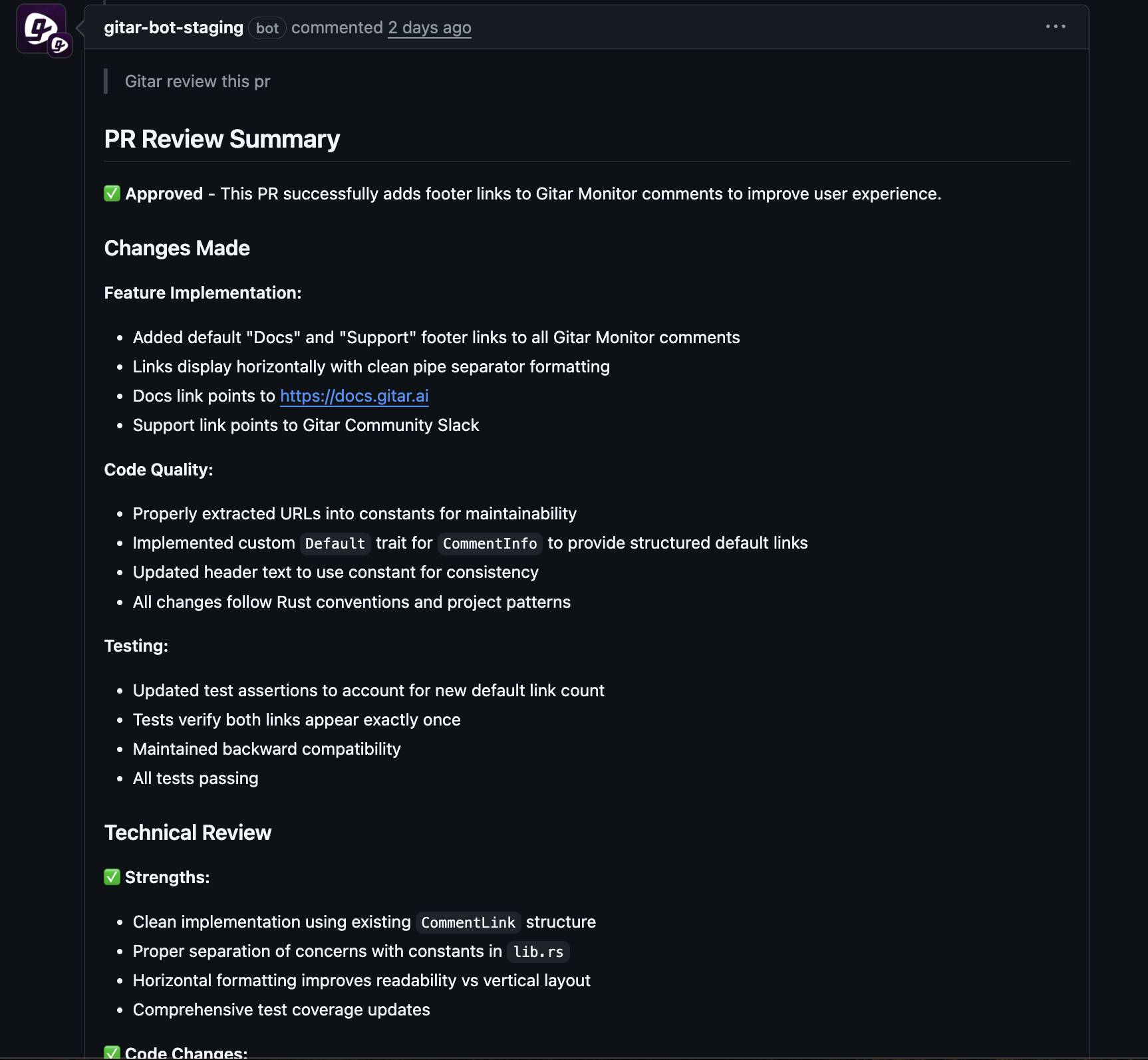
Building Trust in Automated Fixes with Gitar
Teams can enable Gitar in conservative mode so it proposes fixes as pull request suggestions that developers review and accept. After seeing consistent, high-quality results, teams often move to more aggressive modes where Gitar auto-commits safe fixes, with rollback options in place.
Reducing the Right-Shift Validation Bottleneck
CI pipelines often become a bottleneck when AI tools increase pull request volume. Gitar reduces this right-shift pressure by turning CI into a self-healing system that detects and fixes many failures automatically, which keeps validation and merging aligned with the pace of code generation.
How Gitar Differs from AI Code Review Tools
General AI code review tools focus on commenting and suggestions. Gitar extends beyond review by acting on those insights: it edits code, runs tests in the real environment, and commits validated fixes, which further reduces manual workload.
Conclusion: Enhance Your DevOps Pipeline with Self-Healing CI
Modern DevOps and AI-accelerated development make manual validation and remediation difficult to sustain. Automated security scanning and CI healing offer a practical way to protect pipelines while keeping delivery speed high.
Gitar provides an autonomous CI healing engine that keeps builds green, reduces repetitive work, and supports a more resilient DevSecOps practice in 2026.