Key Takeaways
- Manual linter and test fixes in pull requests create heavy context switching, slow merges, and measurable financial waste across engineering teams.
- Automated linter and test fix solutions act as “healing engines” that identify, fix, and validate CI failures inside pull requests, instead of only flagging issues.
- Full environment awareness is essential for reliability, since many CI failures come from dependency conflicts, flaky tests, and environment-related issues that simple suggestion tools cannot resolve.
- Successful adoption depends on clear trust models, phased rollout, and attention to distributed team dynamics so that automation supports existing workflows instead of disrupting them.
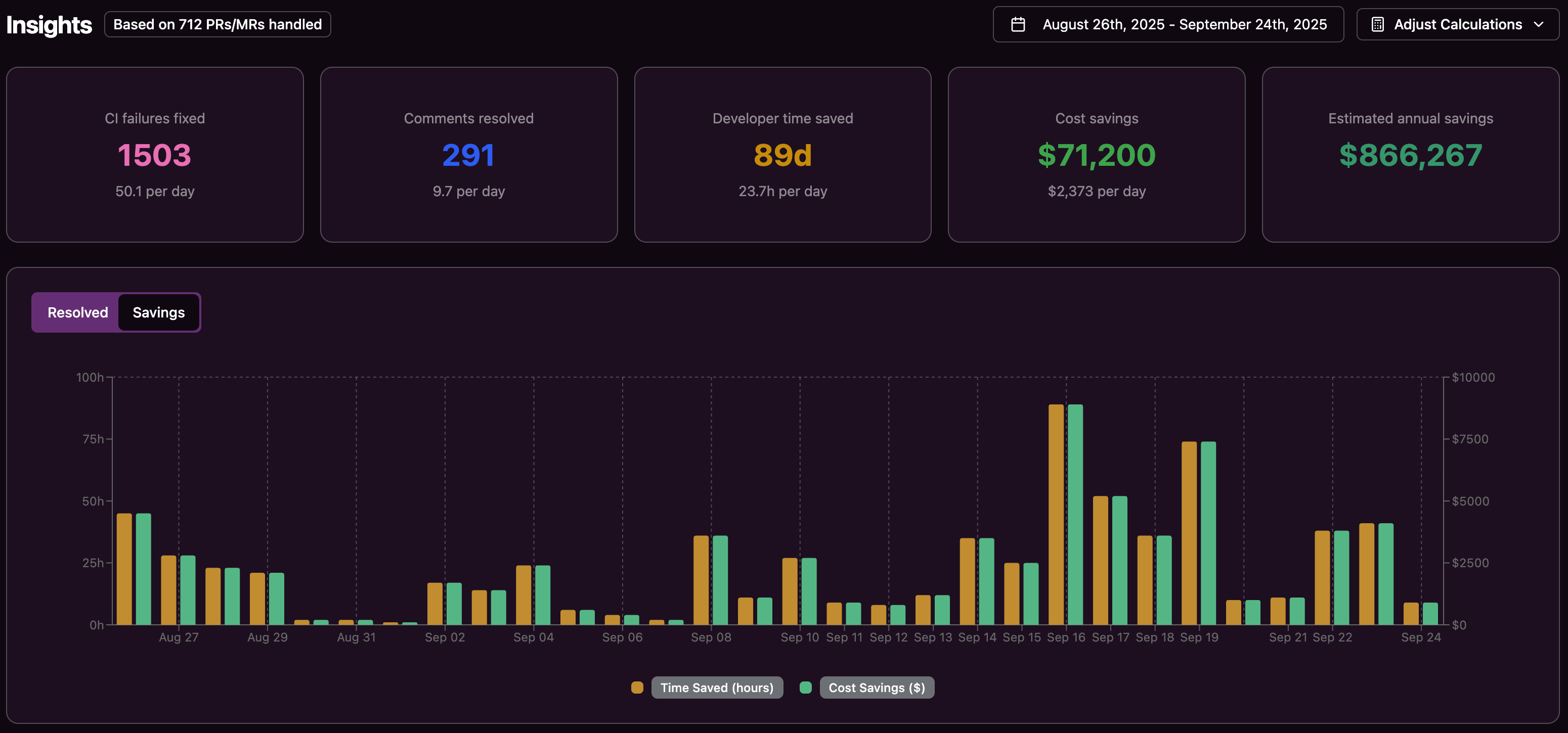
- Teams can reduce CI toil and ship faster by using Gitar to automatically fix broken builds in pull requests, while keeping developers focused on product work instead of maintenance.
The Hidden Costs of Manual Linter and Test Fixes in CI/CD
Manual linter and test fixes consume far more than the few minutes spent editing code. Each failure pulls developers out of focused work, extends pull request lifecycles, and slows release velocity.
Context Switching Drains Developer Productivity
Every failed check on a pull request drags a developer back into the old context. Recreating that mental state can take 15–20 minutes, even when the underlying fix takes only a few lines of code. Across a team, repeated CI interruptions can consume a large share of working hours, especially when developers must re-run pipelines after each attempt.
Slow Merges Delay Projects and Releases
Slow or unreliable CI runs amplify the impact of each failure and keep pull requests open longer. Every extra failure-fix cycle stretches merge time, which then delays dependent work, batched releases, and customer-facing features.
Flaky Tests and Environment Issues Create Noise
Flaky tests often pass locally but fail intermittently in CI because of timing, data, or infrastructure differences. These intermittent failures erode trust in pipeline status and encourage repeated manual retries and investigations, even when code is correct.
Distributed Teams Feel CI Pain More Strongly
Global teams experience extra delay when CI failures require back-and-forth changes across time zones. A linter issue that could be fixed in minutes can stretch into days when each change waits on remote reviewers or new CI runs, which makes autonomous fixes especially valuable for distributed organizations.
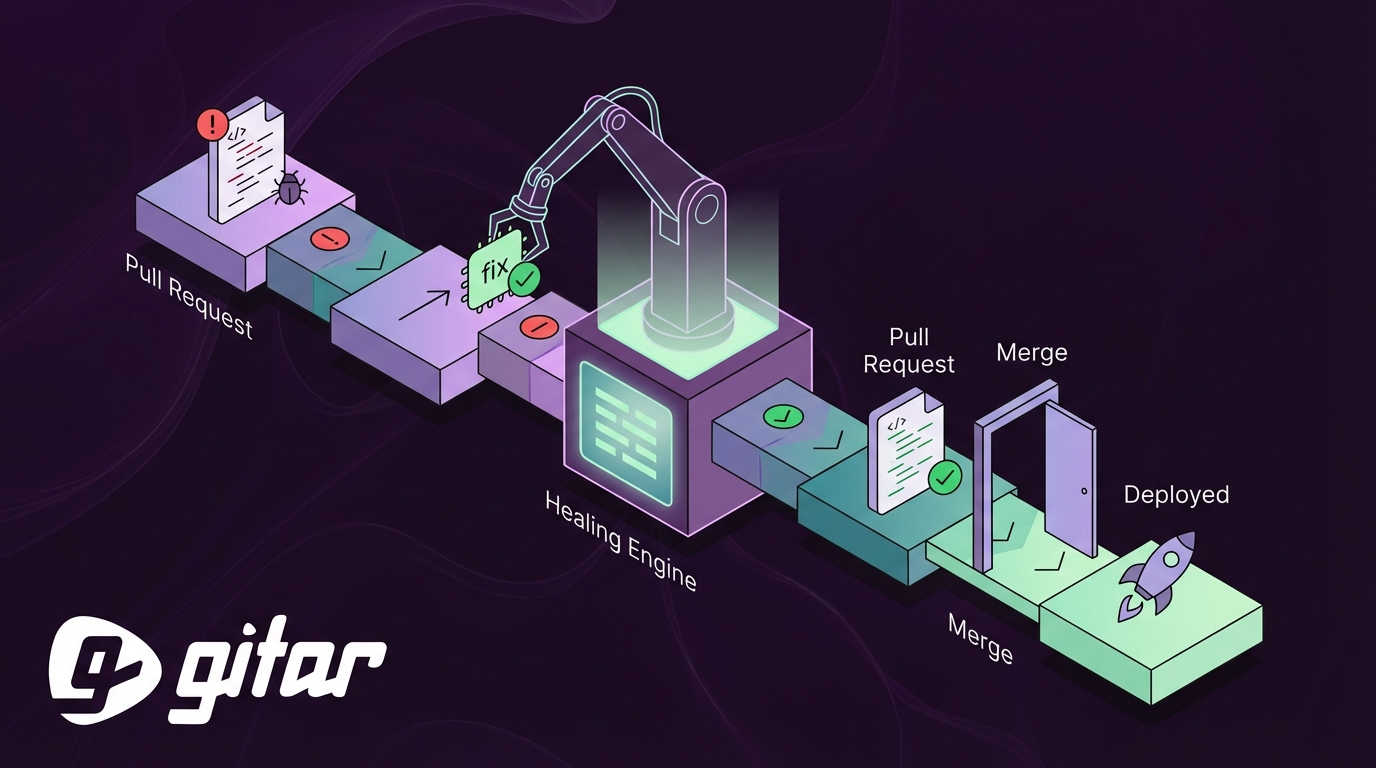
Automated Linter and Test Fix Solutions as “Healing Engines”
Automated linter and test fix solutions extend beyond static analysis or AI reviewers that only surface suggestions. Healing engines take full responsibility for closing the loop from failure to green build.
From Suggestions to End-to-End Fixing
Traditional tools highlight style problems or potential bugs, but developers still implement the changes and wait for CI. Healing engines instead analyze failure logs, propose concrete edits, apply them as commits or suggestions, and verify the result through CI. That approach removes the “last mile” of manual effort that keeps pipelines blocked.
Environment Awareness for Reliable Outcomes
Reliable automated fixes require accurate replication of CI conditions. This includes SDK versions, multi-language builds, third-party scanners, and snapshot test behavior. Environment-related failures frequently affect integration tests that depend on realistic infrastructure, so automation must operate with the same context as the real pipeline.
Common CI Issues These Tools Can Resolve
Modern systems combine static analysis and CI awareness to address a wide range of issues. Static analyzers can catch style violations, simple bugs, and some security issues, while healing engines extend this to:
- Lint and formatting violations
- Test failures that require snapshot updates or assertion fixes
- Build failures from dependency conflicts or script errors
Where Automated Fix Solutions Fit in CI Automation
Modern CI workflows have moved through several stages, from basic static analysis to AI-driven healing.
Static Analysis and AI Code Reviewers
Static analysis tools integrated into pull requests help enforce code standards and catch basic issues early. AI reviewers then add contextual comments or risk signals, yet both categories still rely on humans to implement and validate fixes. Traditional review processes also miss many runtime or environment-specific issues, which limit their impact on CI stability.
On-Demand AI Fixers
Newer LLM tools can respond to specific failure messages when manually invoked. These tools help with single issues, but they usually run inside the customer’s CI, require manual triggering, and do not manage the full environment context, which keeps them reactive rather than autonomous.
Gitar: Self-Healing CI with Automated Linter and Test Fixes
Gitar provides an autonomous AI agent that focuses on broken pull requests. The system observes CI events, understands failures, proposes edits, and verifies that pipelines return to green.
How Gitar Handles Failed Pull Requests
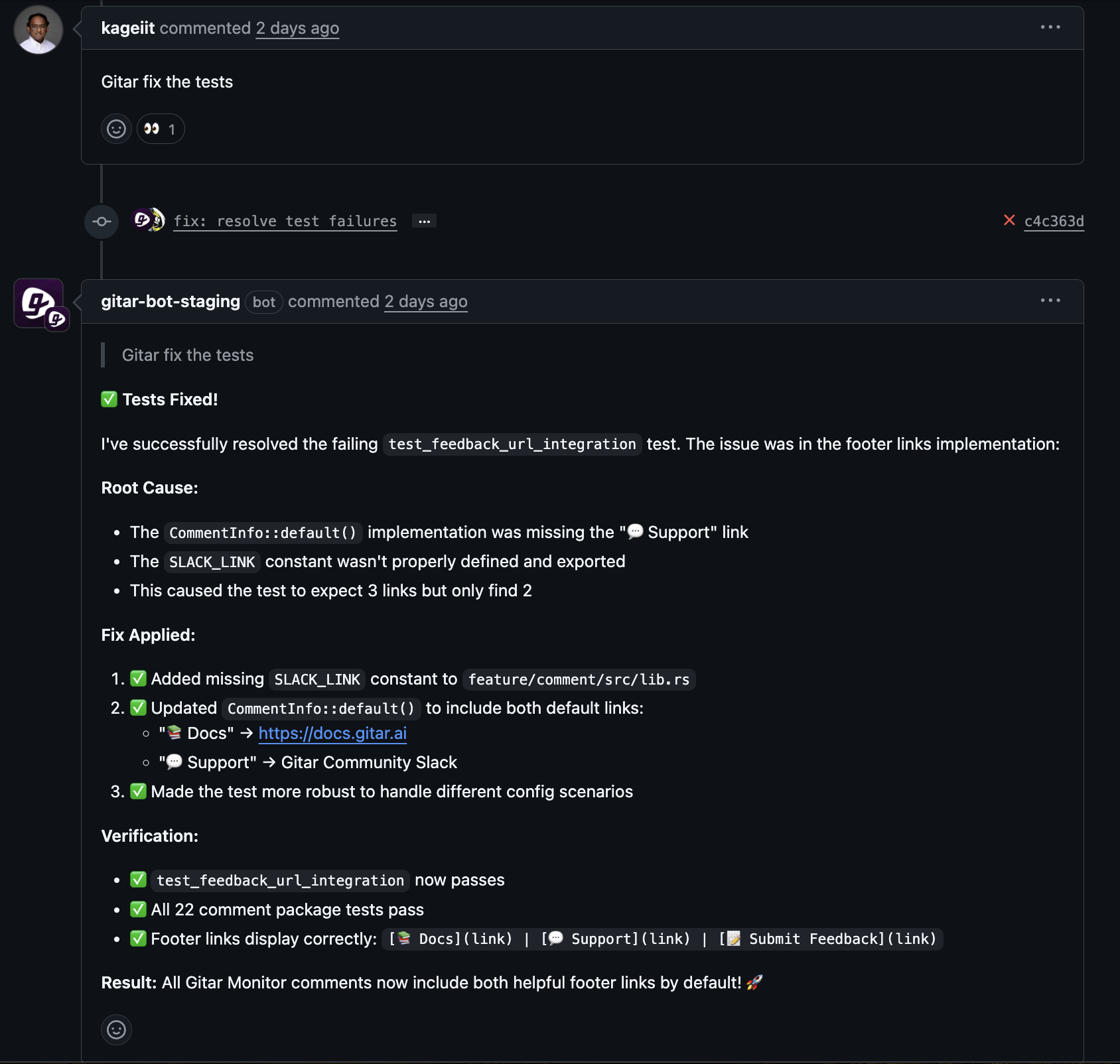
When checks such as npm run lint, pytest, or build steps fail, Gitar reads the logs, identifies root causes, and prepares precise code changes. The agent then either commits directly to the pull request branch or posts suggestions, depending on configuration, and waits for CI to re-run. This process covers linting errors, formatting issues, failing tests, and common dependency or script problems.
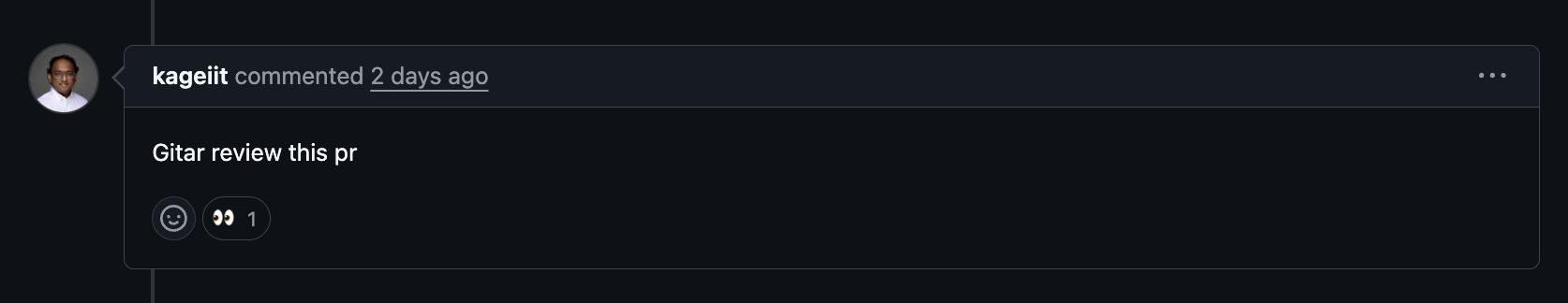
Support for Code Review Feedback
Gitar also responds to reviewer comments. A reviewer can request changes in natural language, and the agent will interpret the intent, update the code, and leave a clear explanation. This shortens back-and-forth cycles, especially when reviewers and authors work in different time zones.
Key Technical Differentiators
- Environment replication: Gitar emulates complex CI workflows, including language versions, multi-SDK builds, and tools such as SonarQube and Snyk, so fixes match real pipeline behavior.
- Action-focused agent design: The system exists to make safe edits and validate them, not just comment on problems.
- Robust event handling: A custom agent architecture manages asynchronous CI events and noisy logs while maintaining the right context for each pull request.
Implementing Automated Linter and Test Fix Solutions
Effective rollout requires more than installing a tool. Teams benefit from explicit choices about build versus buy, trust levels, and deployment phases.
Build vs. Buy Decisions
Teams that attempt to build internal healing engines must allocate engineering time for CI integrations, environment modeling, security, and long-term maintenance. Adopting a specialized product such as Gitar provides an existing architecture, multi-platform support, and continuous improvements without dedicated internal ownership.
Configurable Trust Models
Confidence in automation grows over time, not at installation. Gitar supports modes that range from suggestion-only to direct commits, with clear audit trails and rollback options. Teams often start with suggestions, then promote specific repositories or check types to fully automated fixing as they observe reliable results.
Phased Rollout
- Initial setup: Install the GitHub or GitLab app, connect CI providers, and enable conservative automation on low-risk repositories.
- Trust-building: Let developers review and accept suggested fixes, track win rates, and refine configuration based on feedback.
- Expansion: Enable direct commits for well-understood checks and extend usage to more repositories and teams, including globally distributed groups.
Feature Comparison for CI Fix Approaches
|
Feature / Tool |
Manual Work |
AI Code Reviewers |
On-Demand AI Fixers |
Gitar (Healing Engine) |
|
Solution type |
Human intervention |
Suggestion engine |
Triggered AI assistance |
Autonomous healing engine |
|
Fixes issues |
Yes, manual effort |
No, suggestions only |
Yes, when triggered |
Yes, automatically and validated |
|
CI validation |
Manual runs |
None |
Manual validation |
Automated re-validation |
|
Context switching |
High |
High |
Moderate |
Minimal |
|
Environment awareness |
Human knowledge |
Limited |
Limited |
Full CI replication |
|
Trust configuration |
Not applicable |
Not applicable |
Not applicable |
Suggestions and direct commit modes |
|
Cross-platform CI coverage |
Manual |
Often provider-specific |
Often GitHub-focused |
GitHub Actions, GitLab CI, CircleCI, Buildkite, and others |
|
Integration effort |
Ongoing manual work |
Low |
High, with custom wiring |
Low, app installation and configuration |
Avoiding Common Pitfalls During Adoption
Organizations can reduce risk and accelerate value by planning for the most frequent failure modes of CI automation projects.
Trust and Developer Involvement
Top-down rollout without developer input often meets resistance. Teams that include engineers in configuration decisions, review metrics, and feedback loops build trust faster and tune automation to real workflows.
Environment Complexity
Generic AI tools that do not replicate the full CI environment tend to produce inconsistent results. Environment-sensitive failures are common in integration and end-to-end tests, so any chosen solution should prioritize accurate environment modeling.
Distributed Team Dynamics
Fast, reliable tests help global teams trust PR status across time zones. Autonomous fixing compounds that benefit by clearing many failures before teammates even start their day, which shortens review cycles and reduces idle time.
Frequently Asked Questions About Automated Linter and Test Fix Solutions
How do these solutions handle complex enterprise CI environments?
Automated healing engines such as Gitar model complete CI workflows, including specific language versions, dependency graphs, and integrations with scanners like SonarQube and Snyk. This context allows fixes to align with how code actually runs in pipelines.
How are healing engines different from AI code reviewers?
AI code reviewers inspect code and provide comments. Healing engines like Gitar take the next steps, by editing code in response to real failures and validating the changes with CI until the pull request returns to a passing state.
What if the team is not ready for direct AI commits?
Teams can operate Gitar in conservative modes that only post suggestions. Developers review those suggestions, accept or reject them, and use observed accuracy to decide when to enable more automated options.
Conclusion: Moving Toward Self-Healing CI in 2026
Automated linter and test fix solutions turn CI from a source of friction into a system that heals many issues on its own. By reducing context switching, shortening pull request lifecycles, and handling noisy failures such as flaky tests, these tools free engineers to focus on product work.
Gitar offers an autonomous approach that understands real CI environments, applies targeted fixes, and provides configurable trust levels that match team comfort. Organizations that adopt these capabilities in 2026 gain faster release cycles, lower operational costs, and a better developer experience.