Key Takeaways
- Dependency versioning introduces ongoing security and reliability risks, especially when teams rely on large ecosystems of third-party libraries.
- Unpatched and unscanned dependencies expose CI/CD pipelines to attacks such as dependency chain abuse and dependency confusion, which can compromise entire build environments.
- Manual dependency management consumes developer time, creates context switching, and slows releases when engineers must repeatedly diagnose and fix build failures.
- AI agents can automatically analyze failing pipelines, identify root causes in dependencies, and apply validated fixes that align with the existing CI/CD environment.
- Teams can use Gitar to automatically fix broken CI builds, reduce manual toil, and keep pipelines stable.
The Problem: The Hidden Costs and Dangers of Manual Dependency Management
Manual dependency management creates a significant bottleneck in CI/CD pipelines and increases both security and operational risk. Dependency chain abuse occurs when malicious actors inject vulnerabilities into external dependencies like libraries, propagating security flaws through CI/CD pipelines. These compromised dependencies can produce unexpected behavior and exploitable security gaps, and the Equifax breach due to a missed Apache Struts update highlights the real-world consequences from unpatched open-source libraries.
Unmanaged and unscanned third-party code compounds the problem over time. Unscanned dependencies, such as outdated libraries unchecked for months, pose significant risks, especially as new vulnerabilities surface. More targeted threats exploit package ecosystems directly, and dependency confusion attacks trick package managers into fetching compromised libraries by publishing malicious packages with names resembling legitimate ones. The OWASP Top 10 CI/CD Security Risks calls out real incidents where compromises of popular NPM packages like ua-parser-js, coa, and rc affected millions of downloads, resulting in malicious code execution in build environments.
These risks land directly on developers. Teams spend hours tracking library versions, running scans, and resolving flagged issues, often under tight deadlines. Each dependency-related failure forces a context switch away from product work, so a small fix that should take minutes often stretches into an hour of debugging, investigation, and verification. Over weeks and months, this overhead slows release cadence and contributes to burnout.
The Solution: Introducing Gitar for Autonomous CI Fixes
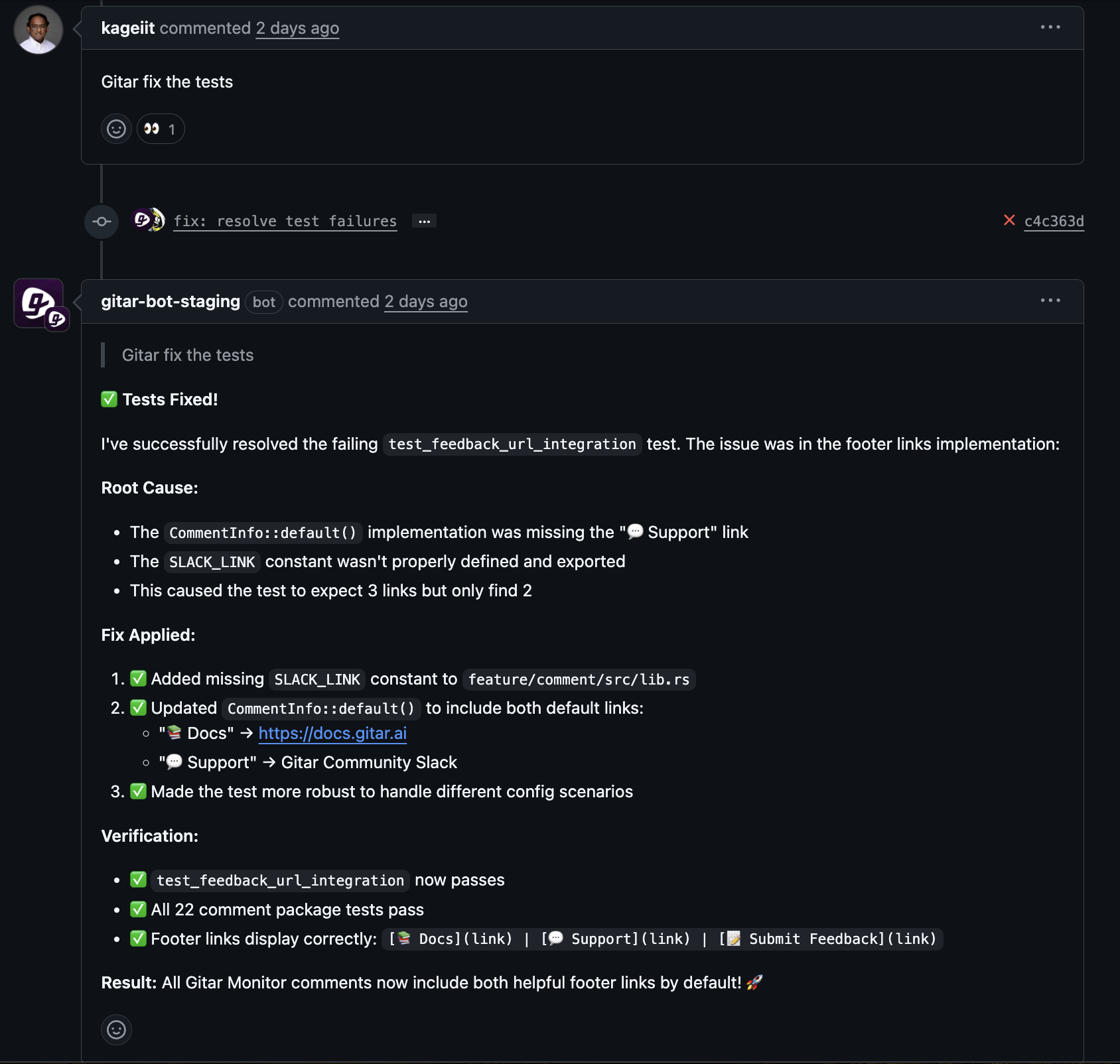
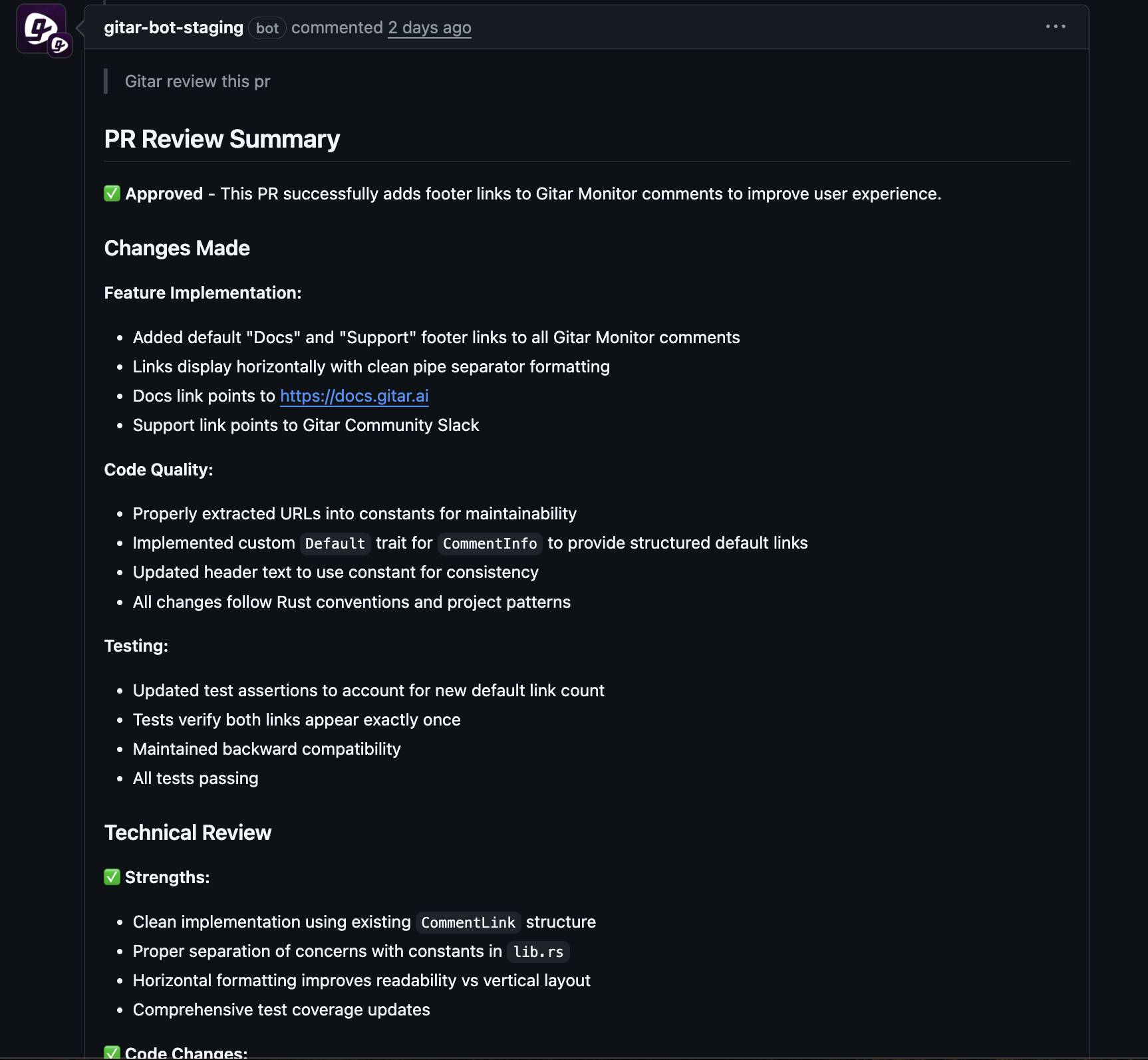
Gitar is an autonomous AI agent that improves how engineering teams handle CI/CD pipeline failures, including those related to dependency issues. When a pipeline fails because of a build or dependency problem, the Gitar agent analyzes the logs and environment, identifies the root cause, generates a fix, and updates the pull or merge request with the change.
Key features that help Gitar improve CI/CD workflows include:
- End-to-end autonomous fixes: Gitar can move beyond suggestions, apply fixes, run them through the full CI workflow, and aim for green builds before developers need to stop what they are doing.
- Full environment replication: Gitar emulates complex enterprise workflows and dependency graphs so fixes align with how your CI actually runs, not just with local assumptions.
- Configurable trust model: Teams can start in conservative modes where Gitar suggests fixes for review, then shift to auto-commit modes with rollback options once they are comfortable with the automation.
Install Gitar to automatically fix broken builds and reduce manual CI maintenance work.
The Benefits: Streamlining CI/CD Workflows with AI-Assisted Fixes
Accelerated Development Velocity and Reduced Toil
Build failures often consume a large share of developer time. Each failure requires triage, log analysis, and patching, especially when dependency version conflicts or security flags appear late in the pipeline.
Gitar reduces this toil by handling many of these steps in the background. The agent can:
- Detect and analyze failing jobs without waiting for manual investigation.
- Propose or apply code and configuration changes that address dependency and build issues.
- Re-run CI checks to confirm the fix before asking for human review in conservative modes.
This approach helps teams reclaim hours that would otherwise be spent on repetitive debugging. Developers can focus on feature work, code quality, and design, while CI issues become a manageable background task instead of a constant interruption.
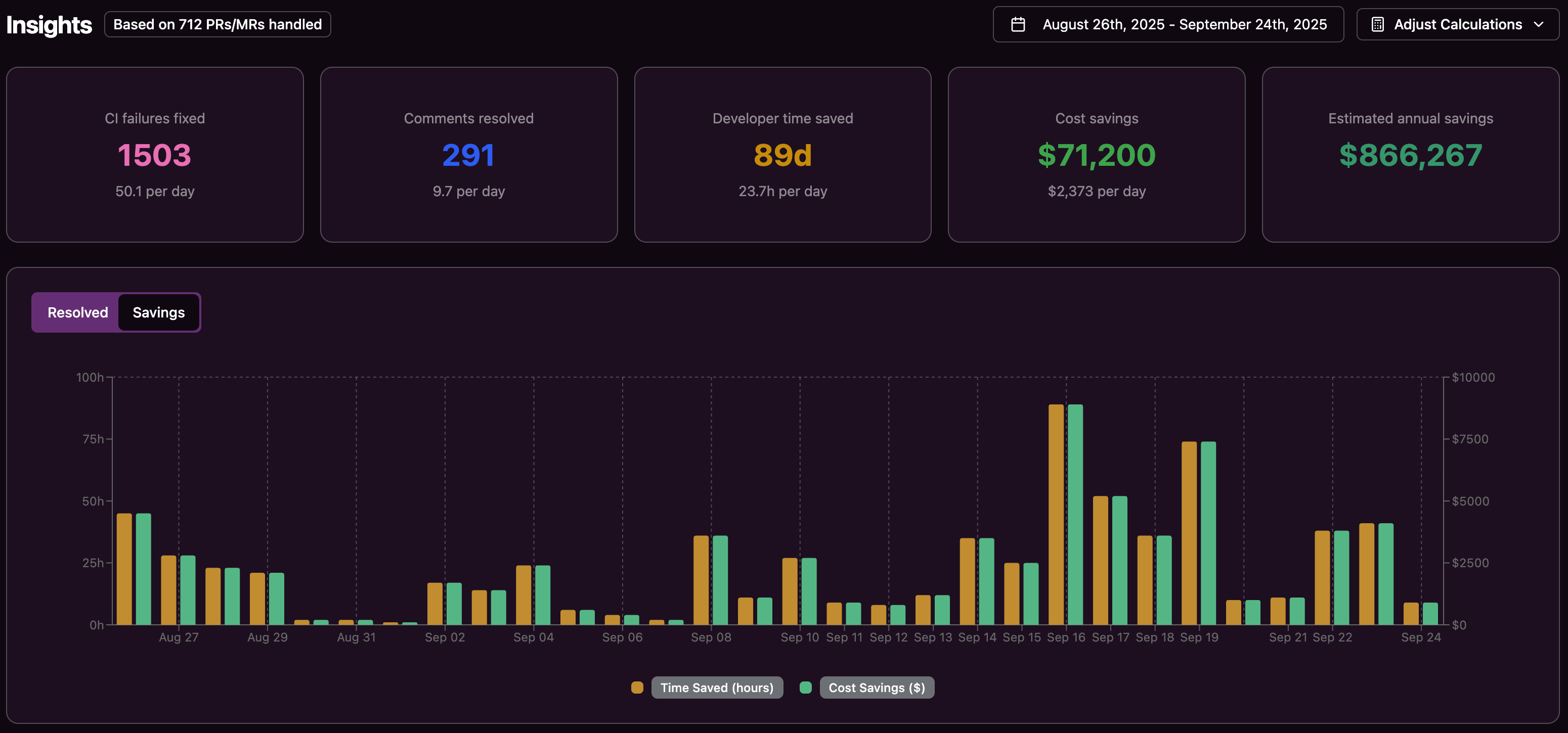
Ensuring Pipeline Stability and Reliability
Pipeline stability depends on how quickly teams can detect and correct failures. Unstable builds slow releases and make it harder to trust CI results, especially when dependency changes break tests or introduce subtle regressions.
Gitar uses full environment replication to validate each fix against the same workflows your CI system uses. The agent tests proposed changes with the relevant SDK versions, dependency sets, and pipeline configuration. This process helps:
- Reduce flaky or intermittent failures tied to dependency issues.
- Prevent regressions by validating fixes in context.
- Keep the main branch stable and ready for deployment.
The result is a CI/CD pipeline that behaves more like a self-correcting system and less like a fragile chain of manual checks.
Comparison: AI-Powered CI Fixes vs. Traditional Methods
|
Feature |
Manual CI Management |
AI-Powered Fixes (Gitar) |
|
Issue detection |
Periodic manual investigation, usually reactive after failures pile up |
Automatic detection with proactive analysis and fixes |
|
Fix implementation |
Manual developer intervention and repeated context switching |
Autonomous or suggested fixes that can be applied with minimal human effort |
|
Build stability |
Frequent unexpected failures and longer time to green builds |
Higher stability as fixes are validated against the full CI environment |
|
Developer productivity |
Significant time spent on debugging and maintenance tasks |
More time for core feature work and design, less time on repetitive CI issues |
Install Gitar to enhance CI/CD workflows and keep builds running smoothly.
Frequently Asked Questions (FAQ)
How Gitar handles complex enterprise CI/CD environments
Gitar replicates full enterprise workflows so fixes align with real-world conditions, not simplified test cases. The agent works with specific SDK versions and multi-SDK dependencies, and it keeps track of context across jobs and users. It also processes events, handles retries, detects duplicates, and maintains consistent state even when CI environments generate noisy or overlapping signals.
How teams can control trust and automation levels with Gitar
Teams that do not yet want fully autonomous commits can start with a conservative trust model. In this mode, Gitar posts suggested fixes as comments or pull request updates and waits for explicit approval. Approvers can accept changes with a single click and gain visibility into how the agent reasons about failures.
Once the team is comfortable with the quality of fixes, they can switch to more automated modes. These modes support direct auto-commits, while maintaining rollback options so changes remain under control. This gradual path allows organizations to adopt AI assistance at a pace that fits their risk tolerance and review processes.
Gitar support for CI/CD platforms beyond GitHub
Gitar is designed to work with a range of CI/CD platforms and toolchains, which provides flexibility for organizations that use multiple systems. Compatibility details and integration guidance are available through documentation and support channels, so teams can understand how Gitar fits into their specific stack before rollout.
Conclusion: Accelerate Your Development with AI-Driven CI Fixes
Managing CI/CD pipelines through manual effort alone places a heavy load on engineering teams. Dependency updates, security fixes, and build failures all compete with feature work and can slow project delivery when handled case by case.
Gitar uses AI to identify and resolve many CI pipeline failures, including those created by dependency issues, so engineers can spend less time on routine maintenance. The agent turns recurring problems into structured, automatable tasks and gives teams clearer insight into how their pipelines behave over time.
Organizations that move from ad hoc CI management to AI-assisted workflows can gain measurable benefits, including reduced downtime, faster time-to-merge, and improved developer satisfaction. These gains become especially visible in large codebases with frequent dependency changes or complex build matrices.