Software development today moves at a rapid pace, often fueled by AI tools and faster delivery cycles. With this speed comes a pressing need to embed strong security practices into every part of the CI pipeline. Vulnerabilities like broken access control, cryptographic errors, injection attacks, insecure designs, misconfigurations, and outdated components frequently cause CI build failures, slowing down engineering teams.
This guide is for engineering leaders, managers, and developers who want actionable steps to tackle CI failures and boost code security. You’ll learn how AI tools like Gitar can streamline remediation, cut down on manual work, and help your team deploy code faster with fewer errors.
Why Security-Related CI Failures Matter More Than Ever
How Insecure Code and CI Issues Drain Resources
CI build failures cost more than just time. For a team of 20 developers, these issues can eat up hours, adding up to around $1 million in lost productivity each year. Beyond the numbers, delays in projects and rising costs hurt your ability to stay competitive in the market.
When a build fails, developers have to stop what they’re doing, analyze logs, and fix the problem. A small issue that should take minutes can stretch into hours due to the mental shift and effort required. This disruption kills focus and slows down progress.
For distributed teams, the problem gets worse. A developer in one time zone might submit a pull request that fails, needing input from a teammate halfway across the world. What could be a quick fix turns into days of waiting, further delaying critical updates.
Common Security Issues Behind CI Failures
Today’s CI pipelines face a range of security threats that directly cause build issues. Key vulnerabilities include:
- Broken access control, cryptographic errors, injection attacks like SQL or prompt injection, insecure designs, misconfigurations, and outdated components.
- Software and data integrity risks specific to CI/CD pipelines, along with authentication failures and vulnerable components, as noted in the OWASP Top Ten.
With API-first and microservices setups becoming standard, new access and authentication threats emerge, requiring advanced detection in CI workflows. Reliance on third-party and AI-generated code also heightens supply chain risks, making automated component analysis a must.
CI/CD Pipelines as a Target for Attacks
CI/CD pipelines are now a prime target for attackers. A breach here can mean malicious code injection, stolen API keys, or unauthorized deployment changes, risking malware or data leaks.
Misconfigurations in cloud-based CI/CD setups are a major cause of breaches, so constant validation is critical. Code flaws such as buffer overflows and insecure deserialization can open doors to remote code execution if not caught early in CI testing. Traditional tools often spot these issues but leave the time-consuming fixes to developers, creating delays and added costs.
How to Build Security into Your CI Workflow
Prevent Issues Early with Threat Modeling
Stopping security-related CI failures starts before coding even begins. Focus on threat modeling during the design phase to spot potential weaknesses in your application. This early step reduces the chance of major issues popping up during builds, when fixes cost more time and effort.
Adopt security-by-design principles to weave protective measures into every stage of development. Clear coding standards and design patterns help keep common vulnerabilities out of your codebase, cutting down on CI failures and easing the burden on your team.
Use Automated Security Testing for Quick Detection
Embedding automated security checks in your CI pipeline catches problems early. Consider these key areas:
- Static Testing (SAST): Scans source code for issues like buffer overflows or injection risks without running the app, ideal for early CI stages.
- Dynamic Testing (DAST): Tests running apps to find runtime flaws, complementing static scans by catching issues like authentication gaps.
- Component Analysis (SCA): Maps out third-party dependencies to flag known vulnerabilities, essential with apps often relying on 70-90% external code.
Want to stop wasting time on manual CI fixes? Install Gitar to automate build repairs and ship better code faster.
Secure Configurations and Data Integrity
Protecting your CI pipeline also means securing how it’s set up. Focus on these practices:
- Infrastructure as Code (IaC): Validate configurations continuously to spot issues before they’re exploited, ensuring consistent, safe deployments.
- Access Controls (IAM): Use multi-factor authentication and monitor API security to block unauthorized access in CI/CD systems.
- Data Integrity: Verify code integrity with signing and secure updates to prevent tampering during builds.
Protect Your Supply Chain in CI Pipelines
Third-party components dominate modern apps, so supply chain security is vital. Generate a Software Bill of Materials (SBOM) to track every piece of code in use. This visibility helps you act fast if a vulnerability surfaces in a dependency.
Using private package repositories adds control over which components enter your builds. Pair this with automated scanning to block known risks. Strategies like dependency pinning and testing updates in isolated setups also help balance security with stability, avoiding unexpected breaks.
Why AI Changes the Game for CI Fixes with Gitar
Where Traditional Tools Fall Short
Most CI tools detect issues and alert developers, leaving the hard part, fixing the problem, to the team. Developers then switch tasks, dig into the issue, find a solution, apply it, and check if it works. This process steals time and focus, especially if specialized skills are needed.
Even AI tools that suggest fixes often require manual steps to test and apply them. If the suggestion doesn’t match the codebase or environment, developers still face trial and error, keeping productivity losses high.
Automate Fixes with Gitar’s AI-Driven Approach
Gitar shifts CI remediation from manual effort to automatic solutions. Instead of just pointing out failures, it analyzes the root cause, creates a fix, and applies it. This covers issues like linting errors, test failures, and build problems tied to dependencies.
With Gitar, developers stay focused on their main tasks while the tool resolves routine CI hiccups. It’s like having an extra teammate dedicated to keeping builds running smoothly.
What Gitar Brings to Your CI Process
Gitar offers specific benefits to make CI smoother and faster:
- Complete Fix Validation: Applies fixes and runs full CI checks to ensure builds pass, removing guesswork from solutions.
- Environment Matching: Mirrors complex setups with specific SDKs and dependencies, ensuring fixes work in your real CI context.
- Flexible Automation: Starts with suggestion mode for review, then scales to full automation for routine fixes as trust grows, with manual control for critical changes.
Ready to turn CI failures into quick wins? Install Gitar now to automate fixes and deliver quality code faster.
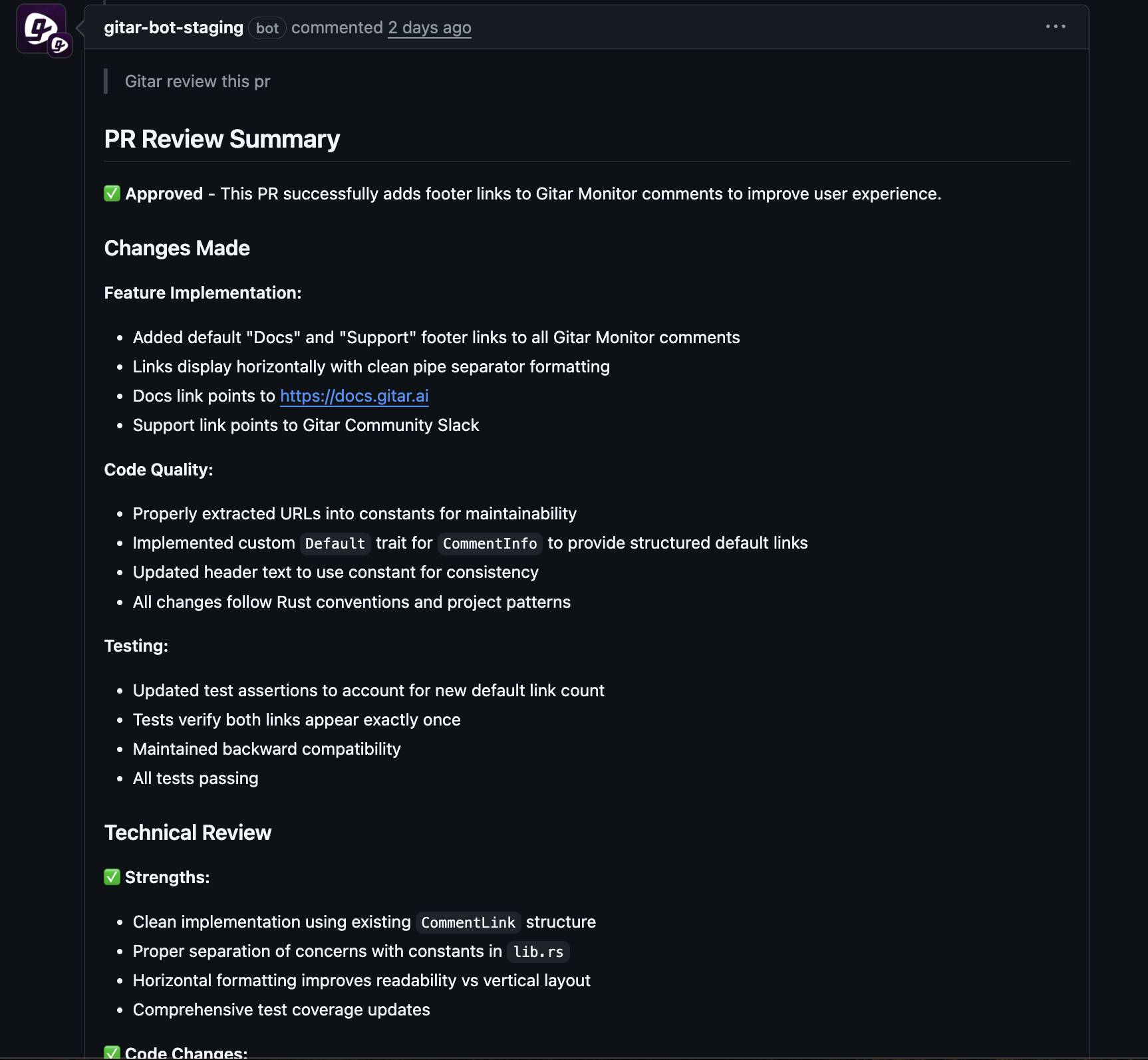
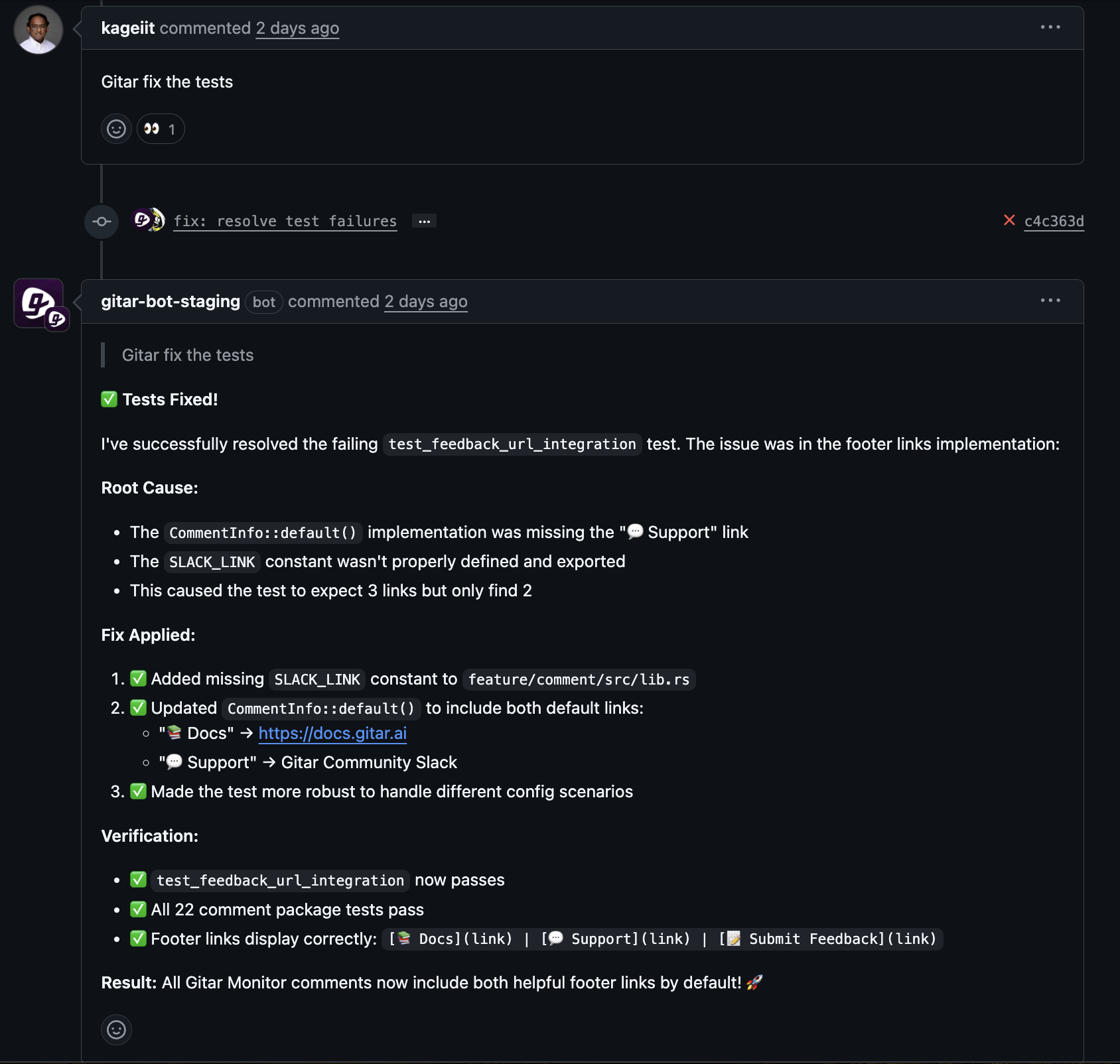
Steps to Build a Self-Healing CI with Gitar
Your Path to Fewer CI Failures
Getting started with Gitar involves a clear, phased approach:
- Phase 1 – Setup and Trust: Install Gitar as a GitHub App on chosen repositories via a web dashboard. Begin with suggestion mode, where fixes need approval, building confidence as it handles linting and test issues.
- Phase 2 – Increased Automation: After seeing reliable fixes, allow Gitar to commit solutions for common issues. Fixes happen in minutes, not hours, without waiting for developer input.
- Phase 3 – Proactive Improvements: Use Gitar to address code review feedback and apply fixes across time zones, preventing delays and boosting workflow efficiency.
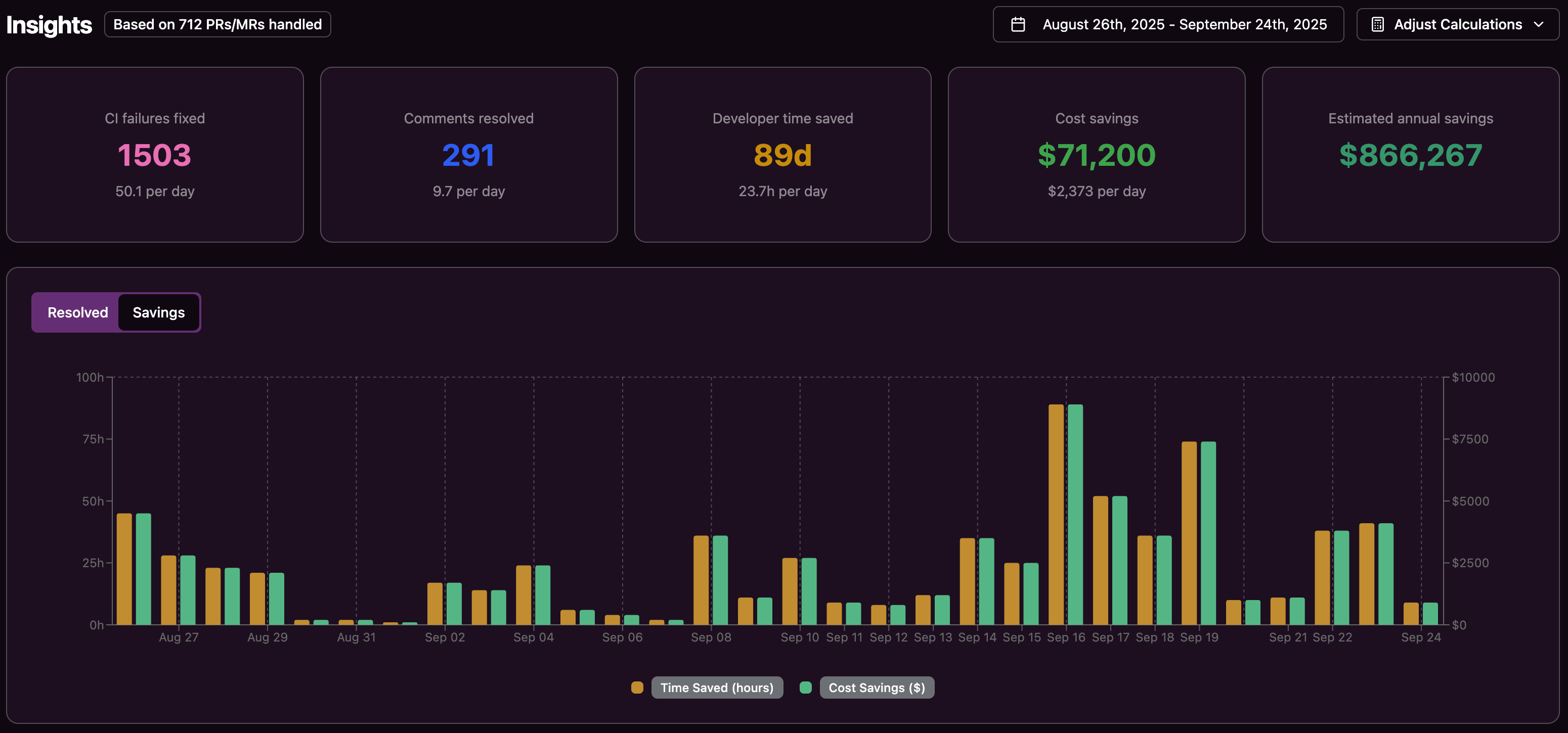
Track ROI and Financial Gains
Automating CI fixes saves more than just time. For a 20-developer team, Gitar can cut down significant debugging hours yearly. At $200 per hour, this adds up to major cost reductions while improving code quality and team morale.
Faster fixes also speed up project timelines and lower overhead. When issues resolve automatically, delivery stays consistent, and developers feel less frustrated, focusing on meaningful tasks instead of repetitive debugging.
Avoid Common Automation Mistakes
Rolling out automated CI fixes needs careful planning. Make sure developers see Gitar as a helper, not a replacement, by explaining its role and limits. Regularly check the quality of fixes and adjust automation levels based on feedback to keep standards high.
Ensure Gitar fits into existing workflows without conflict. Thoughtful integration aligns automated fixes with your broader development goals and policies, avoiding disruptions.
Comparing Gitar to Other CI Fix Approaches
|
Feature |
Gitar (AI Autonomous Fixes) |
AI Code Reviewers (e.g., CodeRabbit) |
Manual Developer Fixes |
|
Fix Execution |
Applies and validates fixes, ensures builds pass |
Suggests fixes, sometimes with one-click apply, but validation may be needed |
Developer identifies, applies, and validates manually |
|
Environmental Context |
Replicates full CI setup for accurate fixes |
Good awareness with code and repository analysis |
Depends on developer’s local setup and knowledge |
|
Developer Effort |
Cuts out manual debugging and task switching |
Reduces some effort, but validation can still be manual |
High effort, frequent switching, productivity loss |
|
Fix Time |
Minutes from issue detection to fix |
Hours to days based on developer availability |
Hours to days for research and application |
Gitar stands out by handling the entire fix process, from spotting issues to ensuring builds pass. Unlike suggestion tools or manual fixes, it removes the final steps of implementation and testing from developers, saving time and reducing interruptions.
Don’t let CI failures hold your team back. Install Gitar to automate fixes and keep your development on track.
Common Questions About Code Security and CI Fixes
Which Security Issues Most Often Cause CI Failures?
Frequent culprits include broken access control, cryptographic errors, injection attacks like SQL, insecure design, misconfigurations, and outdated components. Integrity issues in CI/CD pipelines are also a growing concern, especially with heavy use of third-party and AI-generated code introducing new risks.
How Does AI Improve CI Fix Efficiency?
AI tools like Gitar go beyond spotting issues by automatically fixing them. Unlike traditional tools that leave implementation to developers, Gitar analyzes failures, creates tailored fixes for your codebase, and validates them in your CI environment. This cuts hours of manual work down to instant solutions.
Is It Safe to Let AI Fix CI Issues Automatically?
Automation safety relies on adjustable trust settings. Gitar lets teams start with suggestion mode, reviewing every fix before approval. As confidence builds with reliable results, you can shift to more automated fixes while keeping rollback options and audit logs for oversight.
How Does Gitar Work with Existing CI/CD Tools?
Gitar integrates easily with platforms like GitHub, GitLab, GitHub Actions, CircleCI, and BuildKite. It supports languages such as Python, Go, JavaScript, Java, and Rust, fitting diverse setups. Rather than replacing tools, it automates fixes for issues they detect, enhancing efficiency without disrupting workflows.
Which CI Failures Can AI Fix on Its Own?
AI excels at handling routine CI issues like linting errors, simple test failures, and build issues from dependencies or scripts. Complex architectural problems or unique failures still need human input. Combining AI for everyday fixes with developer expertise for bigger challenges works best.
Wrap-Up: Speed Up Development with AI-Powered CI Fixes
Modern engineering teams face the challenge of maintaining strong workflows while pushing for faster delivery. Manual CI fixes no longer keep up with today’s tight schedules. Tools like OWASP Top Ten benchmarks can guide CI/CD security, but you need more than detection. Automated remediation is the next step.
Gitar turns CI obstacles into effortless fixes, creating a self-healing workflow. It resolves build failures, tests solutions in your full environment, and offers flexible automation levels, letting your team focus on building rather than troubleshooting.
The benefits go beyond saved time. Automated fixes cut costs, improve developer satisfaction, and get features to market quicker. In a field where speed and reliability matter, streamlining CI issues gives your team a clear edge.
Ready to simplify CI failures and empower your developers? Install Gitar today to automate fixes and deliver better software faster.