Key Takeaways
- Optimized CI/CD pipelines in 2026 reduce costly build failures, context switching, and review delays that slow shipping schedules.
- Five practices matter most for stable delivery: shift-left security, GitOps for infrastructure, comprehensive automated testing, progressive delivery, and Environment-as-a-Service.
- Autonomous tooling that fixes CI failures and applies review feedback protects developer focus and shortens time to merge.
- Teams that standardize these practices gain more predictable releases, lower change failure rates, and better use of cloud and infrastructure spend.
- Gitar provides autonomous CI fixes and code review support, helping teams adopt these practices without adding manual overhead. Install Gitar to turn broken builds into automatic fixes.
Why CI/CD Optimization Protects Productivity in 2026
The Business Cost of Inefficient CI/CD
Inefficient CI/CD pipelines drain engineering and financial resources. Developer time lost to failed builds and slow reviews can reach hundreds of thousands of dollars per year for a mid-sized team. Project delays impact most software organizations when pipelines block merges or releases. A short fix often expands into an hour of lost focus once context switching and pipeline reruns are included.
These issues also affect cloud bills and customer trust. Repeated CI retries consume compute resources, while delayed releases slow delivery of improvements and bug fixes. Frequent interruptions and manual log debugging contribute to burnout and high turnover in engineering teams.
The Shift Toward Autonomous, Streamlined CI/CD
AI-generated code has moved the bottleneck from writing code to validating, reviewing, and merging it. Modern CI/CD optimization focuses on shortening this validation loop with smart automation. Autonomous systems now analyze logs, identify root causes, and propose or apply fixes, so developers can stay focused on feature work.
Teams that adopt these patterns build self-correcting pipelines where common issues resolve quickly, and manual work is reserved for complex changes or architectural decisions. The five best practices below create the structure for that outcome.
Gitar: Autonomous Fixes for CI/CD Bottlenecks
How Gitar Fits Into Your Delivery Workflow
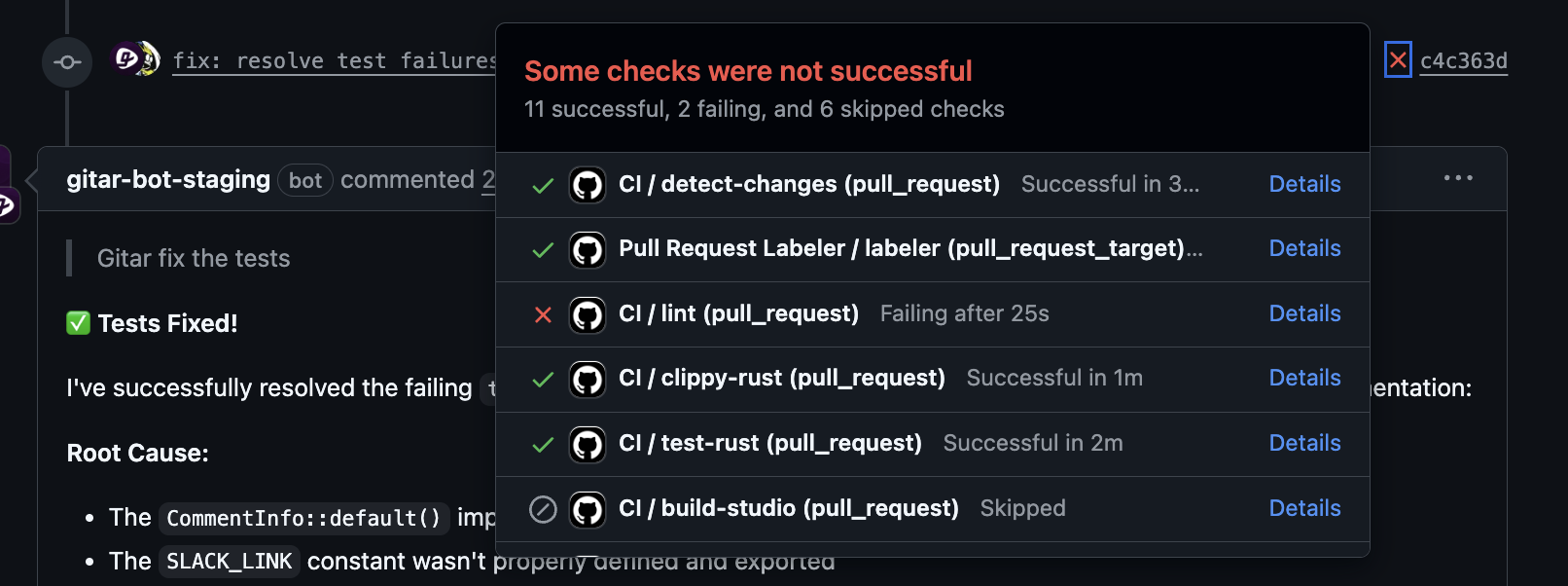
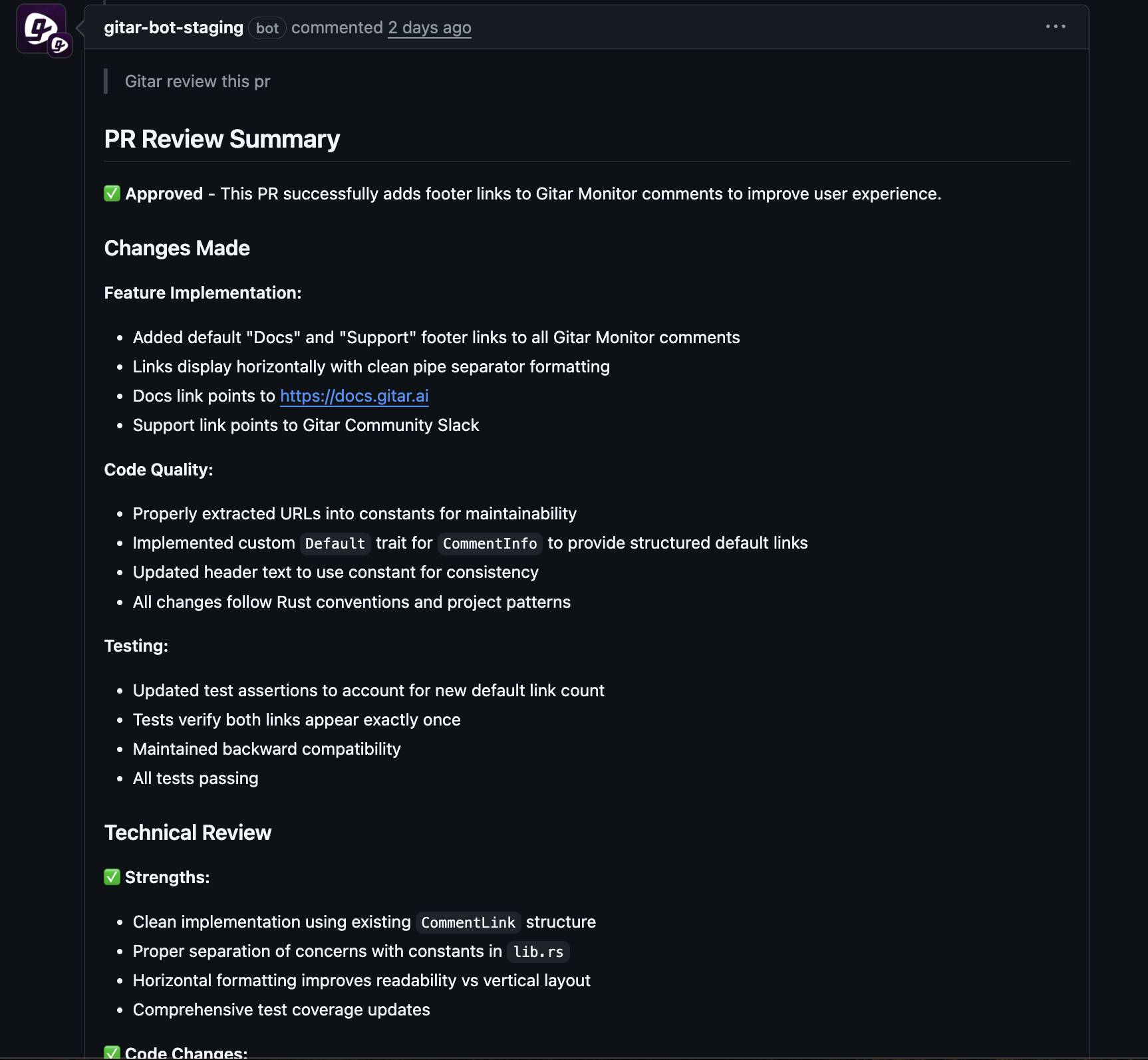
Gitar acts as an autonomous CI assistant that fixes failing builds and implements code review feedback. When a pull request fails because of lint errors, test failures, or build issues, Gitar analyzes the logs, identifies the cause, generates a targeted fix, and commits the change back to the branch.
This approach removes the usual loop where developers pause their current task, study CI logs, patch the code, and wait through another pipeline run. Teams gain faster feedback, more stable branches, and fewer interruptions. Install Gitar to automatically fix broken builds and keep developers focused on shipping features.
Key Capabilities of Gitar
- Autonomous CI fixes that resolve lint, test, and build failures with full environment replication for context-aware changes.
- Code review assistant that applies requested changes and improvements directly in the pull request.
- Configurable trust levels, from suggestion-only mode to auto-commit with rollback options.
- Support for platforms such as GitHub Actions, GitLab CI, CircleCI, and BuildKite without requiring migration.
- Enterprise-ready environment handling that works with specific SDK versions, complex dependency graphs, and security scanners.
1. Shift-Left Security for Earlier, Cheaper Fixes
Why Early Security Checks Matter
Security checks that run early in the CI/CD pipeline with AI-driven prioritization and automated rollback reduce the chance that vulnerabilities reach production. Fixing issues near design or implementation costs far less than patching incidents after deployment.
Embedding security into routine workflows prevents security debt from building up and reduces the need for emergency responses that disrupt roadmaps and damage trust.
Practical Steps for Shift-Left Security
- Add SAST, DAST, and SCA checks to every commit or pull request.
- Use pipeline gates that block merges when security thresholds are not met.
- Surface security findings in IDEs and pull requests so developers see them alongside regular code feedback.
How Gitar Keeps Security Pipelines Moving
Gitar helps when security tools break builds for fixable issues. If a scan flags outdated dependencies with known upgrade paths, Gitar can parse the scan output, update the affected libraries, and commit the changes. Security policies stay enforced while developers avoid time-consuming dependency cleanup.
2. GitOps for Reliable Infrastructure as Code
Why GitOps Improves Infrastructure Stability
Managing infrastructure as code in Git with tools like Terraform, Argo CD, or Flux creates a single source of truth. Every change is versioned, reviewed, and traceable, which lowers the risk of manual misconfiguration and speeds up reproducible deployments.
Declarative GitOps workflows also support automatic drift detection, so teams know when live infrastructure no longer matches the desired state stored in repositories.
Practical Steps for GitOps
- Store all infrastructure definitions in Git with clear branching and review rules.
- Trigger validation pipelines for each pull request to test configuration changes.
- Set up drift detection that alerts or reconciles when real state diverges from Git.
How Gitar Supports GitOps Pipelines
Infrastructure-as-code pipelines fail for reasons such as format mistakes, invalid schemas, or mis-typed resource definitions. Gitar can diagnose these failures from CI logs, correct the problematic files, and commit fixes so DevOps teams spend less time on routine infrastructure errors and more on architecture and reliability.
3. Comprehensive Automated Testing and Quality Gates
Why Testing Coverage Protects Releases
Layered test suites and strict quality gates reduce the chance that defects reach users. Teams with strong automated testing practices see lower defect escape rates and faster recovery when issues appear.
Consistent gates on coverage, performance, and critical checks create predictable criteria for a merge or release, which supports frequent and dependable deployments.
Practical Steps for Automated Testing
- Include unit, integration, and end-to-end tests in CI with clear pass and fail rules.
- Use branch protection so pull requests cannot merge until required checks succeed.
- Apply test parallelization and selective test runs to keep pipelines fast.
How Gitar Reduces Testing Friction
Many failures come from brittle tests, snapshot mismatches, or simple syntax errors. Gitar reviews the failing logs, updates snapshots when appropriate, fixes assertions or syntax, and commits the changes. Developers avoid time-consuming test cleanup while pipelines still enforce strict quality standards.
4. Progressive Delivery and Feature Flags for Safer Releases
Why Progressive Delivery Lowers Risk
Separating deployment from release with canary rollouts, blue-green strategies, and feature flags lets teams ship code frequently while controlling exposure. New features reach small user segments first, which limits blast radius and supports data-driven rollout decisions.
Progressive delivery also makes rollback simple, because disabling a feature flag or shifting traffic is faster and safer than a full rollback of infrastructure or application versions.
Practical Steps for Progressive Delivery
- Use a feature flag platform to target features to specific users, regions, or cohorts.
- Adopt rolling or canary deployment patterns with clear rollback triggers.
- Instrument releases with metrics on errors, latency, and key business outcomes.
How Gitar Keeps Progressive Delivery Unblocked
Feature flag logic can introduce new dependencies, branch conditions, or lint violations that break CI. Gitar identifies these issues in logs, fixes flag-related code problems, and commits patches so progressive delivery systems receive healthy builds without added review delays.
5. Environment-as-a-Service for Consistent Testing
Why On-Demand Environments Speed Development
On-demand environments based on containerization and Infrastructure as Code let teams spin up realistic stacks quickly for each branch or pull request. This approach reduces the classic “works on my machine” problem and keeps development, staging, and production aligned.
Standardized ephemeral environments also support parallel workstreams and simpler onboarding, since new engineers can start work without weeks of manual setup.
Practical Steps for Environment-as-a-Service
- Use Docker and Kubernetes or similar tools to define consistent, portable environments.
- Apply Terraform, Ansible, or related tools to automate environment provisioning.
- Provision temporary environments per branch or pull request for isolated testing.
How Gitar Improves EaaS Stability
Even with strong environment patterns, builds still fail because of Dockerfile mistakes, misordered setup steps, or environment-specific tests. Gitar recreates enterprise CI environments to understand these failures in context, then applies targeted fixes. New and existing team members spend less time diagnosing environment quirks and more time delivering features.
Conclusion: Make CI/CD Best Practices Practical With Autonomy
These five CI/CD best practices form a solid baseline for modern software delivery in 2026. Shift-left security, GitOps workflows, robust automated testing, progressive delivery, and Environment-as-a-Service improve reliability and speed, but they can also add complexity and more CI checks that need attention.
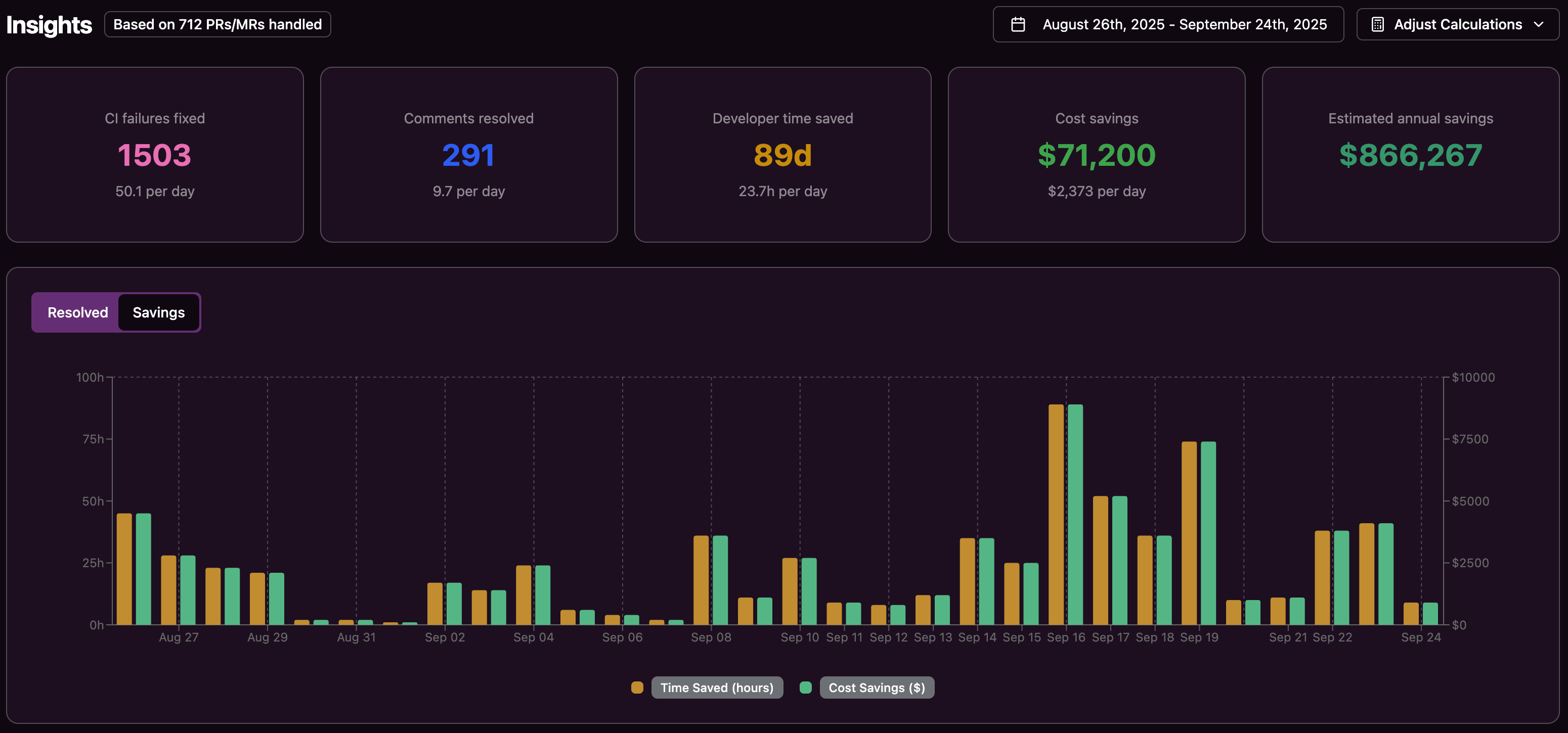
Gitar helps teams realize the value of these practices without adding more manual work. By fixing CI failures, addressing code review comments, and keeping pipelines green, Gitar turns CI/CD from a recurring source of interruptions into a predictable and largely autonomous system. Install Gitar to reduce CI toil and support faster, more reliable releases.