Key Takeaways
- Manual CI/CD security remediation cannot keep up with the growing volume and severity of vulnerabilities, especially as attackers weaponize new CVEs within hours.
- Suggestion-only CI/CD security tools add noise and context switching for developers instead of closing the remediation gap.
- Autonomous AI that can understand, fix, and validate changes in real CI environments reduces developer toil and speeds up time-to-merge.
- Self-healing pipelines improve security outcomes, control remediation costs, and protect developer focus by removing repetitive security firefighting.
- Teams can adopt Gitar to automatically fix CI/CD security and quality issues while keeping full control over how changes are proposed and applied: Install Gitar for autonomous CI/CD remediation.
The Problem: The High Cost of Manual CI/CD Security Remediation
Pervasive Vulnerabilities and Expanding Attack Surface
In the first six months of 2026, more than 21,500 CVEs were disclosed, an 18% increase over 2025, with projections nearing 50,000 for the full year. That pace adds roughly 130 new CVEs each day that require triage and mitigation, which manual remediation cannot match.
In 2025, 38% of reported CVEs were rated High or Critical severity. At least 161 CVEs were exploited in the first half of 2025, with some flaws weaponized within hours of disclosure. Security and platform teams need faster, more automated responses to keep exposure windows small.
Projections indicate that by the end of 2025, 45% of organizations will have experienced a software supply chain attack. CI/CD pipelines sit at the center of this risk as high-value assets for attackers.
Developer Productivity Loss and Context Switching
Developers spend hours reading scanner output, tracing failures through logs, and hand-writing fixes for security and policy issues. Each incident pulls them out of flow and delays merges.
Rapidly accelerating software development cycles create specific problems, including inadequate visibility and control within development for security teams and inconsistent security processes across teams. Teams often respond by expecting individual developers to become part-time security experts.
The Suggestion Engine Trap
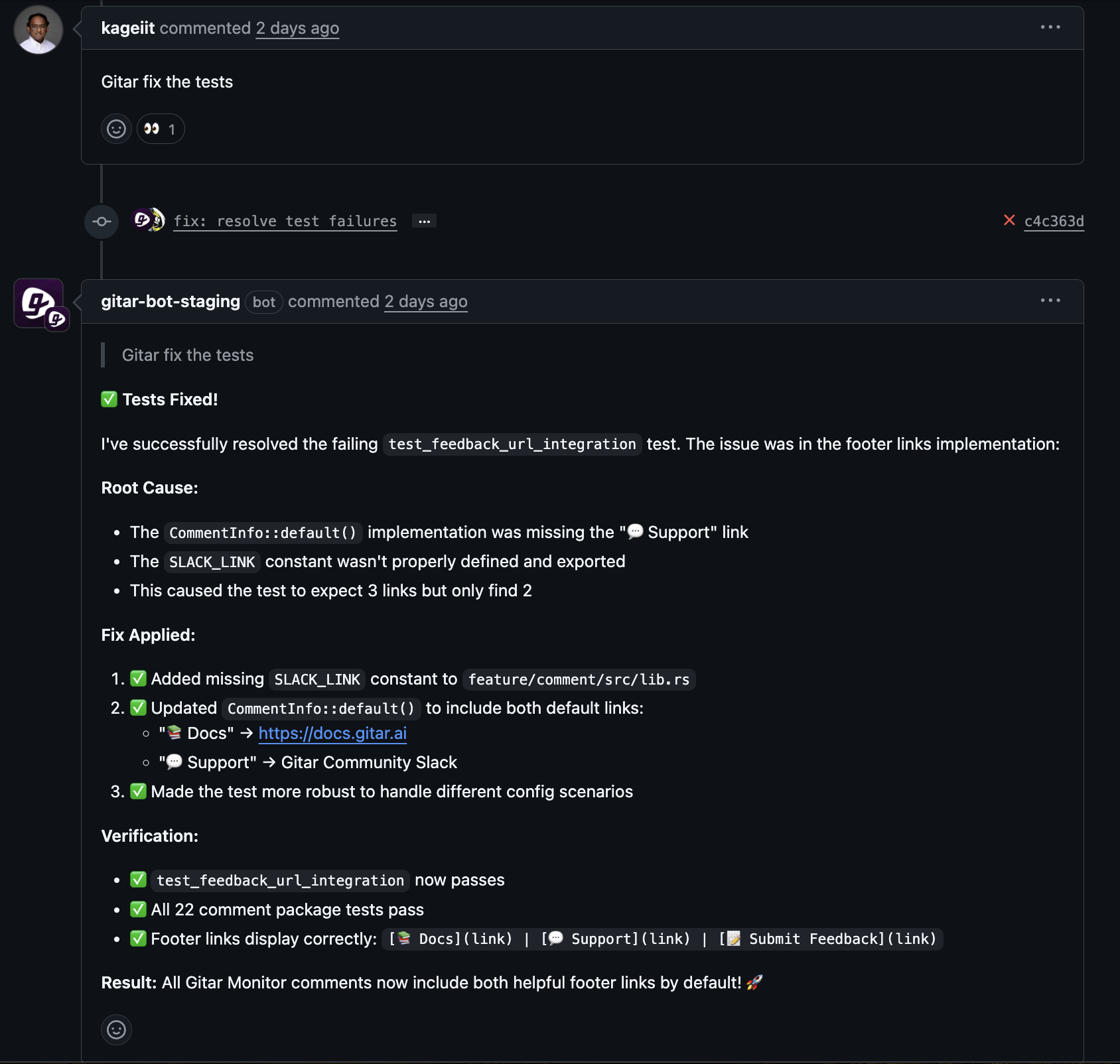
Most CI/CD security tools act as suggestion engines. They flag issues, attach a recommended change, and stop there. Developers still need to:
- Apply and adapt the fix in code or configuration
- Re-run the full CI pipeline
- Debug any new failures created by the change
This model shifts work rather than removing it. Teams still lack an engine that can take ownership of end-to-end remediation and validation.
Escalating Costs and Business Impact
A 20-developer team can lose close to seven figures in annual productivity to repetitive CI/CD security remediation. These hours represent delayed features, slower incident response, and longer feedback loops.
Cloud-based breaches now account for nearly 45% of incidents, and 27% of organizations report public cloud security breaches, at an average cost of about $4.4M per incident. When CI/CD pipelines become an entry point, the impact spreads across compliance, customer trust, and revenue.
Install Gitar to reduce manual CI/CD remediation and keep pipelines secure without slowing delivery.
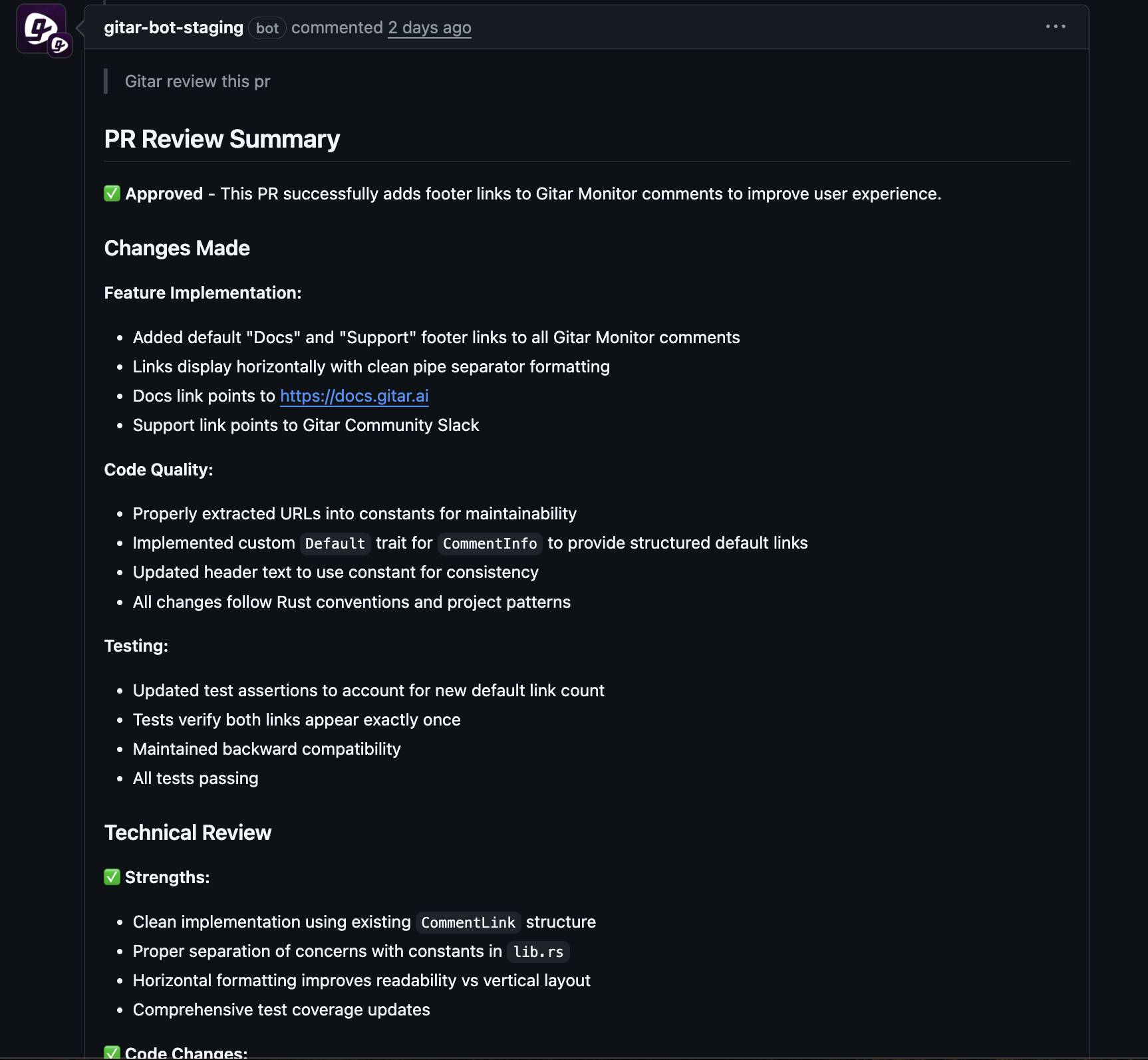
The Solution: Autonomous AI for CI/CD Security Remediation with Gitar
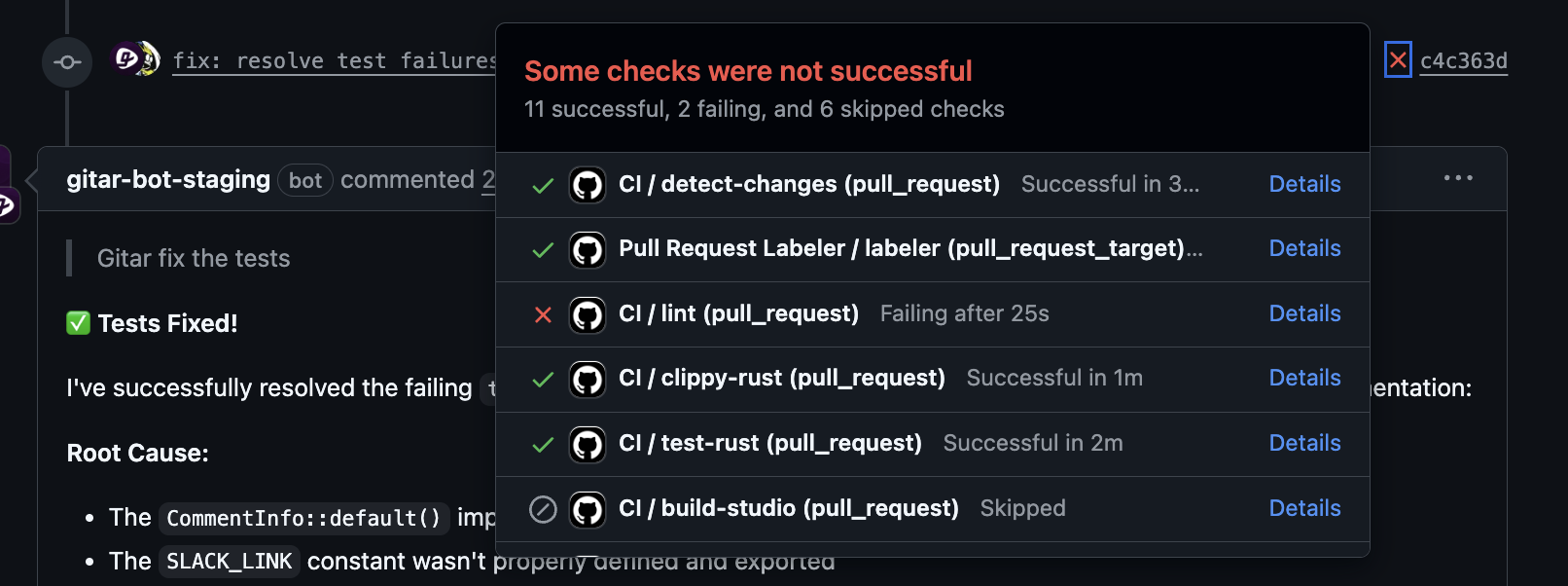
Gitar focuses on security healing instead of only security detection. Its autonomous AI agents understand failing CI runs, identify security or policy issues, apply targeted changes, and validate those updates against the real pipeline before committing.
Industry trends show a shift toward automated systems that fix failures, manage resources, and surface insights with less manual intervention. Gitar aligns with this direction by acting as a healing engine inside your CI/CD workflows.
Key Capabilities for Autonomous Security Healing
- End-to-end fixing that applies and validates security changes, then ensures all CI jobs pass before proposing or committing updates
- Environment replication that mirrors enterprise scan setups such as SonarQube, Snyk, and custom tooling so fixes align with real checks
- A configurable trust model that spans from suggested fixes requiring approval to fully automated commits with audit trails
- Support for common CI platforms such as GitHub Actions, GitLab CI, CircleCI, and BuildKite, along with integrated security scanners
- Context-aware intelligence that can draw on local developer agents and repository history for more accurate, minimal-impact fixes
Explore how Gitar can turn CI/CD security findings into automatic, validated fixes.
The Benefits of Autonomous CI/CD Security Remediation
Faster Time-to-Merge and Fewer Interruptions
Automated remediation removes a major reason for stalled pull requests. Developers stay focused on feature work while Gitar repairs issues that scanners or policies surface in CI.
Organizations facing rapid release cycles report visibility and consistency gaps for security teams across development. Autonomous fixing helps close those gaps without adding extra review steps for developers.
Lower Engineering Toil and Security Operations Cost
Replacing repetitive manual fixes with AI-driven remediation returns time to the team. Organizations can redirect that time toward roadmap work, platform improvements, or strategic security initiatives instead of chasing the same classes of issues across many repositories.
Reduced security toil also supports healthier on-call rotations and less burnout for senior engineers who currently handle complex CI failures.
Stronger Security Posture with Smaller Exposure Windows
Self-healing pipelines shorten the path from detection to validated fix. Issues can be addressed shortly after scanners identify them, often before developers open the CI logs.
The fact that at least 161 CVEs were exploited in the first half of 2025, with some attacks occurring within hours of disclosure, highlights the value of rapid, automated remediation. Faster fixes mean fewer opportunities for attackers to exploit known flaws.
Improved Developer Experience and Flow
Developers gain a more predictable workflow when CI issues resolve with minimal manual effort. Fewer context switches, fewer log-diving sessions, and clearer explanations of changes all contribute to a better day-to-day experience.
Over time, this consistency supports stronger retention and higher-quality code, since engineers can invest energy in design and implementation instead of repetitive remediation.
Comparison: Gitar as a CI/CD Security Healing Engine
This comparison summarizes how Gitar differs from suggestion-only tools and fully manual workflows.
|
Feature/Tool |
Gitar (Autonomous Healing) |
Traditional AI Reviewers (Suggestion Engines) |
Manual Remediation (Status Quo) |
|
Action Taken on Vulnerabilities |
Generates, applies, and validates fixes automatically |
Identifies issues and suggests fixes; requires manual implementation |
Manual identification, diagnosis, and fix implementation |
|
Developer Interaction |
Low, with optional no-touch or one-click acceptance |
High, with manual action needed for each suggestion |
Very high, with full manual investigation and coding |
|
Validation Against CI |
Built-in validation against the full CI pipeline |
Relies on developers to re-run CI after manual fixes |
Manual CI re-runs and debugging after each change |
|
Context Switching |
Reduced, which helps maintain developer focus |
High, with frequent interrupts for small fixes |
Very high, with constant shifting between coding and remediation |
Install Gitar to move from suggestion-only security tooling to validated, autonomous healing.
Implementation Considerations and Common Questions
Handling Complex CI/CD Environments with Multiple Scanners
Gitar replicates the full CI environment that runs in production pipelines, including SDK versions, security scanners such as SonarQube and Snyk, and custom scripts. This replication allows the AI agents to run the same checks locally, propose or apply fixes, and confirm that all security gates pass before changes reach your main branches.
Differences from AI Code Reviewers and Vulnerability Scanners
AI code reviewers and scanners focus on detection and suggestion. They highlight problems and sometimes propose a patch, but they do not own validation. Gitar takes responsibility for closing the loop by applying fixes, running the full CI workflow, and ensuring builds are green before submitting changes for human review, which removes the bulk of manual follow-up work.
Building Trust in Automated Security Fixes
Gitar uses configurable automation levels so teams can introduce it gradually. Many teams start with a mode where Gitar posts suggested changes as pull request comments or branches that require explicit approval. As teams gain confidence, they can enable more automation, such as auto-commits for low-risk classes of issues, while keeping full auditability and rollback options.
Conclusion: Moving CI/CD Security to Autonomous Healing
More than 21,500 CVEs were disclosed in the first half of 2025 alone, with many exploited shortly after disclosure. Manual remediation cannot keep up with this pace, especially when each fix requires developer attention, CI debugging, and coordination across teams.
Gitar offers a practical way to shift from detection-heavy CI/CD security to autonomous healing. Teams can cut repetitive toil, reduce exposure windows, and keep developers focused on feature work while maintaining or improving security standards.