Key Takeaways
- CI/CD pipelines now rank among the most valuable targets for attackers in 2026 because they hold broad access across code, infrastructure, and production systems.
- Credential leaks, misconfigurations, and software supply chain attacks frequently start inside CI/CD tooling, then spread across cloud accounts and downstream services.
- Security teams can reduce risk by tightening access controls, hardening pipelines, improving secret management, and validating artifacts throughout the software supply chain.
- Automated scanning and remediation in CI/CD reduce manual effort and help teams keep pace with both deployment volume and modern security threats.
- Gitar automatically fixes common CI/CD failures so teams ship more reliable software with less manual rework; get started at Gitar.
Why Traditional CI/CD Security Struggles With Modern Attacks
CI/CD pipelines need wide permissions to build, test, and deploy software, which makes them attractive entry points. Each new integration, token, or script increases the blast radius if something goes wrong.
CI/CD Pipelines as High-Value Targets
CI/CD pipelines now enable attackers to steal intellectual property, tamper with code, disrupt services, and escalate privileges across environments. Pipelines often operate with powerful roles that reach from source control to production, so one compromise can expose sensitive data and enable lateral movement.
The July 2025 AWS CodeBuild incident, CVE-2025-8217, showed how memory-dump attacks can inject malicious steps and exfiltrate CI secrets. That event highlighted how build systems themselves have become strategic supply chain targets.
Credential Leaks and Hardcoded Secrets
Most CI/CD failures start with accidental exposure rather than advanced exploits. Credential leaks in CI/CD often come from exposed API keys, SSH keys, tokens, and cloud secrets in workflows and configuration files. Once attackers obtain these secrets, they can access cloud accounts, data stores, and APIs without noisy intrusion attempts.
Supply Chain Attacks Through Pipelines
Gartner estimated that 45% of organizations would face software supply chain attacks by the end of 2025. These campaigns target dependencies, build tools, and package registries that CI/CD systems trust by default, which lets a single compromise reach many downstream users.
Misconfigurations and Privilege Escalation
OWASP NHI6:2025 calls out insecure CI/CD configurations that expose high-privilege access and enable supply chain attacks. Overly permissive IAM roles, flat networks, and weak controls around pipeline agents all increase exposure.
Late 2025 activity included rapid exploitation of critical CVEs, supply chain attacks via package managers, and chained privilege escalation in CI/CD systems. These trends show that pipelines often amplify the impact of underlying platform flaws.
Use Gitar for Autonomous CI/CD Pipeline Fixes
Traditional CI/CD management forces a tradeoff between throughput and reliability. Manual fixes slow teams down, yet skipping them allows flaky builds, broken tests, and insecure defaults to reach production.
Gitar addresses this problem with an autonomous agent that detects and fixes many CI/CD failures before they block your team. The system integrates with existing workflows, analyzes failed checks, and commits safe, context-aware changes back to the pull request.
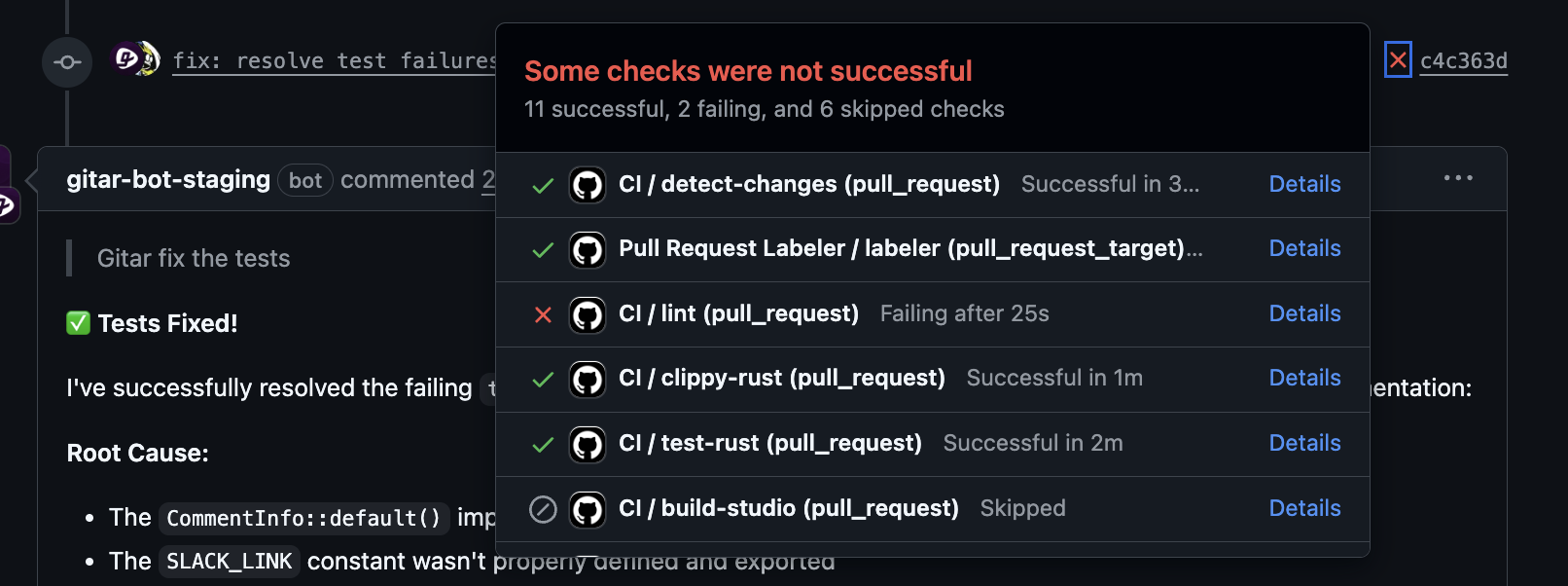
Self-Healing CI/CD Without Extra Friction
Gitar turns common CI/CD failures into routine, automated repairs. When linting, formatting, unit tests, or basic build steps fail, Gitar reviews logs, identifies the root cause, and applies a targeted code change. Teams keep their existing CI platforms while gaining a self-healing layer on top.
Gitar operates in multiple trust modes. Teams can start in suggestion-only mode, then move to auto-commit once they gain confidence in the agent’s fixes and review patterns.
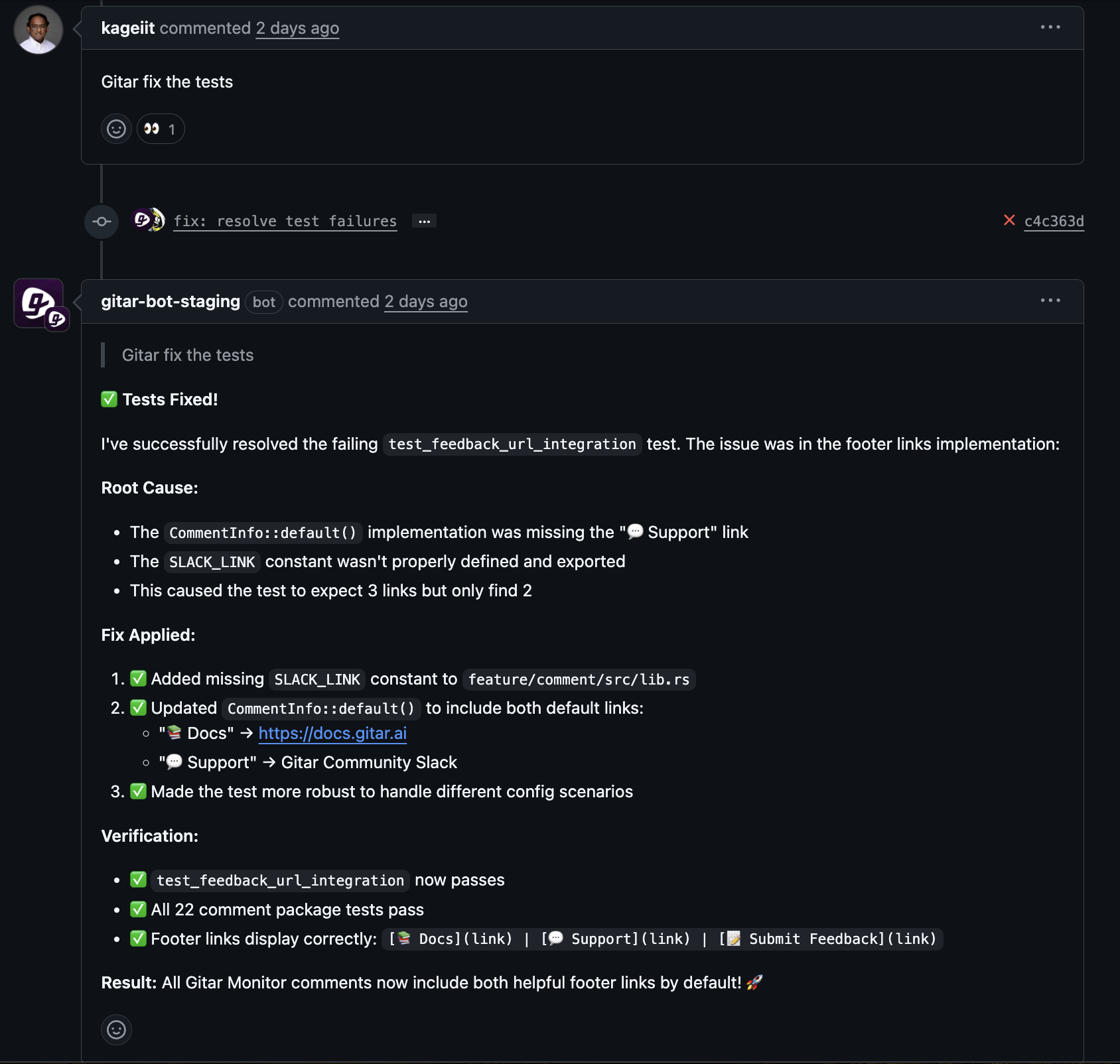
Reducing Context Switching for Developers
CI failures often appear long after a commit, which forces developers to drop current work and revisit an older change. That context switching hurts focus and slows delivery.
Gitar absorbs much of this burden by handling fixes in the background. Developers stay on their current tasks while Gitar repairs straightforward failures, updates the pull request, and documents what changed.
CI/CD Pipeline Security Best Practices for 2026
Security leaders can reduce CI/CD risk by tightening controls around secrets, dependencies, infrastructure, and pipeline behavior. These practices provide a practical baseline.
Protect Secrets and Credentials
- Store secrets in dedicated services such as HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault instead of in code or configuration files.
- Configure pipelines to fetch secrets only when required and avoid logging them in build output or artifacts.
- Run secret scanning at multiple stages, including pre-commit checks and repository-wide scans. Secret detection tools for exposed or hardcoded values now form a core part of CI/CD security.
- Rotate credentials frequently and favor short-lived tokens. Use OIDC for cloud workloads to reduce reliance on long-lived service account keys.
Secure the Software Supply Chain
- Monitor open source and third-party dependencies with software composition analysis and dependency review. Recommended mitigations include SCA, artifact verification, ephemeral runners, branch protection, and restricted workflow execution.
- Verify build artifacts using frameworks such as SLSA and Sigstore to confirm integrity and provenance before deployment.
- Pin dependencies and use lock files so builds stay reproducible while remaining auditable.
- Run builds on ephemeral runners that are destroyed after each job to reduce persistence of malicious changes and protect against poisoned pipeline execution attacks.
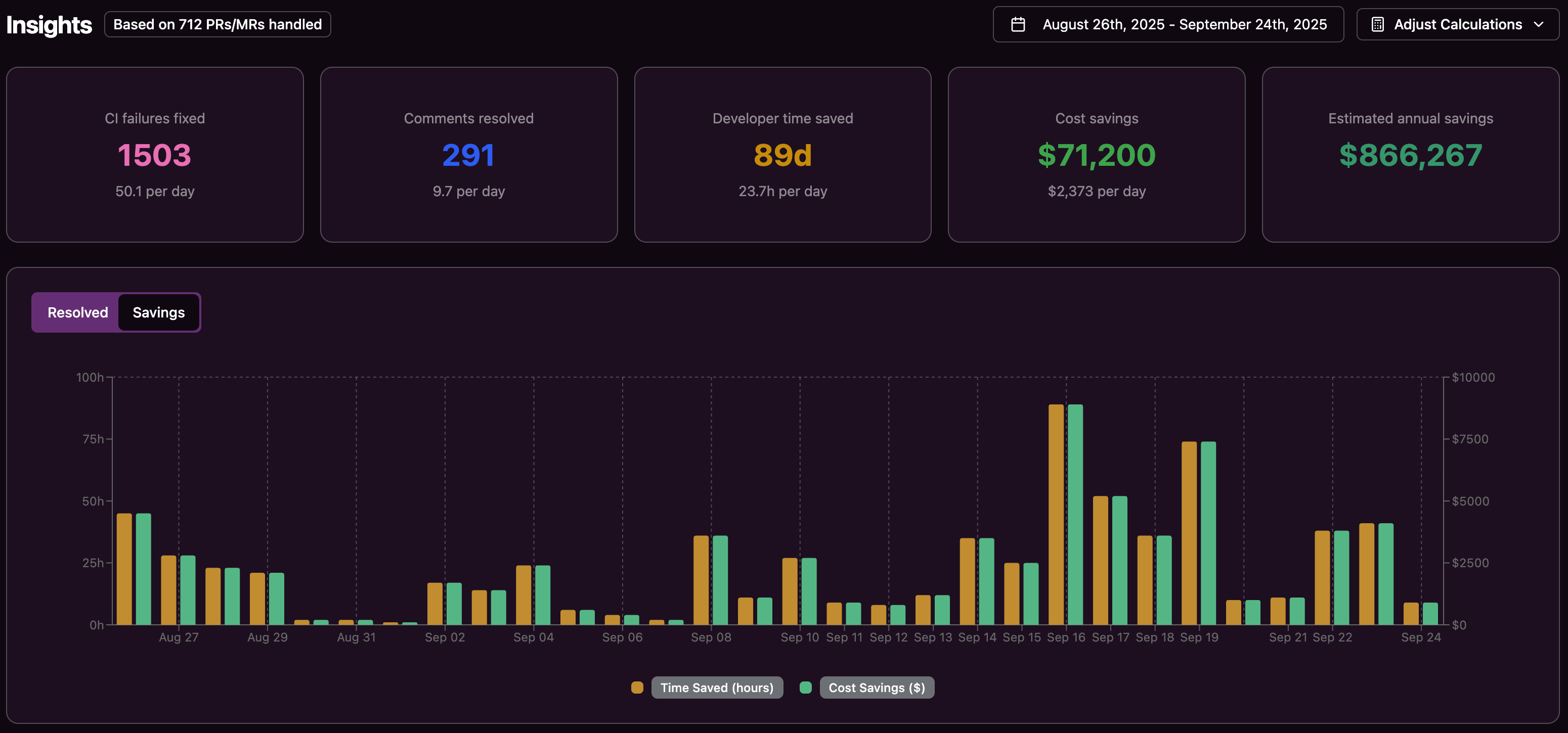
Apply Least Privilege and Strong Access Controls
- Segment environments so development pipelines cannot reach production data or resources by default.
- Use role-based access control to limit who can change pipeline definitions, approve deployments, or read sensitive logs.
- Protect main branches with review requirements and status checks that must pass before merges complete.
- Audit accounts and service identities on a regular schedule, then remove unused access and rotate credentials.
Automate Security Scanning and Remediation
- Integrate SAST, DAST, and IAST into CI jobs so every code change receives baseline security testing.
- Scan infrastructure as code to catch insecure cloud and network configurations before they deploy.
- Define vulnerability triage rules based on exploitability and business impact, then enforce clear time frames for fixes.
- Use automation, including tools like Gitar for CI reliability, to remediate straightforward failures quickly while reserving human effort for complex issues.
Harden Pipelines Against Tampering
- Guard build scripts and deployment definitions with signed commits and protected branches.
- Monitor pipeline runs for unusual activity such as unexpected outbound connections, new processes, or configuration changes.
- Centralize logging for CI/CD components and retain enough history to support incident investigations.
- Favor immutable infrastructure patterns so recovery means rebuilding from trusted definitions rather than patching compromised systems.
Manual CI/CD Fixes vs Gitar’s Autonomous Approach
|
Aspect |
Manual Approach |
Gitar |
|
Issue Detection |
Developers inspect logs and failures by hand |
Agent observes failed checks and identifies root causes |
|
Response Time |
Hours or days, depending on availability |
Near real-time remediation for supported failures |
|
Developer Impact |
Frequent context switches and delayed projects |
Fewer interruptions, since routine fixes happen automatically |
|
Consistency |
Varies by person and workload |
Standardized, repeatable resolution patterns |
Frequently Asked Questions
How does Gitar handle complex enterprise environments?
Gitar can mirror full enterprise CI workflows, including specific SDK versions, multi-language builds, and third-party tools. The agent applies fixes with awareness of these constraints so changes continue to pass existing checks. Organizations with strict security or data residency needs can deploy Gitar on premises to keep data within their own environment.
Can Gitar integrate with existing CI/CD tools and platforms?
Gitar connects to common CI/CD platforms and version control systems without replacing them. It supports languages such as Python, Go, JavaScript, TypeScript, Java, Rust, Docker, and Terraform. The agent layers on top of current pipelines to fix CI failures and respond to code review feedback, rather than introducing a new delivery stack.
Conclusion: Secure Pipelines and Maintain Velocity With Autonomous Fixes
Modern CI/CD pipelines sit at the center of software delivery and security risk in 2026. Misconfigurations, secret exposure, and supply chain weaknesses can all turn a single pipeline into a wide attack surface.
Teams that combine strong security practices with targeted automation reduce that risk while keeping release velocity high. Gitar supports this goal by fixing many common CI failures automatically so developers spend more time building features and less time chasing broken builds.
Install Gitar to keep CI/CD pipelines healthy and ship reliable software faster.