Key Takeaways
- Automated build failure detection reduces costly developer context switching and helps teams control the hidden productivity loss from CI issues.
- Manual debugging and basic AI suggestion tools still require significant human effort, while autonomous “healing” engines can complete the full fix-and-validate loop.
- Successful adoption depends on clear change management, measurable ROI tracking, and strong security and compliance safeguards.
- A phased rollout of automation, from suggestions to trusted auto-fixes, lets teams build confidence without disrupting existing workflows.
- Gitar offers an autonomous healing engine that fixes CI failures and applies code review feedback, helping engineering leaders reclaim time and budget, and you can get started at https://gitar.ai/fix.
The Strategic Imperative: Why Proactive Automated Build Failure Detection Matters
Automated build failure detection now plays a direct role in developer productivity and delivery speed. Cultural resistance and skill gaps still slow CI/CD adoption, while frequent pipeline failures force developers into unplanned work.
A 20-developer team that spends an hour per person per day on CI issues can lose around $1M per year in productivity. Failures often come from syntax errors, broken tests, or misconfigurations, and every failure triggers log digging, patching, and reruns. These interruptions break focus and delay releases.
Proactive, automated healing turns CI from a reactive firefight into a managed system. Teams that adopt autonomous remediation reduce interruption time, keep work in flow, and maintain more predictable delivery schedules.
Navigating the Landscape of Automated Build Failure Detection Solutions
Automated build failure detection solutions fall into three broad categories that offer different levels of autonomy and impact.
Traditional manual approaches rely on developers to inspect logs, trace root causes, and write fixes. This kind of systematic debugging demands expert time and does not scale well with larger codebases or distributed teams.
AI-driven suggestion engines analyze failures and propose fixes, but developers still review, edit, and validate changes. These tools reduce some toil yet leave the core context-switching problem in place.
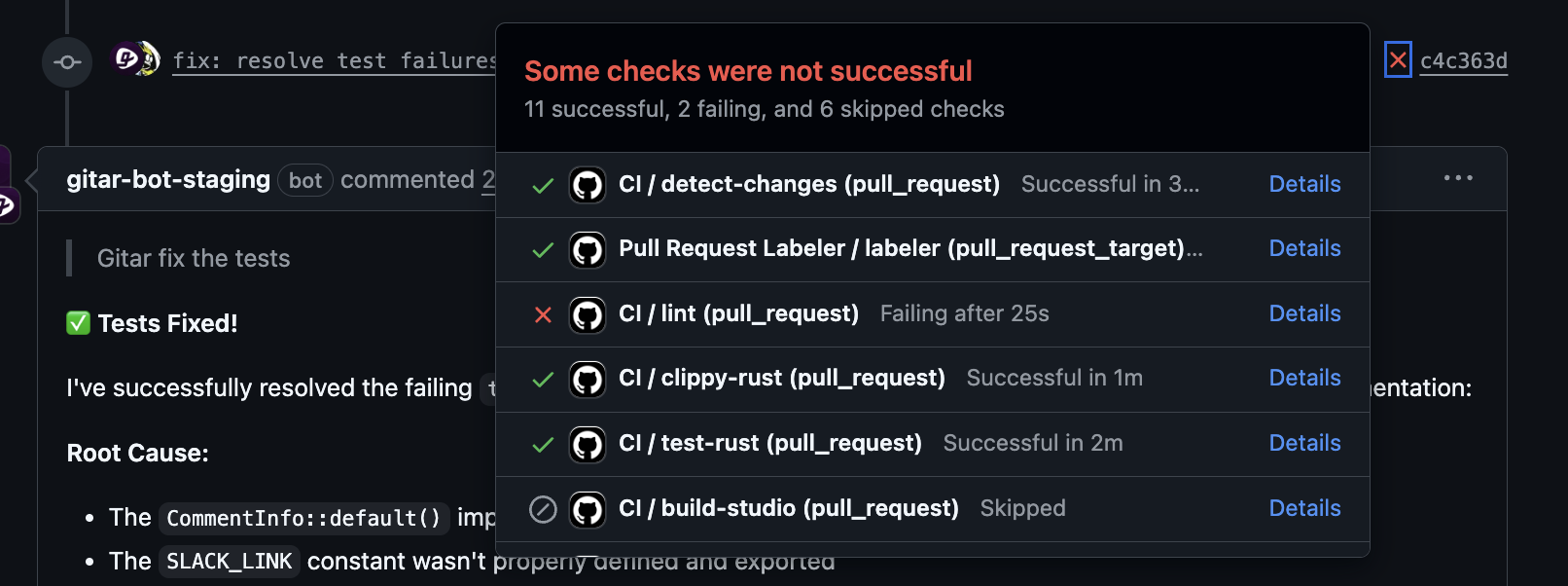
Healing engines such as Gitar aim to complete the loop. They detect failures, generate changes, apply them, and run CI again to confirm success. Common failure modes include test breaks, build errors, deployment issues, and dependency conflicts, and effective platforms handle this variety while respecting existing pipelines and standards.
How Gitar Improves Automated Build Failure Detection and Code Review
Gitar acts as an autonomous CI and code review agent that resolves failures and implements feedback inside your version control system. The platform focuses on closing the gap between detection and validated fixes.
Key capabilities of Gitar’s automated build failure detection
- End-to-end autonomous fixing: When CI checks fail, Gitar reads logs, identifies causes, proposes changes, applies them, and re-runs CI. It handles lint violations, test failures, build errors, and many dependency issues without requiring manual edits.
- Full environment awareness: Enterprise pipelines often involve multiple SDK versions, security scanners, and custom tools. Gitar emulates these workflows, including specific JDKs and integrations such as SonarQube and Snyk, so fixes match real production conditions.
- Configurable trust levels: Trust builds over time, so teams can start with suggestion-only mode and shift to auto-commit mode after they see consistent results. Rollback options remain available at each stage.
- Broad CI and VCS support: Gitar integrates with GitHub, GitLab, GitHub Actions, CircleCI, BuildKite, and other major systems, which simplifies adoption in mixed environments.
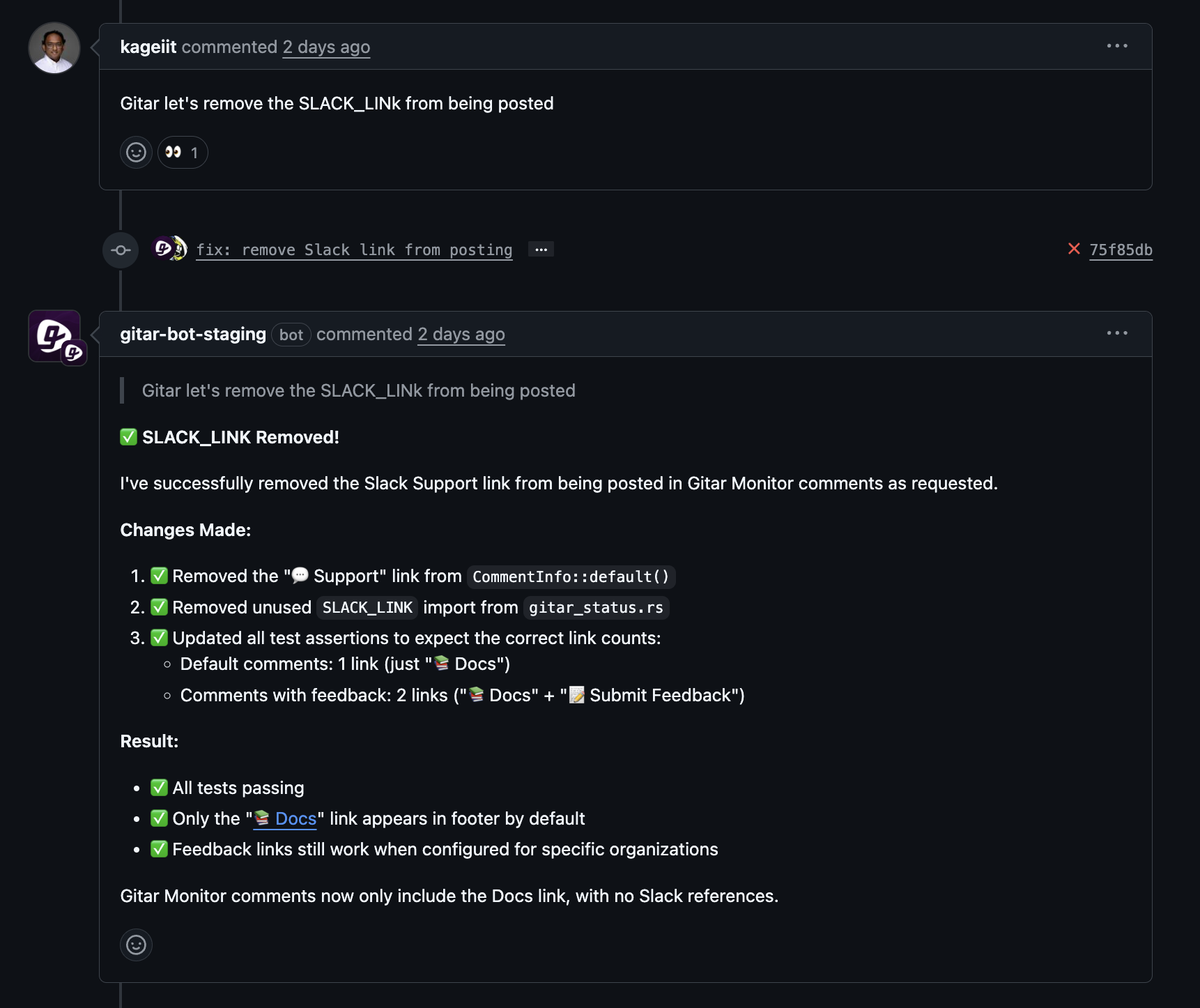
- Support for distributed teams: Reviewers can leave clear instructions at the end of their day, and Gitar applies the requested changes so the next contributor sees an updated pull request ready for review.
Strategic Considerations for Adopting Autonomous Automated Build Failure Detection
Build vs. buy decisions
Direct use of large language models, such as custom integrations with foundation models, can provide flexibility but often requires prompt design, tooling, and incident handling. Purpose-built platforms like Gitar package these capabilities into workflows that connect to CI, apply fixes, and manage safety checks, which reduces ongoing engineering and maintenance costs.
Organizational change management
Adoption succeeds when teams understand how automation fits into their workflow. Existing cultural resistance and skill gaps mean leaders benefit from a phased rollout, clear communication on review expectations, and defined escalation paths for complex failures that still need expert attention.
Measuring ROI and success metrics
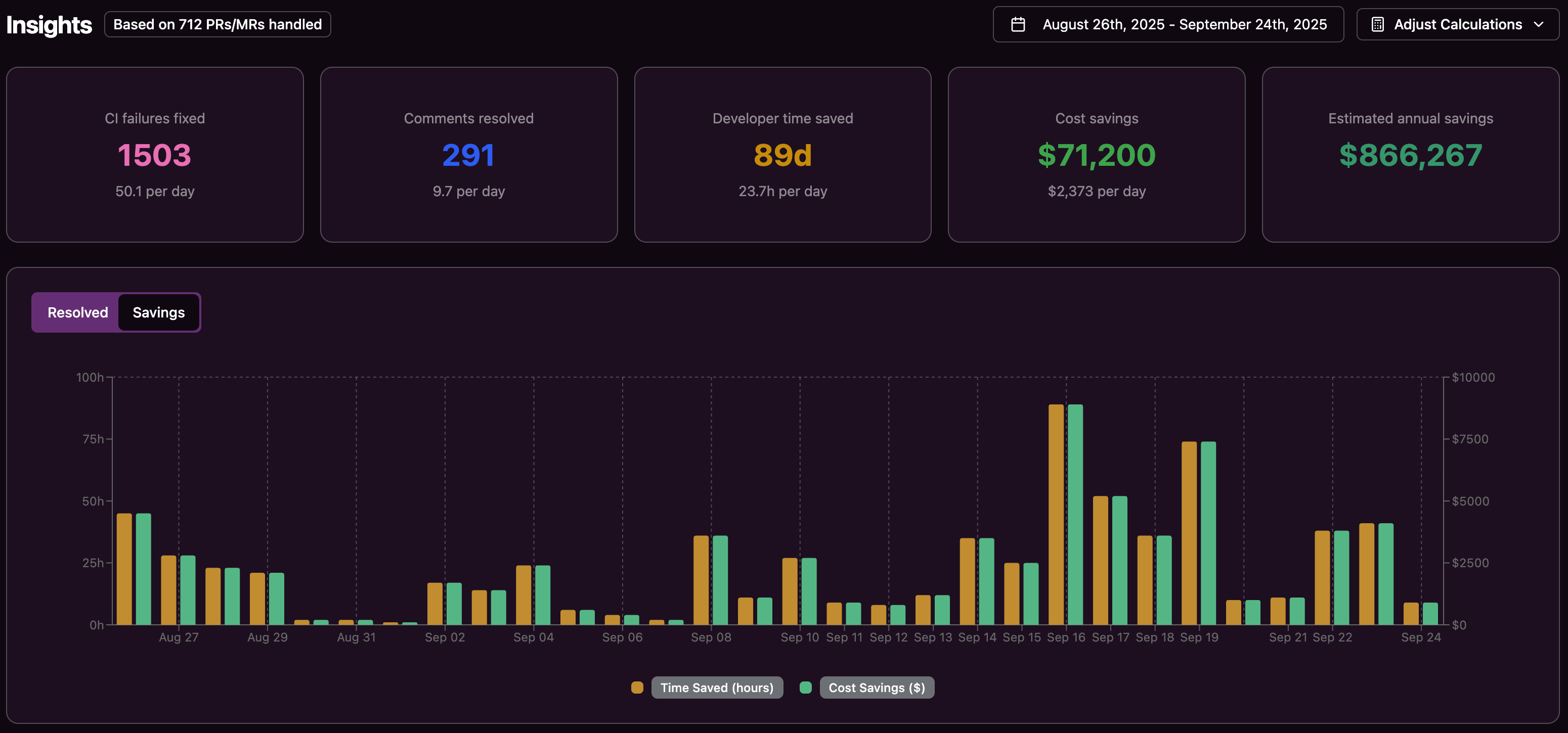
Return on investment becomes clearer with explicit baselines. If a 20-developer team spends around 5,000 hours per year on CI issues at a loaded cost of $200 per hour, automation that removes even half of that effort yields about $500K in annual savings. Improvements in DORA metrics such as lead time for changes and deployment frequency provide additional evidence of impact.
Security and compliance requirements
Security remains essential for any system with access to source code and CI. Compromised CI/CD systems can expose secrets and build infrastructure, so automated build failure detection must support strong access controls, audit trails, and clear visibility into every change it makes.
Teams that evaluate platforms like Gitar should confirm data handling policies, logging behavior, and rollback processes to align with internal compliance and regulatory needs.
Healing engines vs. suggestion engines at a glance
|
Feature |
Gitar (Healing Engine) |
AI Code Reviewers (Suggestion Engine) |
On-Demand AI Fixers (Manual Trigger) |
|
Primary action |
Applies and validates fixes automatically |
Provides suggestions and analysis |
Offers fixes when prompted |
|
CI integration depth |
Replicates full environment and targets green builds |
Performs limited validation, often partial context |
May lack full CI and environment awareness |
|
Autonomy level |
Configurable, from suggestions to auto-commit |
Typically requires manual implementation |
Depends on manual triggers and review |
Implementation Roadmap for Integrating Gitar
Phase 1: Installation and initial guardrails
Deployment starts by authorizing Gitar as a GitHub App on selected repositories and configuring scope in the web dashboard. Teams typically begin in suggestion-only mode so every change appears as a proposed fix that a developer can review and merge.
Phase 2: Trust-building and expansion
Confidence grows as developers see recurring issues, such as lint errors or simple test fixes, resolved automatically with clear, traceable commits. Once teams are comfortable with the quality of these changes, they can enable more aggressive modes that allow auto-commits for well-understood classes of failures.
Phase 3: Advanced workflows and code review support
Mature deployments treat Gitar as a collaborator for refactors and review feedback. Senior engineers can leave structured comments describing desired edits, and Gitar implements them, which speeds code review and reduces time zone friction for distributed teams.
Strategic Pitfalls to Avoid
Awareness of common pitfalls helps leaders design a smoother rollout of automated build failure detection.
- Limiting automation to suggestions: Teams that stop at recommendations keep most of the manual work in place. Full value comes when the system applies and validates fixes for defined scenarios.
- Overlooking organizational readiness: Automation that appears without explanation can create pushback. Clear communication, opt-in phases, and transparent logs make adoption easier.
- Underestimating CI complexity: Tools that cannot mirror real build environments can introduce flaky fixes and erode trust. Evaluations should include complex pipelines and multi-SDK projects.
- Focusing only on technical metrics: Build success rates matter, but the broader impact appears in reclaimed engineering time, faster releases, and reduced review load.
Frequently Asked Questions about Automated Build Failure Detection
How does Gitar handle a complex CI setup?
Gitar is designed for multi-language, multi-tool environments. It models your dependencies, SDK versions, and integrations such as SonarQube and Snyk so fixes respect your actual pipeline rather than a simplified sandbox.
What makes Gitar different from suggestion-only AI tools?
Gitar operates as a healing engine. It proposes changes, applies them in your repository, and re-runs CI to confirm that all required checks pass before surfacing a green pull request.
Can Gitar reduce time zone delays for distributed teams?
Gitar implements code review feedback based on reviewer comments, so teams in different regions can keep work moving overnight. Developers often start their day with updated pull requests already aligned with requested changes.
How can we control automation levels while we build trust?
Teams can configure Gitar to start with suggestion-only mode, then gradually enable auto-commits for specific failure types. Every change remains visible in version control with full history, which helps maintain oversight.
How does Gitar support security and compliance?
Gitar maintains detailed logs of actions, supports fine-grained access controls, and preserves rollback options for every change. These features help security and compliance teams review activity and align the platform with internal policies.
Conclusion: Accelerate Delivery with Autonomous Healing
Automated build failure detection has moved from a convenience to a core capability for modern engineering teams. Organizations that adopt autonomous healing gain more predictable delivery, reduce unplanned work, and give developers more time for design and feature work.
Gitar helps teams reach this state by closing the loop from failure detection to validated fix, across both CI and code review. Engineering leaders who invest early in this approach set their teams up for faster iteration and more sustainable productivity in 2026 and beyond.
To see how autonomous fixes can fit into your own pipelines, install Gitar and start automating broken build resolution at https://gitar.ai/fix.